
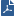

vSEC Controller integrates the Microsoft Azure cloud with Check Point security. The Check Point Data Center Server connects to the Microsoft Azure cloud and retrieves object data. vSEC Controller updates IP addresses and other object properties in the Data Center Objects group.
You must authenticate and connect to your Microsoft Azure account to pull objects. You can use Service Principal Authentication or Microsoft Azure Active Directory User Authentication.
You can create the Service Principal with the Azure portal, Azure Powershell and the Azure CLI.
The minimum recommended permission is Reader. You can assign Reader permission to:
Note - If you have less permissions, some of the functionality might not work.
To connect to the Microsoft Azure Data Center Server:
Note - All changes in Microsoft Azure are updated automatically with the Check Point security policy. Users with permissions to change Resource Tags in Microsoft Azure may be able to change their access permissions.
Imported Properties |
Description |
|---|---|
Name |
Name of the object and of the object Resource Group. Format is: obj_name (obj_resource_group_name) The user can edit the name after importing the object. |
Name in server |
Name of the object and of the object Resource Group. Format is: obj_name (obj_resource_group_name) |
Type in server |
Object type. |
IP address |
Virtual Machines or VMSS IP addresses. In the case of subnets, NSGs or Tags, the field contains a list of all the IPs in the container. |
Note |
Contains the address prefixes for VNETs and subnets. |
URI |
Object path. |
Tags |
Keys and Values attached to the Object. |
Location |
Physical location in Microsoft Azure. |
The Microsoft Azure Auto Scaling service with the Check Point Auto Scaling group can increase or decrease the number of vSEC Gateways according to the current load.
vSEC Controller for Microsoft Azure can work with the Check Point Auto Scaling Group. The Check Point Security Management Server can update Data Center objects automatically on the Check Point Auto Scaling group.
Enable the Identity Awareness Blade as explained in Auto Scaling in Microsoft Azure, sk115533, Section 6-A - Enabling additional Software Blades.