

Inspection Settings add more than 80 protections and VoIP settings. It protects against malicious attacks by:
As part of Inspection Settings, VoIP protections can be:
With Inspection Settings you can:
For example, if you add an exception that allows non-RFC compliant SIP traffic on a specified VoIP server, security is not compromised for all other VoIP traffic.
Inspection Settings can be configured for each profile and can be:
To configure Inspection Settings:
The Inspection Settings window opens.
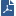
In the Settings column, SCCP Inspection Settings shows.
Double-click the service you want to configure. A window opens.
Specific VoIP services can be blocked if the services:
To configure Application Policy:
The Inspection Settings window opens.
A list of Settings options shows.
A protocol anomaly is a field name or value in the protocol header that is RFC compliant, but deviates from usual use.
For example, the presentation of a field value which contains hundreds of characters, where normally, fewer than ten characters is usual. This is an anomaly.
If a protocol anomaly is found in the VoIP packet, this is a good indication that the VoIP network is being attacked.
To configure Protocol Anomaly Protection:
The Inspection Settings window opens.
To configure Engine Settings:
The Inspection Settings window opens.
The SCCP - General Settings window opens.
Field
A gateway dynamically opens ports for VoIP media channel, based on the information in the SCCP signaling connection. When you select this option, it prevents the opening of SCCP media channels. Do not select this option if a SCCP media channel passes through the gateway.