
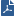

Description Confirms these operations were successful:
CPRID connection.Syntax:
|
Parameter |
Description |
|---|---|
|
Object name of the Check Point Security Gateway defined in SmartConsole. |
|
Package vendor. For example, |
|
Package name. Options are: |
|
Package version |
|
Package minor version. This parameter is optional. |
Example:
Successful - Verify succeeds
|
Unsuccessful - Verify fails
|
Description Starts or stops all Check Point processes and applications.
Syntax:
> cpstart / cpstop
Note - This command cannot be used to start cprid. cprid is invoked when the machine is booted and it runs independently.
Description
Shows Check Point statistics for applications.
Syntax
cpstat [-p <port>] [-s <SICname>] [-f <flavor>] [-o <polling>] [-c <count>] [-e <period>] [-x] [-j] [-d] application_flag <flag>
Parameters
Parameter |
Description |
|---|---|
|
Port number of the server. The default is the standard server port (18192). |
|
Secure Internal Communication (SIC) name of the server. |
|
The flavor of the output (as it appears in the configuration file). The default is the first flavor found in the configuration file. |
|
Polling interval (seconds) specifies the pace of the results. The default is 0, meaning the results are shown only once. |
|
Specifies how many times the results are shown. The default is 0, meaning the results are repeatedly shown. |
|
Specifies the interval (seconds) over which 'statistical' olds are computed. Ignored for regular olds. |
|
XML output mode |
|
Json output mode |
|
Debug mode. |
<flag> |
One of these applications is displayed: One of the following:
|
Return Value
0 on success, 1 on failure
Example
cpstat -c 3 -o 3 fw
Output
Success shows OK. Failure shows an appropriate error message.
The following flavors can be added to the application flags:
fw — "default", "interfaces", "all", "policy", "perf", "hmem", "kmem", "inspect", "cookies", "chains", "fragments", "totals", "ufp", "http", "ftp", "telnet", "rlogin", "smtp", "pop3", "sync"vpn — "default", "product", "IKE", "ipsec", "traffic", "compression", "accelerator", "nic", "statistics", "watermarks", "all"fg — "all"ha — "default", "all"os — "default", "ifconfig", "routing", "memory", "old_memory", "cpu", "disk", "perf", "multi_cpu", "multi_disk", "all", "average_cpu", "average_memory", "statistics"mg — "default"persistency — "product", "Tableconfig", "SourceConfig"polsrv — "default", "all"uas — "default"svr — "default"cpsemd — "default"cpsead — "default"asm — "default", "WS"ls — "default"ca — "default", "crl", "cert", user", "all"Description Edits the objects file on the Security Management Server (see skI3301). Editing the objects.C file on the gateway is not required or desirable, since it will be overwritten the next time a policy is installed.
Important - Do NOT run this command unless explicitly instructed by Check Point Support or R&D to do so. Otherwise, you can corrupt settings in the management database.
Syntax
> dbedit [-s <server>] [- u <user>|-c <certificate>] [-p <password>] [-f <filename>] [-r <db-open-reason>] [-help]
Parameter |
Description |
|---|---|
|
The Security Management Server on which the |
|
The user's name (the name used for the SmartConsole) or the full path to the certificate file. |
|
The user's password (the password used for the SmartConsole). |
|
The name of the file containing the commands. If |
|
A non-mandatory flag used to open the database with a string that states the reason. This reason will be attached to audit logs on database operations. |
|
Print usage and short explanation. |
dbedit internal commands:
Parameter |
Description |
|---|---|
create [object_type] [object_name] |
Create an object with its default values. |
modify [table_name] [object_name] [field_name] [value] |
Modify fields of an object which is:
Extended formats for owned objects can be used: For example, |
update [table_name] [object_name] |
Update the database with the object. This command will check the object validity and will issue an error message if appropriate. |
delete [table_name] [object_name] |
Delete an object from the database and from the client implicit database. |
addelement [table_name] [object_name] [field_name] [value] |
Add an element (of type string) to a multiple field. |
rmelement [table_name] [object_name] [field_name] [value] |
Remove an element (of type string) from a multiple field.
|
rename [table_name][object_name] |
Assign a new name for a given object. The operation also performs an update. Example: Rename network object London to Chicago.
|
quit |
Quit |
Example:
Replace the owned object with a new null object, where NULL is a reserved word specifying a null object:
|
Example:
Extended Format
firewall_properties owns the object floodgate_preferences
floodgate_preferences has a Boolean attribute turn_on_logging, which will be set to true
|
comments is a field of the owned object contained in the ordered container. The 0 value indicates the first element in the container (zero based index).
|
Replace the owned object with a new one with its default values.
|
Manages dynamic objects on the appliance. The dynamic_objects command specifies an IP address to which the dynamic object is resolved.
First, define the dynamic object in the SmartConsole. Then create the same object with the CLI (-n argument). After the new object is created on the gateway with the CLI, you can use the dynamic_objects command to specify an IP address for the object.
Any change you make to dynamic objects' ranges are applied immediately to the objects. It is not necessary to reinstall the policy.
Description
Manages dynamic objects on the appliance.
Syntax
dynamic_objects -o <object> [-r <fromIP> <toIP> ...] [-a] [-d] [-l] [-n <object> ] [-c] [-do <object>]
Parameters
Parameter |
Description |
|---|---|
|
Name of the dynamic object that is being configured. |
|
Defines the range of IP addresses that are being configured for this object. |
|
Adds range of IP addresses to the dynamic object. |
|
Deletes range of IP addresses from the dynamic object. |
|
Lists dynamic objects that are used on the appliance. |
|
Creates a new dynamic object. |
|
Compare the objects in the dynamic objects file and in objects. |
|
Deletes the dynamic object. |
<object> |
Name of dynamic object. |
<fromIP> |
Starting IPv4 address. |
<toIP> |
Ending IPv4 address. |
Example
dynamic_objects -n sg80gw -r 190.160.1.1 190.160.1.40 -a
Output
Success shows Operation completed successfully. Failure shows an appropriate error message.
Description Creates a new active log file. The current active log file is closed and renamed by default $FWDIR/log/<current_time_stamp>.log unless you define an alternative name that is unique. The format of the default name <current_time_stamp>.log is YYYY-MM-DD_HHMMSS.log. For example, 2003-03-26_041200.log
Warning:
$FWDIR/log/current_time_stamp.logThe new log file that is created is given the default name $FWDIR/log/fw.log. Old log files are located in the same directory.
A Security Management Server can use fw logswitch to change a log file on a remote machine and transfer the log file to the Security Management Server. This same operation can be performed for a remote machine using fw lslogs and fw fetchlogs
When a log file is sent to the Security Management Server, the data is compressed.
Syntax
> fw logswitch [-audit] [<filename>] > fw logswitch -h <host> [+|-][<filename>]
Parameter |
Description |
|---|---|
|
Logswitch for the Security Management Server audit file is done. This is relevant for local activation. |
|
The name of the file to which the log is saved. If no name is specified, a default name is provided. |
|
The resolvable name or IP address of the remote machine (running either a Security Gateway or <to_sms>) on which the log file is located. The Security Management Server (on which the |
|
Change a remote log and copy it to the local machine. |
|
Change a remote log and move it to the local machine thereby deleting the log from the remote machine. |
Note - Files are created in the $FWDIR/log directory on both the host and the Security Management Server when the + or - parameters are specified. Note that if - is specified, the log file on the host is deleted rather than renamed.
host specified:
filename specified - On host, the old log file is renamed to old_log. On the Security Management Server, the copied file will have the same name, prefixed by hosts name. For example, the command fw logswitch -h venus +xyz creates a file named venus_xyz.log on the Security Management Server.filename not specified - On host, the new name is the current date. For example, 2003-03-26_041200.log.
On the Security Management Server, the copied file will have the same name, but prefixed by host_. For example, target_2003-03-26_041200.log.
host not specified:
filename specified - On the Security Management Server, the old log file is renamed to old_logfilename not specified - On the Security Management Server, the old log file is renamed to the current date.Compression
When log files are transmitted from one machine to another, they are compressed using the zlib package, a standard package used in the Unix gzip command (see RFC 1950 to RFC 1952 for details). The algorithm is a variation of LZ77 method.
The compression ratio varies with the content of the log records and is difficult to predict. Binary data are not compressed, but string data such as user names and URLs are compressed.
Description Performs management operations on the Security Gateway. fwm controls fwd and all Check Point daemons.
Syntax
> fwm
Description Modifies the expiration date of all users and administrators.
Syntax
> fw expdate dd-mmm-20xx
Comments The date can be modified using a filter.
Example fw expdate 02-mar-20xx -f 01-mar-20xx
Description Downloads the user database and network objects information to selected targets. If no target is specified, then the database is downloaded to localhost
Syntax
gw> fwm dbload [-a|-c <conffile>] [<targets>]
Parameter |
Description |
|---|---|
|
Executes commands on all targets specified in the default system configuration file, |
|
Only OPSEC control connections in the file are enabled. |
|
Executes commands on the designated targets. |
Description Encrypts the password of a SecuRemote user using IKE. The resulting string must then be stored in the LDAP database.
Syntax
> fwm ikecrypt <shared-secret> <user-password>
Parameter |
Description |
|---|---|
|
The IKE Key is defined in the Encryption tab of the LDAP Account Unit Properties window. |
|
The password for the SecuRemote user. |
Note - An internal CA must be created before implementing IKE encryption. An Internal CA is created during the initial configuration of the Security Management Server, following installation.
Description Fetches the packet capture.
Syntax > fwm getpcap -g <gw> -u <cap id> [-p <path>] [-c <domain>]
Parameter |
Description |
|---|---|
|
Host name of the gateway. |
|
Captures UID. |
|
Outputs pathname. |
|
Host name of the Domain Management Server. |
Description Exports the log file to an ASCII file.
Syntax > fwm logexport [-d <delimiter>] [-i <filename>] [-o <outputfile>] [-n] [-p] [-f] [-m {initial|semi|raw}] [-a]
Parameter |
Description |
|---|---|
|
Sets the output delimiter. The default is a semicolon ( |
|
The name of the input log file. The default is the active log file, |
|
The name of the output file. The default prints to the screen. |
|
Does not perform DNS resolution of the IP addresses in the log file (this option significantly speeds the processing). |
|
Does not perform service resolution. A service port number is displayed. |
|
If this is the active log file, |
|
This flag specifies the unification mode.
|
|
Shows account records only. The default is to show all records. |
Use logexport.ini to control the output of fwm logexport. Put the logexport.ini file in the conf directory $FWDIR/conf
The logexport.ini file should be in the following format:
[Fields_Info] included_fields = field1,field2,field3,<REST_OF_FIELDS>,field100 excluded_fields = field10,field11 |
Notes:
num field will always appear first and cannot be manipulated using logexport.ini<REST_OF_FIELDS> is a reserved token that refers to a list of fields. It is optional. -f is set, <REST_OF_FIELDS> is based on a list of fields taken from the file logexport_default.C-f is not set, <REST_OF_FIELDS> is based on the given input log file. included_fields and excluded_fieldsFormat:
The fwm logexport output appears in tabular format. The first row lists the names of all fields included in the next records. Each of the next rows consist of a single log record whose fields are sorted in the same order as the first row. If a record has no information on a specific field, this field remains empty (as indicated by two successive semi-colons).
Example:
|
Description Shows the build number.
Syntax > fwm ver [-f <filename>]
Parameter |
Description |
|---|---|
|
Exports the build number data to a file. |
Description Verifies the specified policy package without installing it.
Syntax > fwm verify <policy>
Parameter |
Description |
|---|---|
|
The name of an available policy package. |
Description Notifies an Internet Service Provider (ISP) when a company's corporate network is under attack. The inet_alert utility forwards log messages generated by the alert daemon to an external Management Station. This is usually located at the ISP site. The ISP can then analyze the alert and react accordingly.
inet_alert uses the ELA Protocol to send the alert. The Management Station receiving the alert must be running the ELA Proxy.
If communication with the ELA Proxy is to be authenticated or encrypted, a key exchange must be performed between the Management Station running the ELA Proxy and the Security Gateway generating the alert.
To use this utility, enter it into a script:
tab > Global Properties > Log and Alert > Alert early versions compatibility > run 4.x alert script.Syntax
# inet_alert -s <ipaddr> [-o] [-a <auth_type>] [-p <port>] [-f <token value>] [-m <alerttype>]
Parameter |
Description |
|---|---|
|
The IP address, in dot format, of the ELA Proxy to be contacted. |
|
Print the alert log received by |
|
The type of connection to the ELA Proxy. One of the following values:
|
|
The ELA proxy port number. Default is 18187. |
|
A field to be added to the log, represented by a
This option can be used multiple times to add multiple |
|
The alert to be triggered at the ISP site. This alert overrides the alert specified in the log message generated by the alert daemon. The response to the alert is handled according to the actions specified in the ISP Security Policy: The following alerts execute the OS commands.
The following NetQuota and ServerQuota alerts execute the OS commands specified in:
You can configure the alert in the Manage & Settings |
Return Value
Exit status |
Description |
|---|---|
|
Execution was successful. |
|
Undetermined error. |
|
Unable to allocate memory. |
|
Unable to obtain log information from |
|
Invalid command line arguments. |
|
Failed to invoke the OPSEC API. |
Example
# inet_alert -s 10.0.2.4 -a clear -f product cads -m alert
This command specifies that in the event of an attack, inet_alert should take the following actions:
cads Description Manages processes running on the Security Gateway collectively or individually and includes the following:
Cache operations, such as emptying the cache, as well as providing debug information.
Finds statistics such as:
View the alert and warning log regarding debug.
Syntax
# ldapcmd -p {<process_name>|all} <command> [-d debug_level] [command_arg]
Parameter |
Description |
|---|---|
|
Runs a specified process or all processes. |
|
Valid values for the
|
|
Specifies whether or not to create LDAP logs. |
Description Performs compare queries. Prints a message whether the result returned a match or not. ldapcompare opens a connection to an LDAP directory server, and binds and performs the comparison specified on the command line or from a specified file.
Syntax
# ldapcompare -d [<options>] dn <attribute> <value>
Parameter |
Description |
|---|---|
|
Debug flag. |
|
See below. |
|
The DN object. |
|
The attribute of the DN object. |
|
The value of the attribute of the DN object. |
The ldapcompare options:
-u - Include user-friendly entry names in the output.-d <level> - Set LDAP debugging level to level-F sep - Print sep instead of = between attribute names and values.-f <file> - Perform sequence of compares listed in file-D <binddn> - Bind DN.-w <passwd> - Bind password (for simple authentication).-h <host> - LDAP server.-p <port> - Port on the LDAP server.-T <timeout> - Client side timeout for all operations (in milliseconds).-l <time limit> - Server side time limit (in seconds) for compare.-z <size limit> - Server side size limit (in entries) for compare.Description A utility program to port from Member Mode to MemberOf Mode. This is done by searching all specified group/template entries and fetching their Member attribute values.
Each value is the DN of a member entry. The entry identified by this DN is added to the MemberOf attribute value of the group/template DN at hand. In addition, those Member attribute values will be deleted from the group/template unless Both Mode is specified.
When your run the program, a log file, ldapconvert.log is generated in the current directory. It logs all modifications done and errors encountered.
Syntax
> ldapconvert -d -h <host> -p <port> -D user_DN -w <secret> [-g group_DN | -f <file>] -m mem_attr -o memberof_attr –c memberobjectclass[<extra options>]
Parameter |
Description |
|---|---|
|
Debug flag. |
|
LDAP server IP address. |
|
LDAP server port number. |
|
LDAP bind DN. |
|
LDAP bind password. |
|
Group or template DN to perform the conversion on. May appear multiple times for multiple entries. |
|
File containing a list of group DNs each separated by a new line. |
|
LDAP attribute name when fetching and (possibly) deleting a |
|
LDAP attribute name when adding |
|
LDAP |
|
See below. |
The ldapconvert extra options are as follows:
-M - Maximum number of member LDAP updated simultaneously. Default is 20.-B - Convert to Both Mode.-p <port> -LDAP port. Default is 389.-T <timeout> -Client side timeout for LDAP operations, in milliseconds. Default is never-l <time limit> -Server side time limit for LDAP operations, in seconds. Default is never-s -Server side size limit for LDAP operations in entries. Default is none-z -Use SSL.Note - We recommend you make a backup of the LDAP server before running the conversion program in case unrecoverable errors are encountered.
There are two GroupMembership modes. You must keep these modes consistent.
For example, if you apply conversion on LDAP users to include MemberOf attributes for their groups, then this conversion has to be applied on LDAP defined templates for their groups.
Symptom:
A command runs with the option –M fail. The program stops with an error message stating the connection stopped unexpectedly.
Solution:
The LDAP server could not handle that many LDAP requests simultaneously and closed the connection.
Run the program again with a lower value for the –M option. The default value should be adequate but can also cause a connection failure in extreme situations. Continue to reduce the value until the program exits normally. Each time you run the program with the same set of groups the program will pick up where it left off.
Example 1:
A group is defined with the DN: cn=cpGroup,ou=groups, ou=cp, c=il and the following attributes:
... cn=cpGroup uniquemember="cn=member1,ou=people, ou=cp,c=il" uniquemember=" cn=member2, ou=people, ou=cp,c=il" ... |
For the two member entries:
... cn=member1 objectclass=fw1Person ... |
and:
... cn=member2 objectclass=fw1Person ... |
Run: ldapconvert with the following arguments:
ldapconvert -g cn=cpGroup,ou=groups, ou=cp, c=il -h myhost -d cn=admin -w secret |
The result for the group DN will be as follows:
... cn=cpGroup ... |
The result for the two member entries will be as follows:
... cn=member1 objectclass=fw1Person memberof="cn=cpGroup,ou=groups, ou=cp, c=il" ... |
and:
... cn=member2 objectclass=fw1Person memberof=" cn=cpGroup,ou=groups, ou=cp, c=il" ... |
If you run the same command with the –B options, it will produce the same result but the group entry will not be modified.
Example 2:
If there is another member attribute value for the same group entry:
uniquemember="cn=template1,ou=people, ou=cp,c=il" |
and the template is:
cn=member1 objectclass=fw1Template |
After running the same command line the template entry will stay intact because the command line specified the option –c fw1Person, but the object class of template1 is fw1Template
|
|
Description Imports users to an LDAP server. The input file must be in the LDIF format.
Syntax
# ldapmodify -a -c -d -h <host> -p <port> -D <LDAPadminDN> -p <LDAPadminPassword> -f <exportfilename>.ldif -d
Parameter |
Description |
|---|---|
|
Adds users. |
|
Continue on errors. |
|
LDAP server IP address. |
|
Debug flag. |
|
LDAP server port number. |
|
LDAP administrator DN. |
|
LDAP administrator password. |
|
Specifies the name of the input file. This file must be in the LDIF format. |
Before importing, prepare the LDAP directory as follows:
ldapmodify command:ldapmodify -a -h <host> -p <port> -D <LDAPadminDN> -w <LDAPadminPassword> objectclass: organization o:myOrg |
Description Queries an LDAP directory and returns the results.
Syntax
ldapsearch [options] filter [attributes] -d
Parameter |
Description |
|---|---|
|
See the |
|
RFC-1558 compliant LDAP search filter. For example, |
|
The list of attributes to be retrieved. If no attributes are given, all attributes are retrieved. |
|
Debug flag. |
The following are the attributes for options:
-A -Retrieve attribute names only, without values.-B -Do not suppress printing of non-ASCII values.-D bindDN -The DN to be used for binding to the LDAP server.-F separator -Print separator between attribute name and value instead of =-h host -The LDAP server identified by IP address or resolvable name.-l timelimit -The server side time limit for search, in seconds.-p portnum -The port number. The default is standard LDAP port 389.-S attribute -Sort the results by the values of attribute-s scope -One of the following: base, one, sub-b -Base distinguished name (DN) for search.-t -Write values to files in /tmp. Each attribute-value pair is written to a separate file, named: /tmp/ldapsearch-<attribute>-<value>.For example, for the fw1color attribute, the file written is named /tmp/ldapsearch-fw1color-a00188
-T timeout - Client-side timeout in milliseconds, for all operations.-u - Show user friendly entry names in the output. For example, show cn=Babs Jensen, users, omi instead of cn=Babs Jensen, cn=users,cn=omi-w password - The password.-Z - Encrypt using SSL.-z sizelimit -Server-side size limit for search, in entries.Example:
ldapsearch -p 18185 -b cn=omi objectclass=fw1host objectclass
The LDAP directory will be queried for fw1host objects using port number 18185 with DN common name omi. For each object found, the value of its objectclass attribute is printed.
Description Enables the search of the object database according to search parameters.
Syntax
# queryDB_util [-t <table_name>] [-o <object_name>] [-a][-mu <modified_by>] [-mh <modified_from>][-ma <modified_after>] [-mb <modified_before>] [-p{m|u|h|t|f}][-f <filename>] [-h] [-q]
Parameter |
Description |
|---|---|
|
The name of the table. |
|
The name of the object. |
|
All objects. |
|
The name of the administrator who last modified the object. |
|
The host from which the object was last modified. |
|
The date after which the object was modified |
|
The date before which the object was modified |
|
Short print options:
|
|
The name of the output file |
|
Display command help |
|
Quit. |
Example:
Print modification details of all objects modified by administrator aa
query> -a -mu Bob -pm Object Name:my_object Last Modified by:Bob Last Modified from:london Last Modification time:Mon Jun 19 11:44:27 2000
Object Name:internal_ca Last Modified by:Bob Last Modified from:london Last Modification time:Tue Jun 20 11:32:58 2000
A total of 2 objects match the query. |
Description Manages DAIP gateways in a DAIP database.
Syntax
# rs_db_tool [-d] <-operation <add <-name object_name> <-ip module_ip>
<-TTL Time-To-Live> >
# rs_db_tool [-d] <-operation fetch <-name object_name> >
# rs_db_tool [-d] <-operation <delete <-name object_name> >
# rs_db_tool [-d] <-operation <list> >
# rs_db_tool [-d] <-operation <sync> >
Parameter |
Description |
|
debug file. |
|
Add entry to database. |
|
Enter the name of the gateway object. |
|
Enter the IP Address of the gateway. |
|
The relative time interval (in seconds) during which the entry is valid. |
|
Get entry from database. |
|
Delete entry from database. |
|
List all the database entries. |
|
Synchronize the database. |