
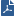

Security Gateways with a Bridge interface can support Layer 3 routing over non-bridged interfaces. If you configure a Bridge interface with an IP address on a Security Gateway (not on Cluster Members), the Bridge interface functions as a regular Layer 3 interface. It participates in IP routing decisions on the Security Gateway and supports Layer 3 routing.
Configure the Security Gateway to reroute packets on the Bridge interface. Set the value of the kernel parameter fwx_bridge_reroute_enabled to 1. The Security Gateway makes sure that the MD5 hash of the packet that leaves the Management Interface and enters the Bridge interface is the same. Other packets in this connection are handled by the Bridge interface without using the router.
Notes:
Procedure:
Step |
Description |
|---|---|
1 |
Connect to the command line on the Security Gateway. |
2 |
Log in to the Expert mode. |
3 |
Modify the |
3A |
Back up the current
Important - If this file does not exit, create it. Run:
|
3B |
Edit the current
|
3C |
Add this line in the file:
Important - This configuration file does not support spaces or comments. |
3D |
Save the changes in the file. |
3E |
exit the Vi editor. |
4 |
Set the value of the required kernel parameter on-the-fly:
|
5 |
Make sure the Security Gateway loaded the new configuration:
|
6 |
Reboot the Security Gateway when possible. After reboot, make sure the Security Gateway loaded the new configuration:
|
To resolve this issue, configure the Security Gateway to recognize that the first packet is from the Management Interface. The Security Gateway makes sure that the MD5 hash of the packet that leaves the Management Interface and enters the Bridge interface is the same. Other packets in this connection are handled by the Bridge interface without using the router.
Step |
Description |
|---|---|
1 |
Connect to the command line on the Security Gateway. |
2 |
Log in to the Expert mode. |
3 |
Modify the |
3A |
Back up the current
Important - If this file does not exit, create it. Run:
|
3B |
Edit the current
|
3C |
Add the applicable line in the file. Important - This configuration file does not support spaces or comments. For IPv4 traffic:
For IPv6 traffic:
|
3D |
Save the changes in the file. |
3E |
exit the Vi editor. |
4 |
Reboot the Security Gateway. |
5 |
Make sure the Security Gateway loaded the new configuration:
|
To resolve this issue, you can disable inspection on the Management Interface and disable local Anti-Spoofing.
Important - This procedure removes inspection from the Management Interface and could compromise Security Gateway's security. If you are unsure whether your environment is safe to use this method, contact Check Point Support.
Step |
Description |
|---|---|
1 |
Connect to the command line on the Security Gateway. |
2 |
Log in to the Expert mode. |
3 |
Modify the |
3A |
Back up the current
Important - If the file does not exist, create it:
|
3B |
Edit the current
|
3C |
Add this line:
Notes:
|
3D |
Save the changes and exit the Vi editor. |
4 |
Modify the $ |
4A |
Back up the current $
Important - If the file does not exist, create it:
|
4B |
Edit the current $
|
4C |
Add these three lines:
Notes:
|
4D |
Save the changes and exit the Vi editor. |
5 |
Reboot the Security Gateway. |