
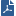

Create Firewall rules that relate to inbound traffic in the inbound traffic Rule Base and rules that relate to outbound traffic in the outbound traffic Rule Base.
To create a Firewall rule:
Column |
Description |
|---|---|
NO |
Rule priority number. Rule priority is important because a client checks firewall rules based on its sequence in the Rule Base. Rules are enforced from the top to the bottom. The last rule is usually a Cleanup Rule that says to drop traffic that does not match any of the previous rules. |
Name |
Name of the Firewall Rule. |
Source or Destination |
|
Service |
Network protocol or service used by traffic. |
Action |
What is done to traffic that matches the rule: Accept or Drop. |
Track |
When the rule is enforced:
Notes:
|
Firewall Rules and Domain Controllers
|
Important - When creating Firewall Rules for endpoint clients, create explicit rules that allow all endpoints to connect to all of the domain controllers on the network. |
Related Topics |