


What can I do here?
Use this window to select the gateways of the Star or Meshed VPN community.
Note - For Global VPN Communities, see: VPN and Multi-Domain Security Management
|
Getting Here - SmartConsole > Security Policies > Access Control > Policy > Access Tools > VPN Communities > New Star/Meshed Community > Gateways |
To configure an internally managed VPN meshed community:
(There are instances where the VPN domain is a group which contains only the Security Gateway itself, for example where the Security Gateway is acting as a backup to a primary Security Gateway in an MEP environment.)
The network Security Gateway objects are now configured, and need to be added to a VPN community.
Note - There is nothing to configure on the IPsec VPN page, regarding certificates, because internally managed Security Gateways automatically receive a certificate from the internal CA.
The New Meshed Community window opens.
A VPN tunnel is now configured.
For information on other options, such as Encryption, Shared Secret, and Advanced, see: IPsec & IKE
Source |
Destination |
VPN |
Service |
Action |
|---|---|---|---|---|
Any |
Any |
Meshed community |
Any |
Accept |
Where "Meshed community" is the VPN community you have just defined.
A star VPN community is configured in much the same way as a meshed community, the difference being the options on the Star Community window:
A VPN Domain is a collection of internal networks that use Security Gateways to send and receive VPN traffic. Define the resources that are included in the VPN Domain for each Security Gateway. Then join the Security Gateways into a VPN community - collection of VPN tunnels and their attributes. Network resources of different VPN Domains can securely communicate with each other through VPN tunnels that terminate at the Security Gateways in the VPN communities.
VPN communities are based on Star and Mesh topologies. In a Mesh community, there are VPN tunnels between each pair of Security Gateway. In a Star community, each satellite Security Gateway has a VPN tunnel to the central Security Gateway, but not to other Security Gateways in the community.
Note - Global VPN Communities are not supported in this release.
Mesh Topology |
Star Topology |
Item |
Description |
|---|---|
1 |
Security Gateway |
2 |
Satellite Security Gateways |
3 |
Central Security Gateway |
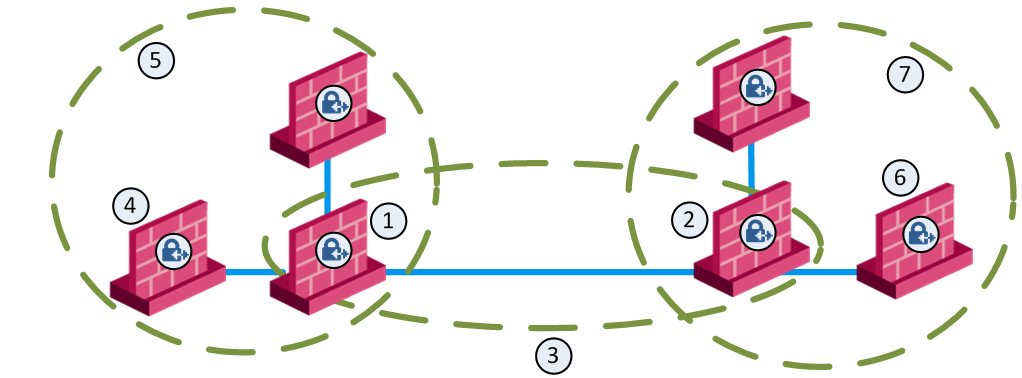
Item |
Description |
|---|---|
1 |
London Security Gateway |
2 |
New York Security Gateway |
3 |
London - New York Mesh community |
4 |
London company partner (external network) |
5 |
London Star community |
6 |
New York company partner (external network) |
7 |
New York Star community |
This deployment is composed of a Mesh community for London and New York Security Gateways that share internal networks. The Security Gateways for external networks of company partners do not have access to the London and New York internal networks. However, the Star VPN communities let the company partners access the internal networks of the sites that they work with.