Azure Active Directory (SCIM)
Registering Application through the Microsoft Azure Portal
-
Log in to your Microsoft Azure Portal.
-
Navigate to Azure Active Directory in the left pane.
-
Go to Manage > Enterprise applications.
-
Click New application.
-
Click Create your own application.
-
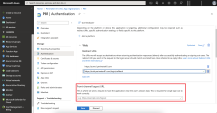
In the What's the name of your app filed, enter a name for your application.

Note - Do not change the default setting.
-
Click Create.
The Microsoft Azure application is created.
-
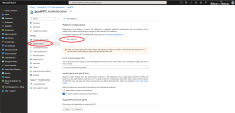
Browse to App registrations, locate and select your application.
-
Click Manage > Authentication > Add a platform.
The Configure platforms window appears.
-
Select Web.
-
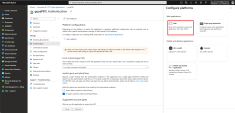
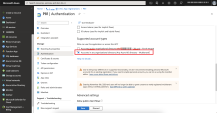
In the Redirect URI (Optional) field, select Web from the type of application list and enter
https://workspace.perimeter81.comURI where the access token is sent to. -
Click Configure.
-
In the Redirect URIs section, enter
https:// auth.perimeter81.com/login/callback. -
In the Front-channel logout URL section, enter
https://{{WORKSPACE}}.perimeter.comwhere{{WORKSPACE}}refers to your Harmony SASE workspace name. -
To allow access from external organizations, in the Supported account types section, select Accounts in any organizational directory (Any Azure AD directory - Multitenant).
-
Click Save.
Configuring the Permissions for the Application
To configure the permissions for the application:
-
Log in to your Microsoft Azure Portal.
-
Click Identity > Applications > App registrations > All applications.
-
Select your application.
-
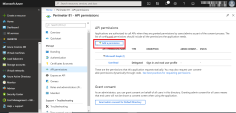
Click Overview > Manage > API Permissions.
-
Click Add a permission.
The Request API permissions page appears.
-
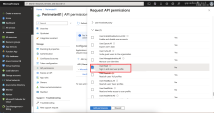
Click Microsoft APIs and select Microsoft Graph from the list of available APIs to change the access level.
-
Click Delegated permissions.
-
Select the User.Read and Directory.Read.All checkbox to modify the permissions so your application can read the directory..
-
Click Add permissions > Configured permissions > Grant admin consent for approval of your app API permissions.
-
Click Yes.
Your application gets the granted permissions.
-
To enable user group support, enable:
-
Application Permissions: Read directory data.
-
Delegated permissions: Access the directory as the signed in user.
-
-
Click Save to save the changes.
-
To remove the Windows Azure Active Directory API permission, see Appendix A - Removing Microsoft Entra ID (formerly Azure AD) API Permissions.
Configuring the Key
-
Log in to your Microsoft Azure Portal.
-
Go to Identity > Applications > App registrations > All applications.
-
Browse to App registrations, locate and select your application.
-
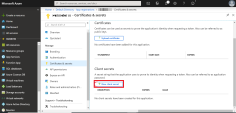
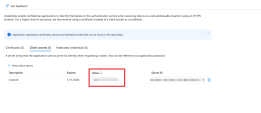
Go to Manage > Certificates & secrets.
-
Click New client secret.
The Add a Client secret window appears.
-
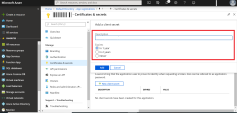
In the Description filed, enter a name for the key.
-
In the Expires field, select the expiry:
-
In 1 year
-
In 2 years
-
Never
-
-
Click Add.
The new key is added.
-
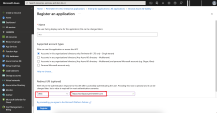
To get the secret value of the key, go to the Client secrets tab and copy the secret Value.
This value is the Client Secret in Harmony SASE Admin console. .

Note - The Secret value of the key need to be copied before you close the screen. If not, you need to create a new key.
Configuring SCIM Integration within Harmony SASE Administrator Portal
-
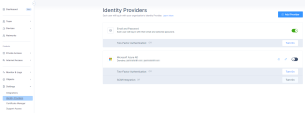
Access the Harmony SASE Administrator Portal and click Settings > Identity Providers.
The Identity Providers page appears.
-
Click Add Provider.
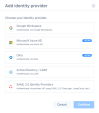
The Add identity provider window appears.
-
Select Microsoft Azure AD.
-
Click Continue.
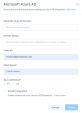
The Microsoft Azure AD page appears.
-
In the Microsoft Azure AD Domain field, enter the domain name.
-
In the Domain Aliases field, enter the email ID(s) separated by commas or spaces.
-
In the Client ID field, enter the Application (client) ID in Microsoft Azure AD:
-
Log in to your Microsoft Azure Portal.
-
Go to Identity > Applications > App registrations > All applications.
-
Browse to App registrations, locate and select your application.
-
Go to Overview > Application (client) ID.
-
Copy the Application (client) ID value.
-
-
In the Client Secret field, enter the secret value.
-
In the Azure AD Edition, select either:
-
PI
-
P2
-
-
Select the SCIM Integration checkbox to enable continuous sync through the SCIM protocol.
-
Click Done.
-
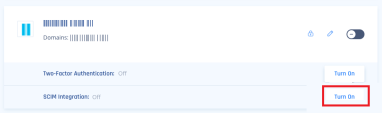
Click Turn On in the SCIM Integration section if you are editing an existing Azure configuration.
-
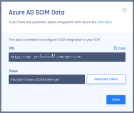
To get the tenant URL and secret token, click Settings in the SCIM Integration section.
-
Click Copy to copy the URL.
This is the Tenant URL that is required when configuring SCIM Integration within Azure AD.
-
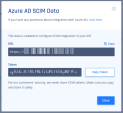
Click Generate Token.
The secret token is generated.
-
Click Copy Token.
This is the Secret Token that is required when configuring SCIM Integration within Azure AD.
-
Click Close.
Configuring SCIM Integration within Azure AD Management Portal
-
Log in to your Microsoft Azure Portal.
-
Navigate to Azure Active Directory in the left pane.
-
Go to Manage > Enterprise applications.
-
Search and select the enterprise application you created.
-
In the left navigation pane, go to Manage > Provisioning.
-
Click Getting Started.
The Provisioning window appears.
-
In the Provisioning Mode list, select Automatic.
-
Expand Admin Credentials and enter these:
-
Tenant URL, see step 14 in Configuring SCIM Intergration within Harmony SASE.
-
Secret Token, see step 16 in Configuring SCIM Intergration within Harmony SASE.
-
-
Click Test Connection.
-
Expand Mappings.
-
Enable the Provision Azure Active Directory Groups toggle button.
-
Click Provision Azure Active Directory Users.
The Attribute Mapping window appears.
-
In the Target Object Actions section, select the relevant actions.
These actions will trig calls to the SCIM adapter.
-
Configure Attribute Mappings to match these configuration by deleting all the irrelevant fields and changing
userPrincipalName:Azure Active Directory Attribute
customappsso Attribute
Matching Precedence
userPrincipalNameemails[type eq “work”].value1
givenNamename.givenNamesurnamename.familyNameSwitch([IsSoftDeleted], , "False", "True", "True", "False")activemailuserName
Note - If the
userPrincipalNameandemails[type eq "work"].valuedo not match, mapuserNamewithmail. -
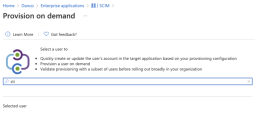
To provision a user on demand, click Provision on demand tab.
The Provision on demand window appears.
-
Search and select the user who you want to provision or update.
-
Click Provision.