AWS Redundant Tunnels - Transit Gateway
Prerequisites
-
An active Harmony SASE Administrator Portal account and network.
-
Make sure you have installed the Harmony SASE Agent on your devices.
-
Administrator account in the Firewall/ Router/ Cloud Management Portal.
-
Your Harmony SASE network must have at least two different gateways in the same network.

Notes -
-
You can deploy the gateways in two separate regions for comprehensive ISP redundancy.
-
You can scale up the network. Adding another region does not affect the connection.
-
Step 1 - Configurations in the AWS Management Console
Creating a Transit Gateway
|
|
Note - If you already have a Transit Gateway in your AWS region, skip this procedure. |
-
Access the AWS Management Console and go to the TRANSIT GATEWAYS section.
-
Click Transit Gateway > Create transit Gateway.
-
Create the Transit Gateway with the default settings.
-
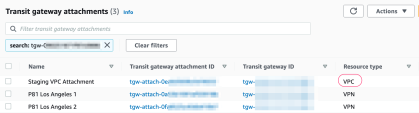
In the VPC section, go to Transit Gateway Attachments and create a Transit Gateway Attachment for your VPC.
Creating Two Site-to-Site VPN Connections
-
Access the AWS Management Console and go to your AWS VPC > VIRTUAL PRIVATE NETWORK(VPN) section.
-
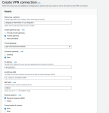
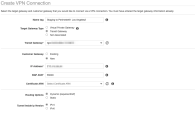
Click Site-to-Site VPN Connections > Create VPN Connection.
The Create VPN connection window appears.
-
Enter these:
-
Transit Gateway - Transit gateway you created.
-
Customer gateway - New.
-
IP address - IP address of the first Harmony SASE gateway.
-
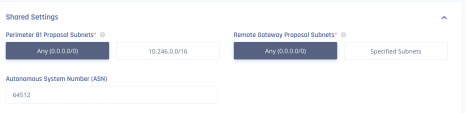
BGP ASN - ASN you plan to use for the Harmony SASE network. The default is 64512.
-
Routing options - Dynamic (requires BGP).
(Recommended) Use suitable naming conventions so that you can locate and distinguish between the connections later.
-
-
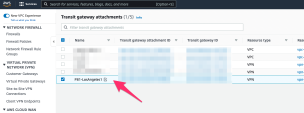
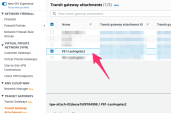
In the TRANSIT GATEWAYS section, go to Transit Gateway attachments and find the Transit Gateway Attachment you created.
Rename it with a meaningful name.
-
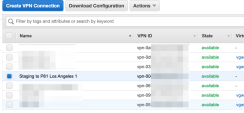
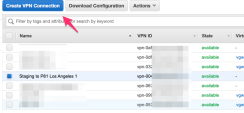
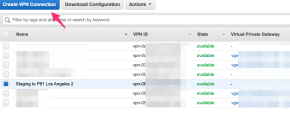
Go back to Site-to-Site VPN Connections, select the VPN connection you created, and then click Download Configuration.
The Download configuration window appears.
-
Enter these:
- Vendor - Generic
-
Platform - Generic
-
Software - Vendor Agnostic
-
Ike version - Ikev2
-
Click Download.
The system downloads the file. Rename the file as Tunnel1.txt.
-
Repeat steps 1-7 for the other Site-to-Site Tunnel with the IP address of the second Harmony SASE gateway.
-
In the TRANSIT GATEWAYS section, go to Transit Gateway attachments and find the Transit Gateway Attachment you created.
Rename it with a meaningful name.
|
|
Note - To access your VPC through the redundant connection, you must have a VPC Attachment connected to the Transit gateway. |
Creating Static Routes
-
Access the AWS Management Console and go to VPC.
-
Select the corresponding VPC attached to the Transit Gateway and then select the Main Route Table for the VPC.
-
Edit the main Route Table for the VPC:
-
In the Destination column, add the subnet mask of your Harmony SASE network.
-
In the Target column, select Transit Gateway (Route for reverse traffic).

Note - If this is not the Main Route Table for the VPC, locate each subnet associated with the VPC and add the reverse route for the Harmony SASE internal subnet range.
-
Step 2 - Creating the Tunnels in the Harmony SASE Administrator Portal
-
Access the Harmony SASEAdministrator Portal and click Networks.
-
Click the network where you want to create the tunnel.
-
In one of the gateways, click
 > Add Tunnel.
> Add Tunnel. -
Click IPSec Site-2-Site Tunnel and click Continue.
-
Select Redundant Tunnels and click Continue.
The Redundant IPSec Tunnels window appears.
-
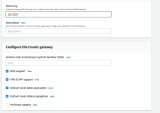
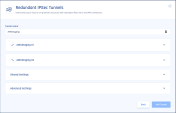
For the first tunnel:
-
Expand the Tunnel 01 drop-down.
-
To automatically populate the tunnel configuration values, click Upload File and upload Tunnel_1.txt file.
-
For manual configuration, copy the values from Tunnel_1.txt file as shown below.
-
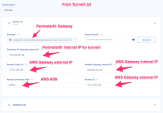
Shared Secret - Pre-Shared Key
-
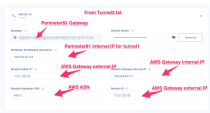
Harmony SASE gateway Internal IP - Inside IP Addresses of Customer Gateway.
-
Remote Public IP & Remote ID - Outside IP Addresses of Virtual Private Gateway.
-
Remote Gateway internal IP - Inside IP Addresses of Virtual Private Gateway. The IP on the AWS side has a subnet (/30), discard it when pasting.
-
Remote Gateway ASN - BGP Configuration Options of Virtual Private Gateway ASN from the file.
-
-
-
Enter the above copied values.
-
For the second tunnel, expand the Tunnel 02 drop-down and repeat step 6 with the values from Tunnel_2.txt file.
-
In the Shared Settings section:
-
In the Advanced Settings section, enter the information for your tunnel type:
Field
IKE Version
IKE Lifetime
Tunnel Lifetime
Dead Peer Detection Delay
Dead Peer Detection Timeout
Encryption (Phase 1)
Encryption (Phase 2)
Integrity (Phase 1)
Integrity (Phase 2)
Diffie Hellman Groups (Phase 1)
Diffie Hellman Groups (Phase 2)
Cloud Vendor
Amazon AWS
Single Tunnel - AWS Virtual Gateway V2 8h 1h 10s 30s aes256 aes256 sha512 sha512 21 21 Single Tunnel - AWS Transit Gateway V2 8h 1h 10s 30s aes256 aes256 sha512 sha512 21 21 Redundant Tunnels - AWS Virtual Private Gateway V2 8h 1h 10s 30s aes256 aes256 sha512 sha512 21 21 Redundant Tunnels - AWS Transit Gateway V2 8h 1h 10s 30s aes256 aes256 sha512 sha512 21 21 Google Cloud Platform
Single Tunnel 1 V2 8h 1h 10s 30s aes256 aes256 sha512 sha512 21 21 Redundant Tunnels
V2 8h 1h 10s 30s aes256 aes256 sha512 sha512 21 21
Microsoft Azure Single Tunnel -
Azure Virtual Network Gateway
V2
3600s
27000s
10s
45s
aes256 aes256 sha1 sha1 2
2
Redundant Tunnels - Virtual Network Gateway
V2
9h
9h
10s 30s aes256 aes256 sha1 sha1 2
2
Redundant Tunnels - Virtual WAN
V2
8h
1h 10s 30s aes256 aes256 sha256
sha256
14
14
Other tunnel types
Alibaba Cloud V1 8h 1h 10s 30s aes256 aes256 sha1 sha1 2 2 IBM Cloud
V1
8h 1h 10s 30s aes256 aes256 sha256
sha256
21
21
1 Suggested values. For other supported ciphers, see this Google article.
-
Click Add Tunnel.