Splunk Cloud
Splunk Cloud allows you to search, analyze and view data collated from various systems in your IT infrastructure.
Integrating Splunk Cloud
Step 1 - Setting Up the HTTP Event Collector
The HTTP Event Collector (HEC) allows you send data and application events to a Splunk deployment over HTTP and HTTPS protocols. You can use HEC to generate a token and use it to configure a log library with data in a specific format. This eliminates the requirement for a Splunk forwarder when you send application events.
Step 2 - Enabling an HTTP Event Collector
When you enable HEC, applications use the HEC tokens to send data to HEC, eliminating the requirement for Splunk credentials in your application or supported files.
|
|
Note - If you have managed Splunk, contact Splunk customer support for assistance. |
To enable an HTTP Event Collector:
-
Log in to the Splunk web portal.
-
Click Settings > Data Inputs.
-
Click HTTP Event Collector.
-
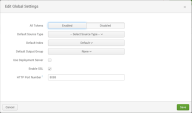
Click Global Settings.
-
In the All Tokens field, select Enabled.
-
To enable communication over HTTPs, select the Enable SSLcheckbox.

Note - It is enabled by default. You can disable it only through Splunk Enterprise.
-
Click Save.
Step 3 - Creating an Event Collector Token
-
Log in to the Splunk web portal.
-
Go to Settings > Add Data.
-
Click Monitor.
-
Click HTTP Event Collector.
-
In the Name field, enter a name for the token.
-
Make sure indexer acknowledgment is disabled for this token.
-
Click Next.
-
Click Review.
-
Verify the settings.
-
Click Submit.
Configuring the Splunk Integration in the Harmony SASE Administrator Portal
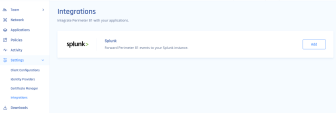
-
Access the Harmony SASE Administrator Portal and click Settings > Integrations.
-
In the SIEM integrations section, in the Splunk row, click Add.
-
Enter these:
Item
Description
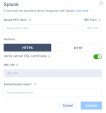
Splunk HEC Host
Enter an appropriate value according to your Splunk tier.
Replace {hostname} with your Splunk server hostname.
-
Splunk Cloud (paid): inputs-<host>
-
Splunk Cloud (free-trial): <host> ORinputs.<host>
HEC Port
-
Splunk Cloud free trial: 8088
-
Splunk Cloud paid: 443
Protocol
-
Splunk Cloud free trial: HTTP
-
Splunk Cloud paid: HTTPS
(For HTTPS only) Verify server SSL certificate:
-
If you are using a self-signed certificate disable SSL verification.
-
If you are using a CA-signed certificate make sure to enable it.
HEC URI
Value is automatically populated.
Authentication token
Enter the token generated in the Splunk web portal.
-
-
Click Validate.
Troubleshooting
This table shows the status codes for all HTTP Event Collector endpoints.
| HTTP status code ID | HTTP status code | Status message | Action required |
|---|---|---|---|
| 200 | OK | Success | None |
| 403 | Forbidden | Token disabled | Enable token at Splunk Web. |
| 401 | Unauthorized | Invalid authorization | Make sure you entered a valid token. |
| 403 | Forbidden | Invalid token | Make sure you entered a valid token. |
| 500 | Internal Error | Internal server error | Contact Check Point Support. |
| 503 | Service Unavailable | Server is busy | There are too many requests pending in the Splunk server queue. Try again later. |
| 400 | Bad Request | Data channel is missing |
Edit the token at the Splunk web portal and make sure the Indexer Acknowledgement is disabled. |
| 400 | Bad Request | Error in handling indexed fields |
Contact Check Point Support . |