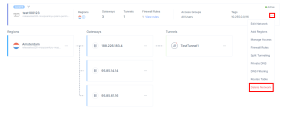
Managing a Network
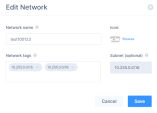
Editing a Network
-
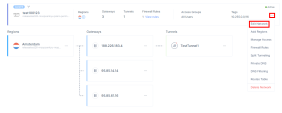
Access the Harmony SASE Administrator Portal and click Networks.
-
Select the network.
-
Click
 and then click Edit Network.
and then click Edit Network.The Edit Network window appears.
-
Make the required changes and click Save.
Adding Regions
-
Access the Harmony SASE Administrator Portal and click Networks.
-
Select the network.
-
Click
 and then click Add Regions.
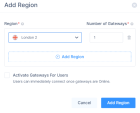
and then click Add Regions.The Add Region window appears.
-
From the Region list, select the region to deploy the Harmony SASE gateway.
-
In the Number of Gateways field, enter the number of private gateways you want to deploy in the region.
-
To add another region, click Add Region and repeat steps 4 and 5.
-
To activate the gateway for users, select the Activate Gateways For Users checkbox.
-
Click Add Region.
Managing Access
Manage Access allows you to select the member groups who can access the network.
To manage access to a network:
-
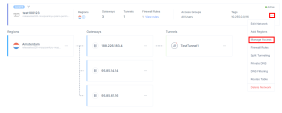
Access the Harmony SASE Administrator Portal and click Networks.
-
Select the network.
-
Click
 and then click Manage Access.
and then click Manage Access.The Manage Access window appears.
-
From the list, select the member groups who can access the network.
-
To remove a member group, click Remove.
-
Click Apply.
Firewall Rules
Firewall Rules allows you to set the firewall access rules for your network.
To set the rules, see Creating a Firewall Access Rule.
Split Tunneling
Split tunneling allows you to choose the traffic that should pass through the tunnel and the traffic that should bypass the tunnel and access the resource directly.
|
|
Best Practices -
|
|
|
Note - Split tunneling by FQDN is supported only for Harmony SASE Agents10.1.x and higher. With older agent versions, split tunneling by FQDN is ignored and reverts to full tunneling. |
To configure split tunneling for a network:
-
Access the Harmony SASE Administrator Portal and click Networks.
-
Select your network.
-
Click
 and then click Split Tunneling.
and then click Split Tunneling.The Split Tunneling window appears.
-
Select one of these:
Item
Description
Automatic (Full tunnel)
Allows all the traffic through the tunnel. That is, split tunneling is disabled. This is the default setting.
Manual
-
Include - Enter the subnets, FQDN, or IP addresses that you want to pass through the tunnel. This is the default setting.
-
Exclude - Enter the subnets, FQDN, or IP addresses that you want to bypass the tunnel.

Important - The processing time depends on the system resource. It takes up to 3 seconds for every 500 subnets.
-
-
Click Apply.
Private DNS
A private DNS allows you to use your local DNS to resolve host names into IP addresses.
Harmony SASE supports DNS at two levels:
-
Network - Allows you to utilize your organization’s DNS server and local domain names.
-
Region - Allows your users to resolve resources through a local DNS server rather than waiting for a remote server response.
|
|
Notes -
|
To configure a private DNS for a network:
-
Access the Harmony SASE Administrator Portal and click Networks.
-
Select the network.
-
To add a private DNS:
-
For a network, click
 and then click Private DNS.
and then click Private DNS. -
For a region, in the Regions section, click
 and then click Regional Private DNS.
and then click Regional Private DNS.
The Add Private DNS window appears.
-
-
Turn on the Enable Private DNS toggle button.
-
If your Private DNS Server(s) supports DoT, from the Port list, select Over TLS (otherwise your requests are sent over HTTPS).

Note - You can configure multiple private DNS servers for load balancing. Make sure that the DNS endpoint has zone sharing or zone forwarding enabled. This is supported by both cloud-based and on-premises DNS resolvers.
-
In the Server IP Address field, enter the IP address of your DNS servers. You can enter up to four IP addresses.
-
In the Search Domains field, enter the suffix for the DNS query.
For example, if the domain is checkpoint.com, if your enter support, then the system automatically redirects to support.checkpoint.com.
-
Click Apply.
Wait for the network status to change from Deploying... to Active.
DNS Filtering
DNS Filtering allows you to manage internet access for members in your network by blocking or allowing websites using allow-list and block-list.
|
|
Best Practices -
|
To configure DNS filtering for a network:
-
Access the Harmony SASE Administrator Portal and click Networks.
-
Select the network.
-
Click
 and then click DNS Filtering.
and then click DNS Filtering.The DNS Filtering window appears.
-
Turn on the Enable DNS Filter toggle button.
-
From the Blocked Domain Categories list, select the website categories you want to block.
-
In the Blocked Domains field, enter the domains you want to block or upload a .CSV file with the domains.
Make sure that the .CSV file:
-
Contains all the entries in a single column.
-
Each cell contain only one entry.
-
The number of entries does not exceed 1000.
-
Each entry is in the form domain.com, without www, HTTP, HTTPs prefixes.
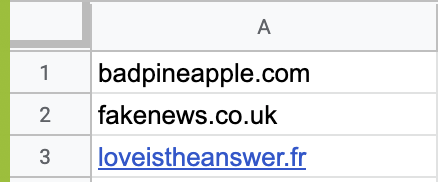

Note - When you block a domain, the system blocks the related sub-domains as well.
-
-
In the Exclusion list field, enter the URLs you want to exempt from the blocked domains list or upload a .CSV file with the domains.
-
Click Apply.
After the settings are applied, a tooltip shows that DNS filtering is activated in your network.
The changes are enforced the next time when the member connects to your network using the Harmony SASE Agent.
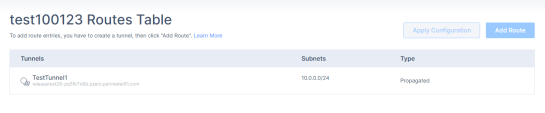
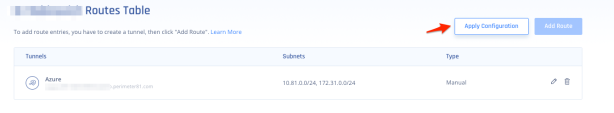
Routes Table
Routes Table shows the routes created for the tunnels in your network.
To add a new route to a tunnel in your network:
-
Access the Harmony SASE Administrator Portal and click Networks.
-
Select the network.
-
Click
 at the right end of the network and then select Routes Table.
at the right end of the network and then select Routes Table. -
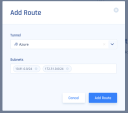
Click Add Route.
-
Enter all the subnets on the remote side of the tunnel and then click Add Route.
For cloud-based resources, enter these values for your vendor.
Tunnel Type
Subnets
Amazon AWS
AWS Single Tunnel - Transit Gateway
CIDRs of the attached VPCs (The VPCs to which you want to gain access)
AWS Single Tunnel - Virtual Gateway
Subnets you want to reach on the AWS side of the tunnel.
AWS Redundant Tunnels - Transit Gateway
Subnets you want to reach on the AWS side of the tunnel.

Note - Ensure that the added route matches the route transmitted by BGP. Any discrepancies, such as incorrect subnetting or supernetting, are strictly prohibited.
AWS Redundant Tunnels - Virtual Private Gateway
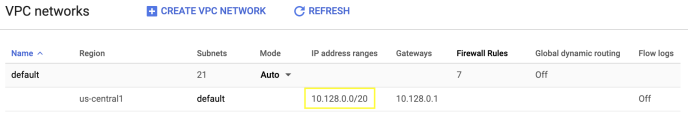
Google Cloud Platform
Single Tunnel
From the GCP console, copy the subnets of the regions where your resources are installed.
Redundant Tunnels
Microsoft Azure
Single Tunnel -
Virtual Network Gateway
Subnets of the regions where your resources are installed.
Redundant Tunnels - Virtual Network Gateway
Redundant Tunnels - Virtual WAN
-
Click Apply Configuration.