PingFederate
Prerequisites
-
Administrator access to the Harmony SASE Administrator Portal.
-
Administrator account with the Identity Provider Management Portal.
High-Level Procedure
Step 1 - Configure the PingFederate Management Portal
-
Log in to PingFederate Management Portal.
-
Go to SP Connections and click Create New.
-
Select Browser SSO Profiles as Connection Type.
-
Select Browser SSO as Connection Options.
-
Configure the parameters and map the attributes.
-
Entity ID: US-based platform:
urn:auth0:perimeter81:{{WORKSPACE}}-ocEU-based platform:urn:auth0:eu-sase-checkpoint:{{WORKSPACE}}-ocAU-based platform:urn:auth0:au-sase-checkpoint:{{WORKSPACE}}-ocIN-based platform:urn:auth0:in-sase-checkpoint:{{WORKSPACE}}-ocFor example:acme.perimeter81.comworkspace should translate tourn:auth0:perimeter81:acme-oc -
Assertion Consumer Service URL: US-based platform:
https://auth.perimeter81.com/login/callback?connection={{WORKSPACE}}-ocEU-based platform:https://auth.eu.sase.checkpoint.com/login/callback?connection={{WORKSPACE}}-ocAU-based platform:https://auth.au.sase.checkpoint.com/login/callback?connection={{WORKSPACE}}-ocIN-based platform:https://auth.in.sase.checkpoint.com/login/callback?connection={{WORKSPACE}}-oc -
SAML Request: HTTP-Redirect Binding
-
SAML Response: HTTP-POST Binding
-
Attributes:
Harmony SASE Attribute
PingFederate Attribute
email
Mail
given_name
Given Name
family_name
Surname
-
-
Configure Browser SSO.
-
In the SAML Profiles, select SP-Initiated SSO and SP-Initiated SLO.
-
Go to Assertion Creation section and select Configure Assertion.
-
Accept all defaults for the next two screens.
-
-
Go to IdP Adapter Mapping section and select the existing authentication or add a new one.

Note - Auth0 only requires the NameIdentifier claim. All other attributes will be passed further to the end application.
-
Configure Protocol Settings.
Values for Protocol Settings are imported from the metadata file. Next, you will see the Assertion Consumer Service URL and the Sign-Out URLs. Click Next to the Allowable SAML Bindings section.
-
Leave POST and Redirect enabled. Make sure SAML Assertion is always signed.
-
Configure Credentials. On Digital Signature Settings, select your signing certificate and make sure you check the option to include it in the element.
-
Configure the certificate used to sign incoming requests.
-
Review your settings and set as Active or Inactive.
-
Click Save at the bottom of the screen. You should see the new SP Connection on the Main screen.
Step 2 - Configure the Harmony SASE Administrator Portal
-
Log in to the Harmony SASE Administrator Portal with a administrator account.
-
Go to Settings > Identity Providers.
-
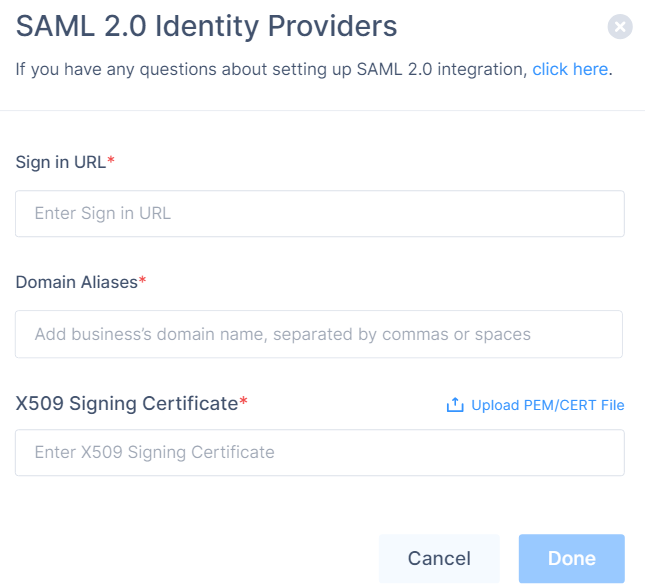
Click Add Provider.
The Add identity provider pop-up appears.
-
Select SAML 2.0 Identity Providers and click Continue.
-
In the Sign in URL field, enter the Identity Provider Sign-in URL from your SAML Identity Provider.
Identity Provider
Sign in URL
Generic SAML
Identity Provider Sign in URL
Active Directory Federation Services (AD FS)
https://{{Your ADFS Domain}}/adfs/lsAuth0
Auth0 login URL
OneLogin
SAML 2.0 Endpoint (HTTP) value
PingOne
https://sso.connect.pingidentity.com/sso/idp/SSO.saml2?idpid={{idpid}}PingFederate
https://sso.{{Your PingFederate Domain}}.com/idp/SSO.saml2Rippling
Rippling IdP Sign-in URL.
JumpCloud
JumpCloud IDP URL
Okta
Okta Sign on URL
Google Applications
SSO URL
-
In the Domain Aliases field, enter the business domain names separated by commas or space.
-
In the X509 Signing Certificate field, enter the X.509 signing certificate for the application from the SAML Identity Provider.
If you have the signing certificate as PEM/CERT file, click Upload PEM/CERT File and select the file.
-
Click Done.
|
|
Note - After the first successful authentication of a member with SAML, Harmony SASE does this:
|