IBM Cloud
Prerequisites
-
An active Harmony SASE Administrator Portal account and network.
-
Make sure you have installed the Harmony SASE Agent on your devices.
-
Administrator account in the Firewall/ Router/ Cloud Management Portal.
Step 1 - Configuring a VPN Gateway at the IBM Cloud Console
-
Access the IBM Cloud Console and open the VPC section and go to Network > VPNs.
-
Go to the IKE policies tab and click New IKE policy.
-
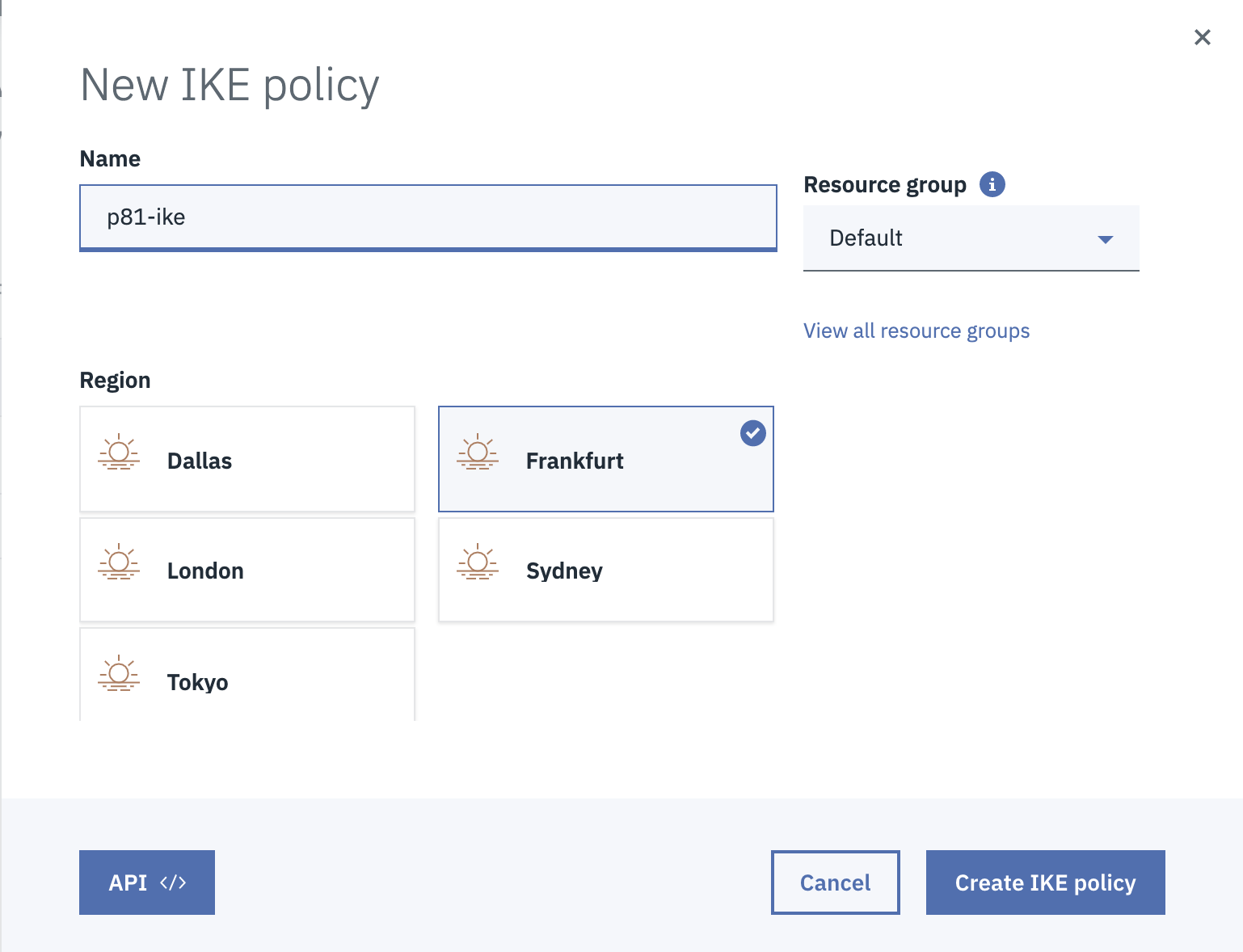
The New IKE policy window appears.
-
Enter these:
-
Name - Name of the policy.
-
Resource group
-
Region - Region in which the VPC is located.
-
-
Click Create IKE policy.
The system creates the IKE policy.
-
Click
 and then Edit.
and then Edit. -
Enter these:
-
IKE Version - 1
-
DH Group - 2
-
Authentication - sha256
-
Key Lifetime - 28800
-
Encryption - aes256
-
-
Click Save IKE policy.
-
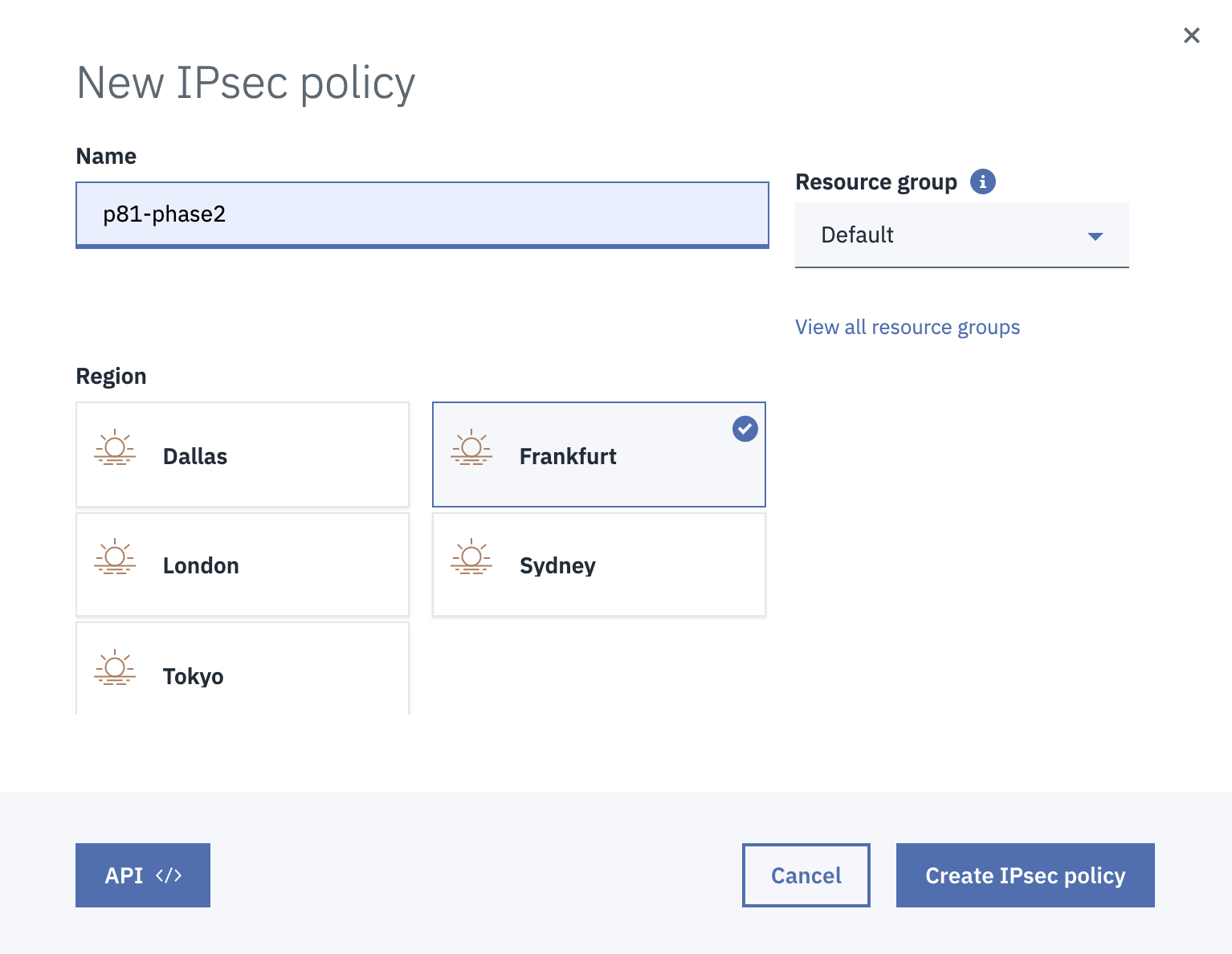
Go to the IPSec Policies tab and click New IPSec Policy.
The New IPSec policy window appears.
-
Enter these:
-
Name - Name of the policy.
-
Resource group
-
Region - Region in which the VPC is located.
-
-
Click Create IPSec policy.
The system creates the IPSec policy.
-
Click
 and then Edit.
and then Edit. -
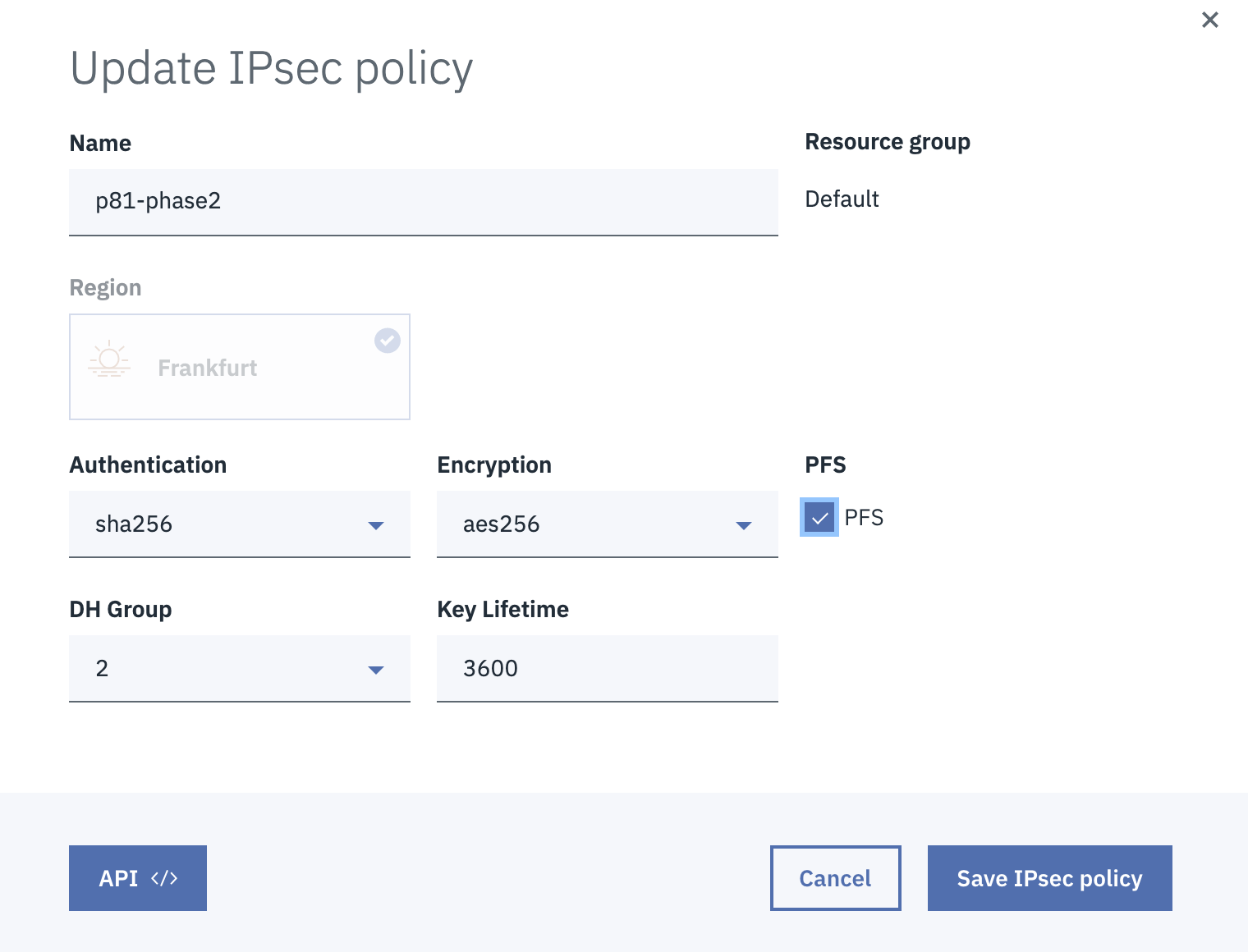
Enter these:
-
Authentication - sha256
-
Encryption - aes256
-
PFS - Select the checkbox.
-
DH Group - 2
-
Key Lifetime - 3600
-
-
Click Save IPSec policy.
-
Go to the VPN gateways tab and click New VPN gateway.
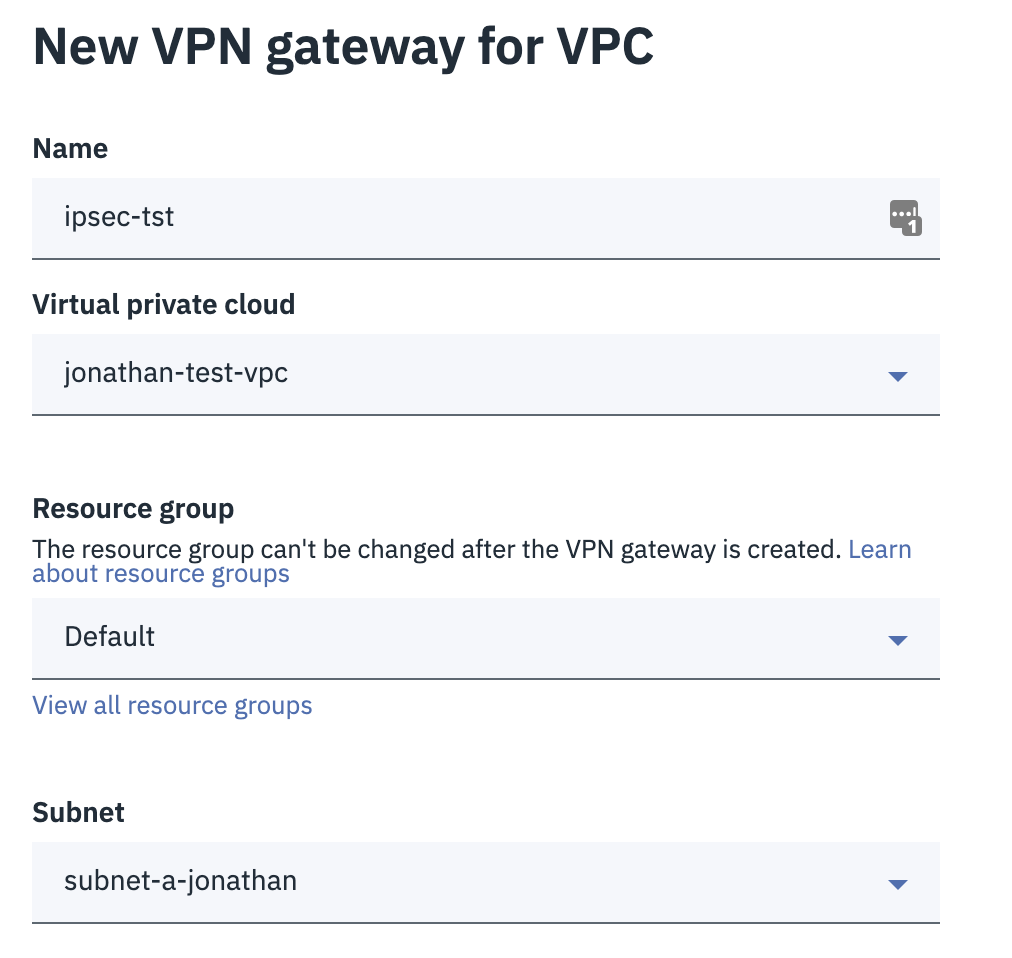
The New VPN gateway for VPC window appears.
-
Enter these:
-
Name - Name of the VPN gateway.
-
Virtual private cloud - Select the required cloud.
-
Resource group - Select the resource group.
-
Subnet - Select the required subnet.
-
-
Select New VPN Connection for VPC.
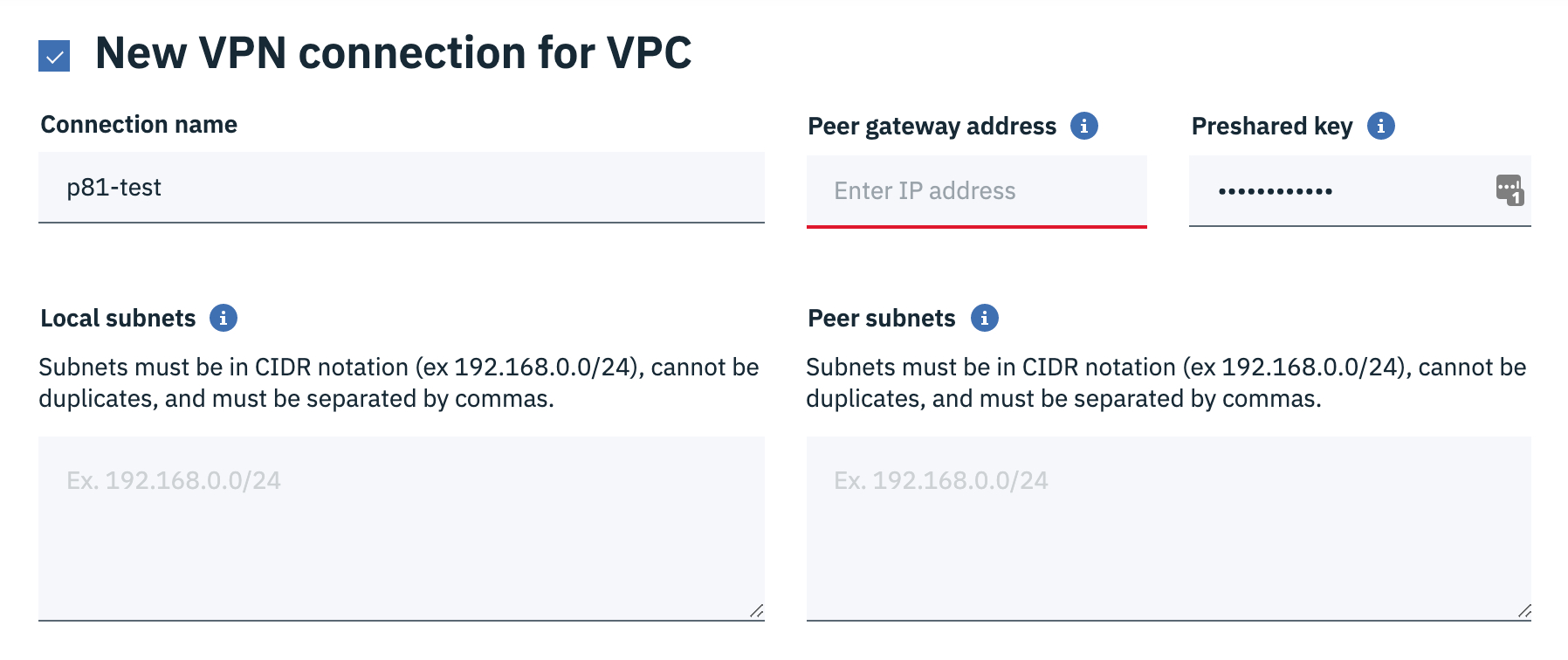
The New VPN connection for VPC window appears.
-
Enter these:
-
Connection name - Name of the VPN connection.
-
Peer gateway address - IP address of your Harmony SASE gateway.
-
Preshared key - A string with at least 8 characters that contains upper-case letters and numbers.
-
Local subnets - Specify one or more subnets in the VPC you want to connect.
-
Peer subnets - 10.255.0.0/16 (Unless you have custom configurations or multiple tunnels to the same Harmony SASE gateway).
-
Dead peer detection action - Restart
-
Interval - 10 seconds
-
Timeout - 30 seconds
-
IKE policy - Select the IKE policy created earlier.
-
IPSec policy - Select the IPSec policy created earlier.
-
Step 2 - Creating the Tunnel in the Harmony SASE Administrator Portal
-
Access the Harmony SASE Administrator Portal and click Networks.
- Click the network where you want to create the tunnel.
-
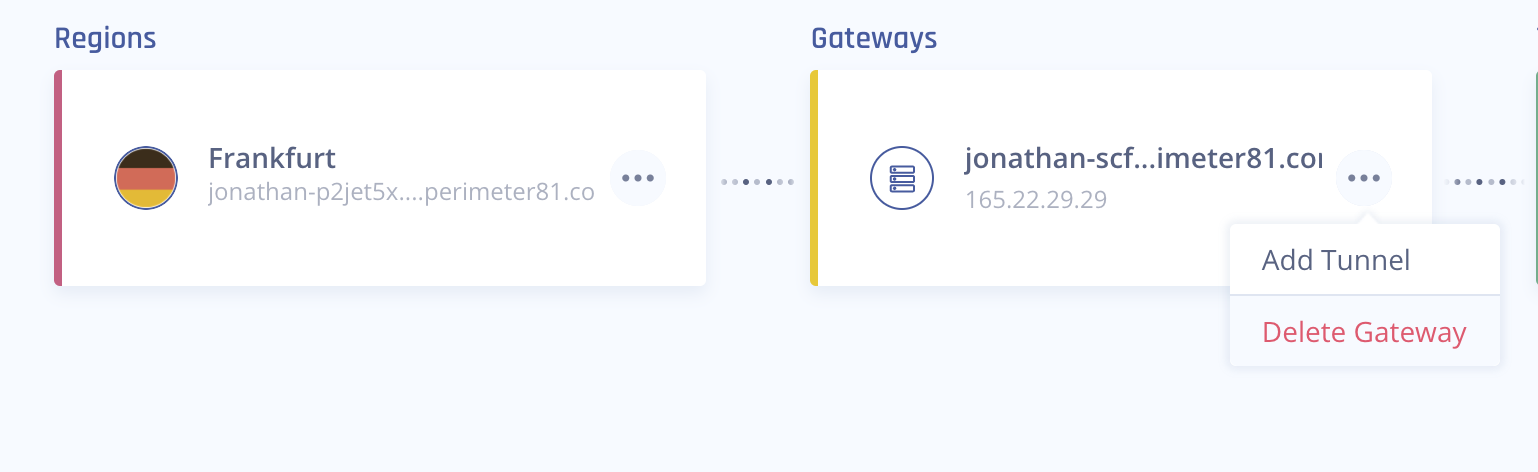
In the required gateway, click
 > Add Tunnel.
> Add Tunnel. -
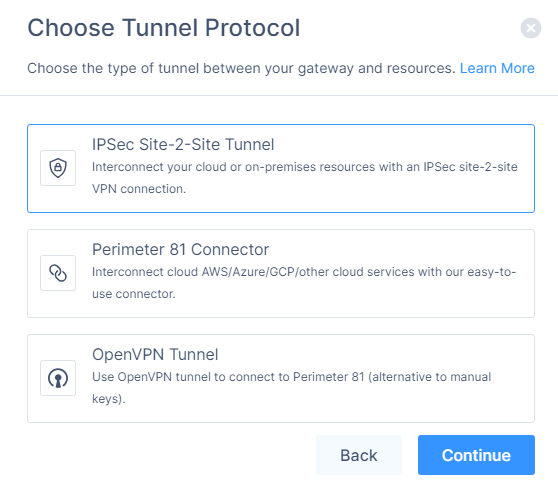
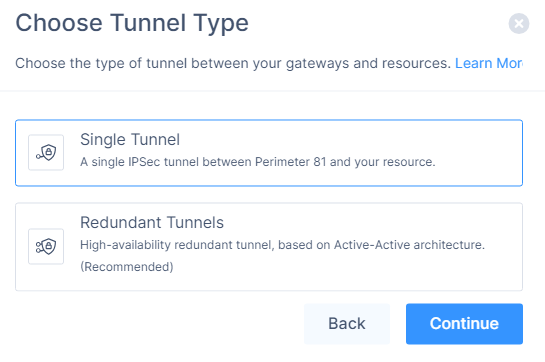
Click IPSec Site-2-Site Tunnel and click Continue.
-
Click Single Tunnel and click Continue.
The IPSec Site-2-Site Tunnel window appears.
-
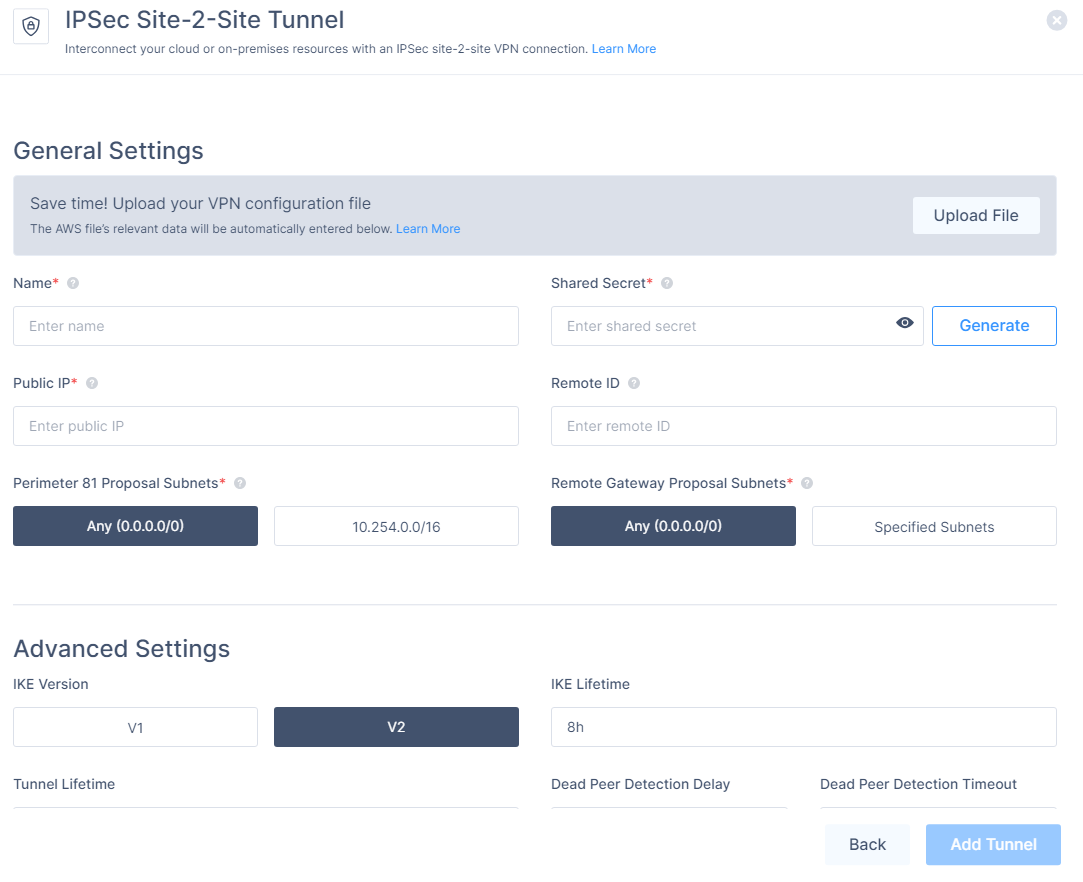
In the General Settings section, enter these:
-
Name - Name of the tunnel.
-
Public IP - IP address of the VPN Gateway defined in the IBM Cloud console.
-
Remote ID - Identical to Remote IP.
-
Shared Secret - Preshared key in the IBM Cloud console.
-
Perimeter 81 Gateway Proposal Subnets - 10.255.0.0/16 or the value defined in the IBM Cloud console.
-
Remote Gateway Proposal Subnets - Subnets in the VPC that you want to connect.
-
-
In the Advanced Settings section, enter the information for your tunnel type:
Field
IKE Version
IKE Lifetime
Tunnel Lifetime
Dead Peer Detection Delay
Dead Peer Detection Timeout
Encryption (Phase 1)
Encryption (Phase 2)
Integrity (Phase 1)
Integrity (Phase 2)
Diffie Hellman Groups (Phase 1)
Diffie Hellman Groups (Phase 2)
Cloud Vendor
Amazon AWS
Single Tunnel - AWS Virtual Gateway V2 8h 1h 10s 30s aes256 aes256 sha512 sha512 ecp521 ecp521 Single Tunnel - AWS Transit Gateway V2 8h 1h 10s 30s aes256 aes256 sha512 sha512 ecp521 ecp521 Redundant Tunnels - AWS Virtual Private Gateway V2 8h 1h 10s 30s aes256 aes256 sha512 sha512 ecp521 ecp521 Redundant Tunnels - AWS Transit Gateway V2 8h 1h 10s 30s aes256 aes256 sha512 sha512 ecp521 ecp521 Google Cloud Platform
Single Tunnel 1 V2 8h 1h 10s 30s aes256 aes256 sha512 sha512 ecp521 ecp521 Redundant Tunnels
V2 8h 1h 10s 30s aes256 aes256 sha512 sha512 ecp521 ecp521 Microsoft Azure Single Tunnel -
Azure Virtual Network Gateway
V2
3600s
27000s
10s
45s
aes256 aes256 sha1 sha1 modp1024 modp1024 Redundant Tunnels - Virtual Network Gateway
V2
9h
9h
10s 30s aes256 aes256 sha1 sha1 modp1024 modp1024 Redundant Tunnels - Virtual WAN
V2
8h
1h 10s 30s aes256 aes256 sha256
sha256
modp2048 modp2048 Other tunnel types
Alibaba Cloud V1 8h 1h 10s 30s aes256 aes256 sha1 sha1 modp1024 modp1024 IBM Cloud
V1
8h 1h 10s 30s aes256 aes256 sha256
sha256
ecp521 ecp521 1 Suggested values. For other supported ciphers, see this Google article.
-
Click Add Tunnel.
Verifying the Setup in IBM Cloud Console
-
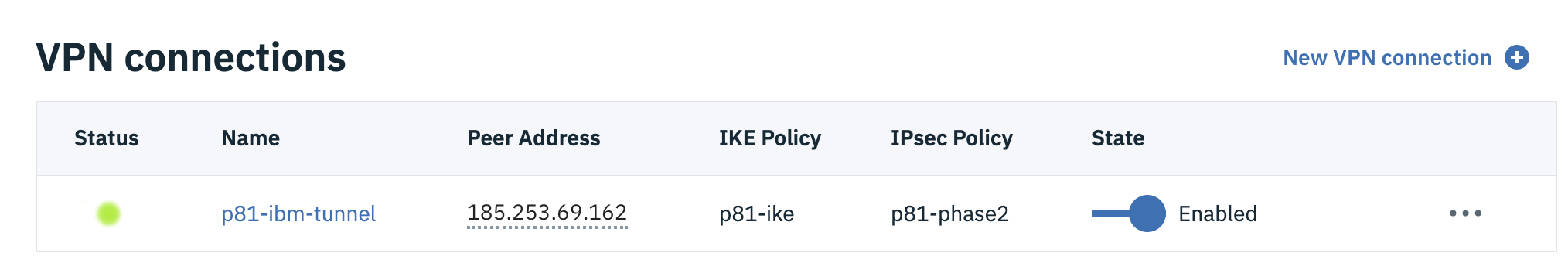
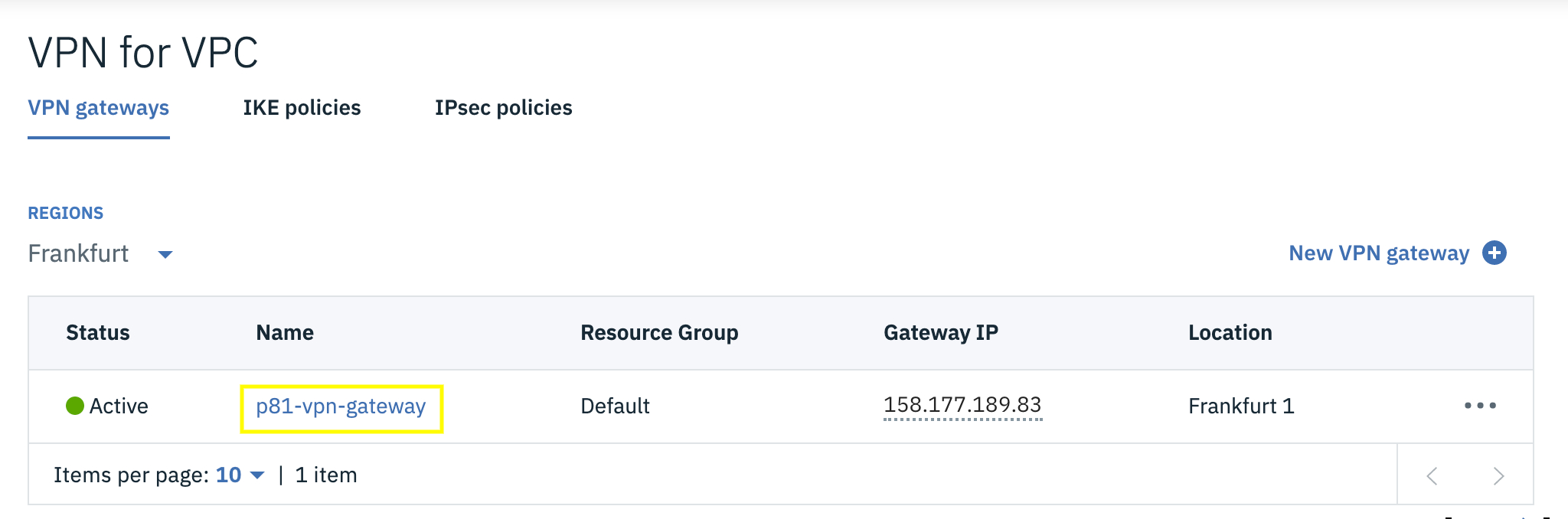
Access the IBM Cloud console and go to the VPN gateways tab.
-
Select the name of the VPN Gateway associated with the tunnel.
-
Scroll down and click View all connections.
Verify whether the tunnel Status as active.