Google Cloud Platform
This chapter describes the procedure to establish a Site-to-Site IPsec tunnel between your Harmony SASE network and Google Cloud Platform (GCP).
Prerequisites
-
An active Harmony SASE Administrator Portal account and network.
-
Make sure you have installed the Harmony SASE Agent on your devices.
-
Administrator account in the Firewall/ Router/ Cloud Management Portal.
Step 1 - Configurations in the GCP Console
Creating a Virtual Private Gateway
-
Access the GCP console and go to Network Connectivity.
-
In the left menu, click VPN.
-
Click Cloud VPN Gateways > Create VPN gateway.
-
Click the link to create Classic VPN.
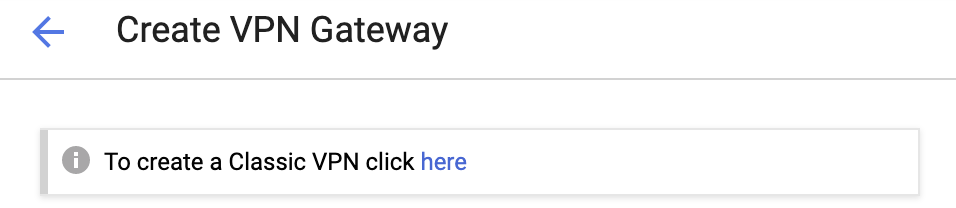
-
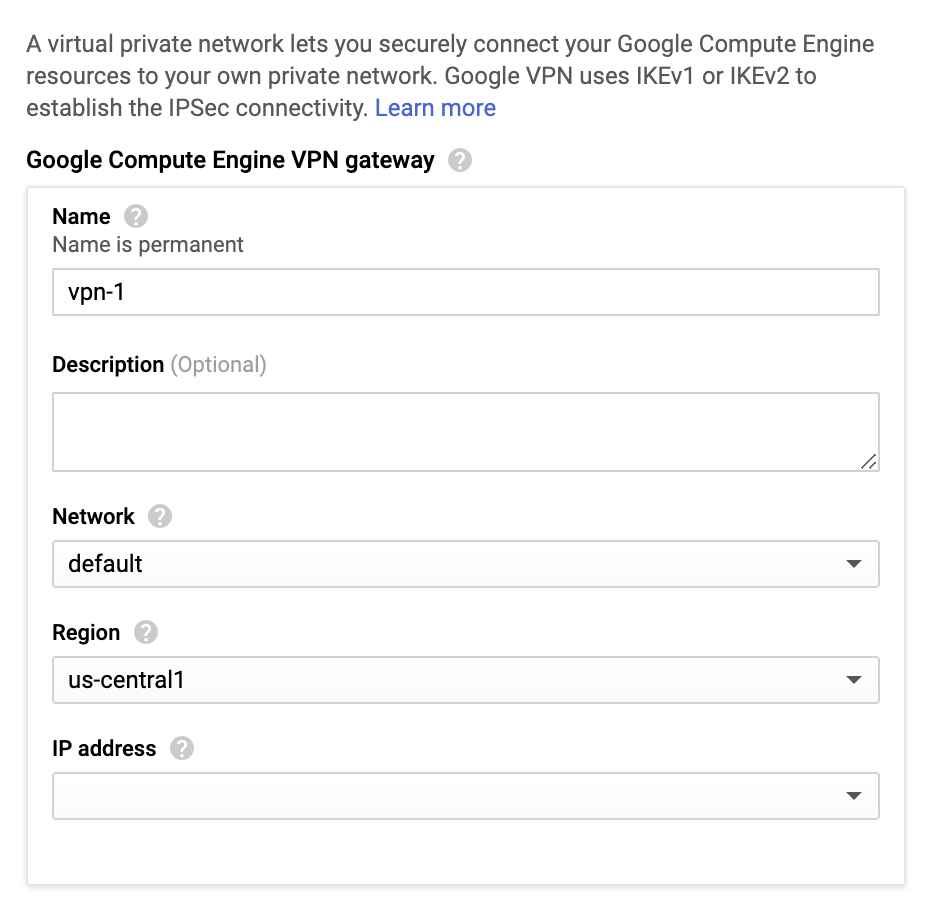
Enter these:
-
Name - Name of the gateway.
-
Network - Select default or a specific VPC.
-
Region - Select the region where your resources are located.
-
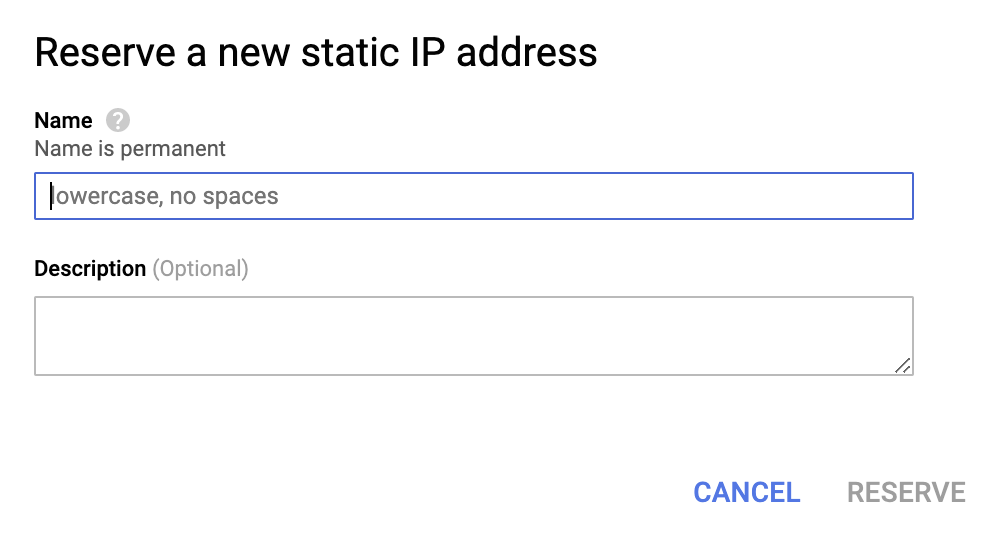
IP address - Create an IP address to connect your gateway and click Reserve.
-
Creating a Tunnel
-
Access the GCP console and go to Network Connectivity.
-
In the left menu, click VPN.
- Click Cloud VPN Tunnels > Create VPN tunnel.
-
Enter these:
-
Name - Name of the tunnel.
-
Remote peer IP address - IP address of your Harmony SASE Gateway.
To obtain this, go to the Harmony SASEAdministrator Portal > Networks and select the network that contains the gateway to which you wan to create a tunnel.
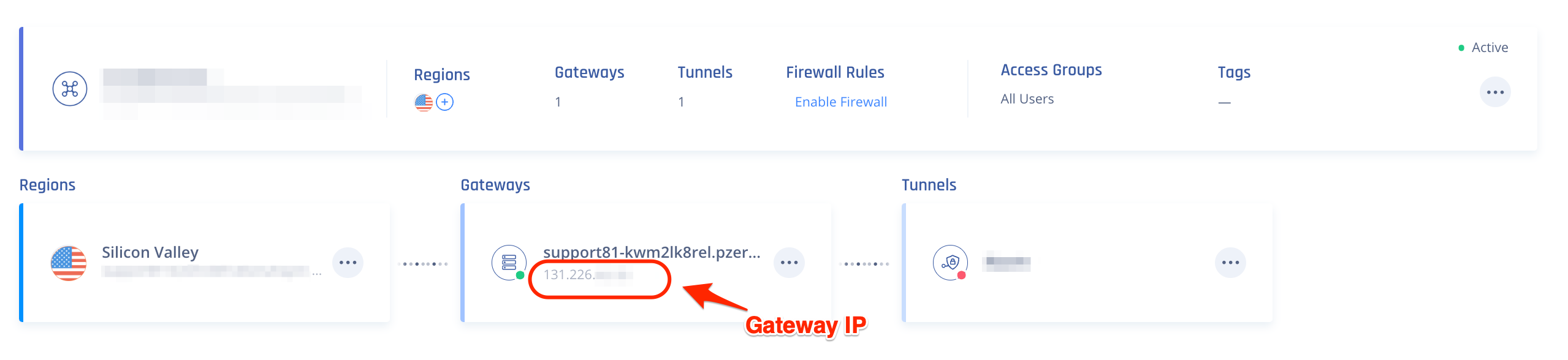
-
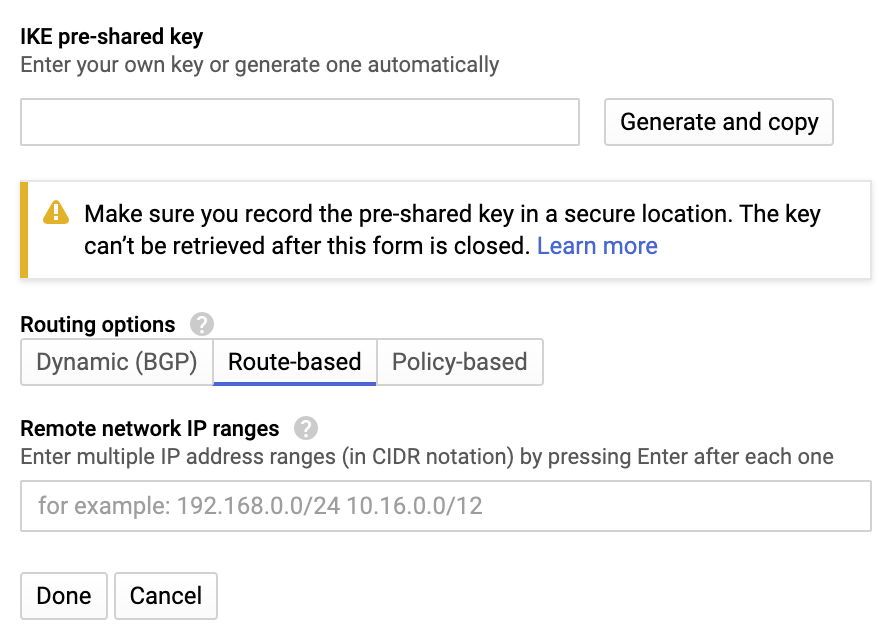
IKE Version - IKEv2
-
IKE pre-shared key - Click Generate and copy or select a key of your own and note it down.
-
Routing options - Route-based
-
Remote network IP ranges - 10.255.0.0/16 (unless customized)
-
-
Click Done and then Create.
Configuring the Routing Rules to the VPC Network
-
Access the GCP console and go to the VPC Network section.
-
In the left menu, click Routes.

-
Click Create Route Rule.
-
Enter these:
-
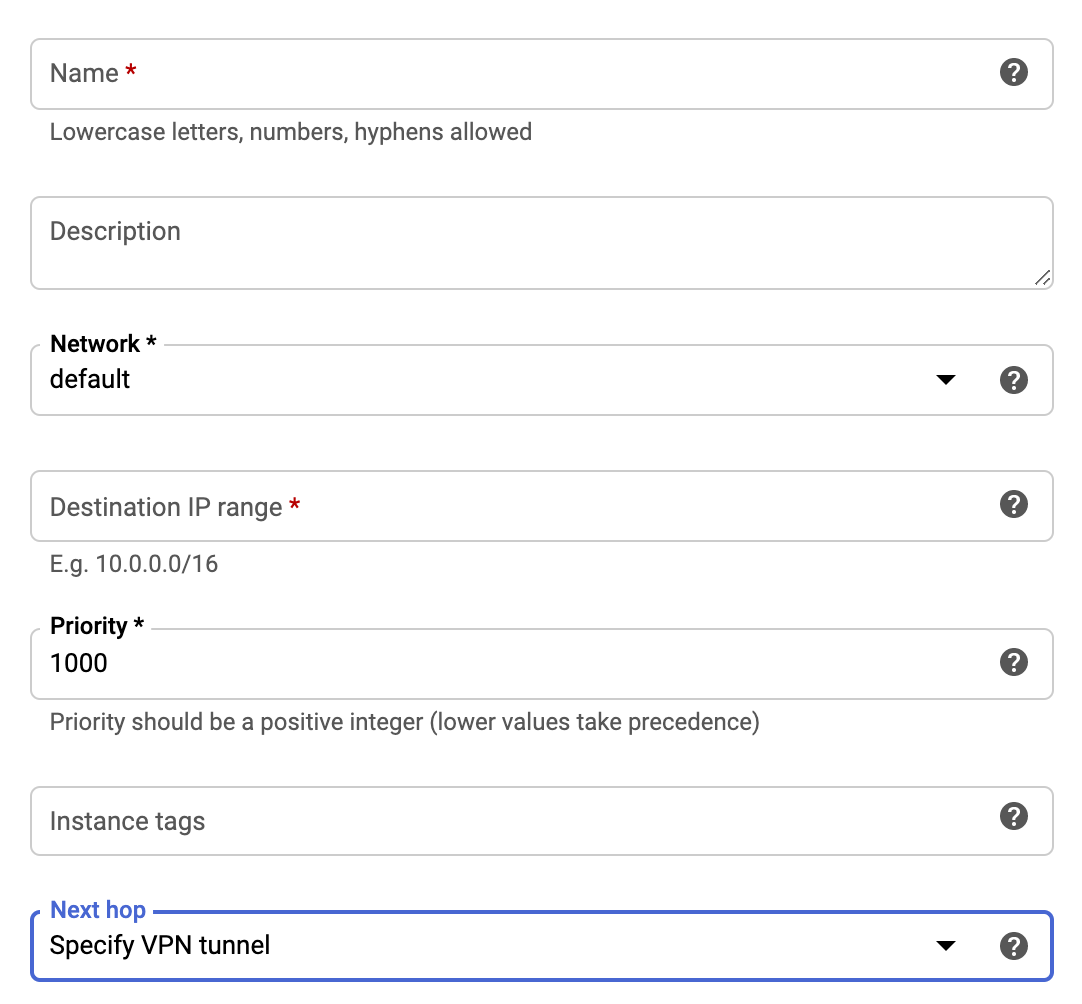
Name - Name of the VPN gateway.
-
Network - Select the VPC network that contains the instances served by the VPN gateway. This must be the same network selected in the previous steps.
-
Destination IP range - 10.255.0.0/16 (or customized)
-
Priority - 1000
-
Next hop - Select Specify VPN Tunnel.
-
Next hop VPN tunnel - Select the VPN tunnel you created in the previous steps.
-
-
Click Create.
Allowing Incoming Connections from Harmony SASE Local Network Using Firewall Rules
-
Access the GCP console and go to the VPC Network section.
-
In the left menu, click Firewall rules.

-
Click Create Firewall Rule.
-
Enter these:
-
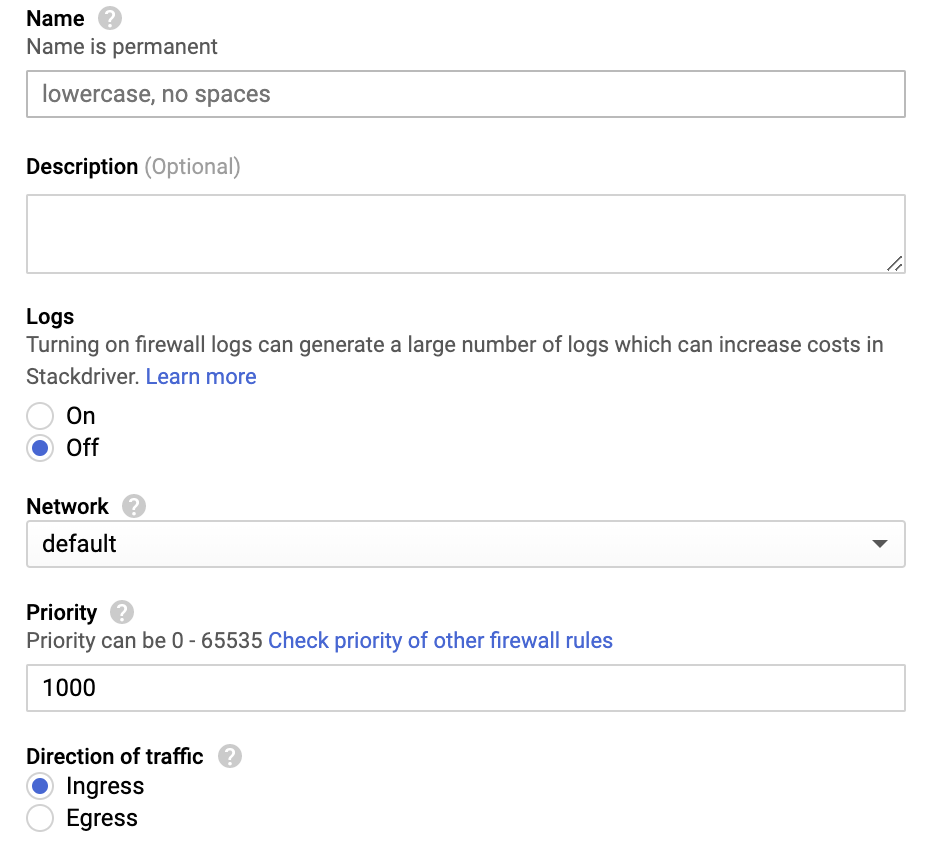
Name - Name of the rule.
-
Logs - Off
-
Network - Select the VPC network that contains the instances served by the VPN gateway. This must be the same network selected in the previous steps.
-
Priority - 1000
-
Direction of traffic - Ingress.
-
Action on match - Allow
-
(Optional) Target tags
-
Source filter - IP ranges
-
Source IP ranges - 10.255.0.0/16 (unless customized)
-
Second source filter - None
-
Protocols and ports - Allow all
-
Step 2 - Creating the Tunnel in the Harmony SASE Administrator Portal
-
Access the Harmony SASE Administrator Portal and click Networks.
- Click the network where you want to create the tunnel.
-
In the required gateway, click
 > Add Tunnel.
> Add Tunnel. -
Click IPSec Site-2-Site Tunnel and click Continue.
-
Click Single Tunnel and click Continue.
The IPSec Site-2-Site Tunnel window appears.
-
In the General Settings section, enter these:
-
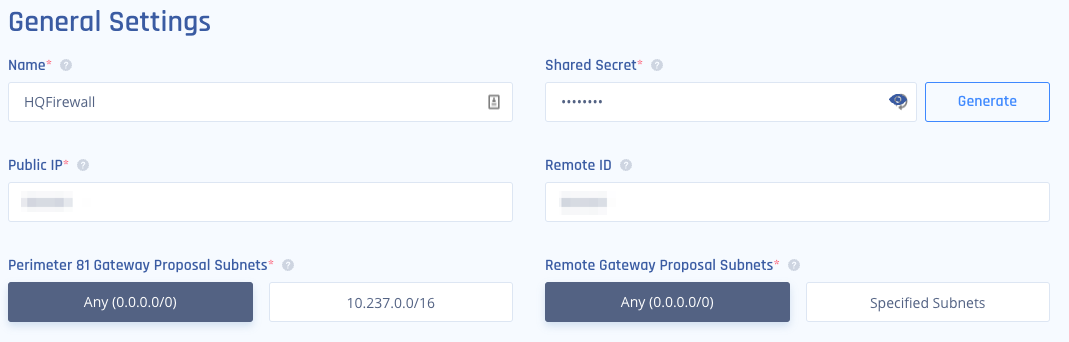
Name - Name of the tunnel.
-
Harmony SASE Gateway Proposal Subnets - Any (0.0.0.0/0)
-
Remote Gateway Proposal Subnets - Any (0.0.0.0/0)
-
-
In the Advanced Settings section, enter the information for your tunnel type:
Field
IKE Version
IKE Lifetime
Tunnel Lifetime
Dead Peer Detection Delay
Dead Peer Detection Timeout
Encryption (Phase 1)
Encryption (Phase 2)
Integrity (Phase 1)
Integrity (Phase 2)
Diffie Hellman Groups (Phase 1)
Diffie Hellman Groups (Phase 2)
Cloud Vendor
Amazon AWS
Single Tunnel - AWS Virtual Gateway V2 8h 1h 10s 30s aes256 aes256 sha512 sha512 21 21 Single Tunnel - AWS Transit Gateway V2 8h 1h 10s 30s aes256 aes256 sha512 sha512 21 21 Redundant Tunnels - AWS Virtual Private Gateway V2 8h 1h 10s 30s aes256 aes256 sha512 sha512 21 21 Redundant Tunnels - AWS Transit Gateway V2 8h 1h 10s 30s aes256 aes256 sha512 sha512 21 21 Google Cloud Platform
Single Tunnel 1 V2 8h 1h 10s 30s aes256 aes256 sha512 sha512 21 21 Redundant Tunnels
V2 8h 1h 10s 30s aes256 aes256 sha512 sha512 21 21
Microsoft Azure Single Tunnel -
Azure Virtual Network Gateway
V2
3600s
27000s
10s
45s
aes256 aes256 sha1 sha1 2
2
Redundant Tunnels - Virtual Network Gateway
V2
9h
9h
10s 30s aes256 aes256 sha1 sha1 2
2
Redundant Tunnels - Virtual WAN
V2
8h
1h 10s 30s aes256 aes256 sha256
sha256
14
14
Other tunnel types
Alibaba Cloud V1 8h 1h 10s 30s aes256 aes256 sha1 sha1 2 2 IBM Cloud
V1
8h 1h 10s 30s aes256 aes256 sha256
sha256
21
21
1 Suggested values. For other supported ciphers, see this Google article.
-
Click Add Tunnel.