Microsoft Sentinel
Microsoft Sentinel (formerly Azure Sentinel) is a scalable, cloud-native, security information event management (SIEM) and security orchestration automated response (SOAR) solution. It delivers intelligent security analytics and threat intelligence across the enterprise, providing a single solution for alert detection, threat visibility, proactive hunting, and threat response.
Configuring the Integration in the Microsoft Azure Portal
Step 1 - Setting up a Log Analytics Workspace
|
|
Note - If you are using an existing log analytics workspace, skip this section. |
-
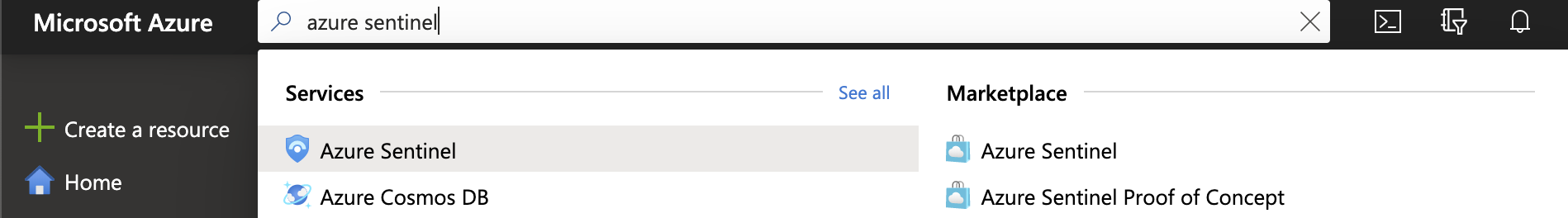
Log in to the Microsoft Azure portal.
-
Search for Azure Sentinel and select it.
-
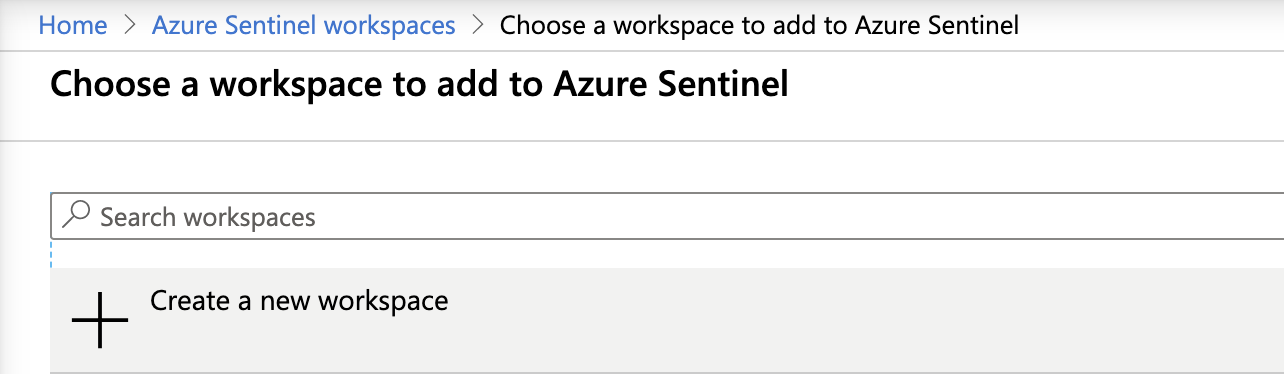
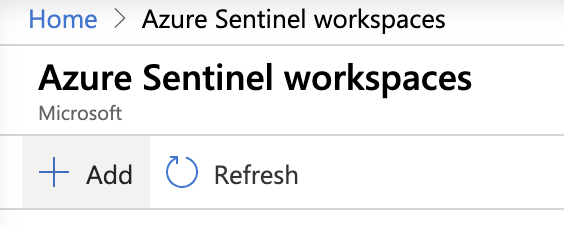
Click Add.
-
Click Create a new workspace.
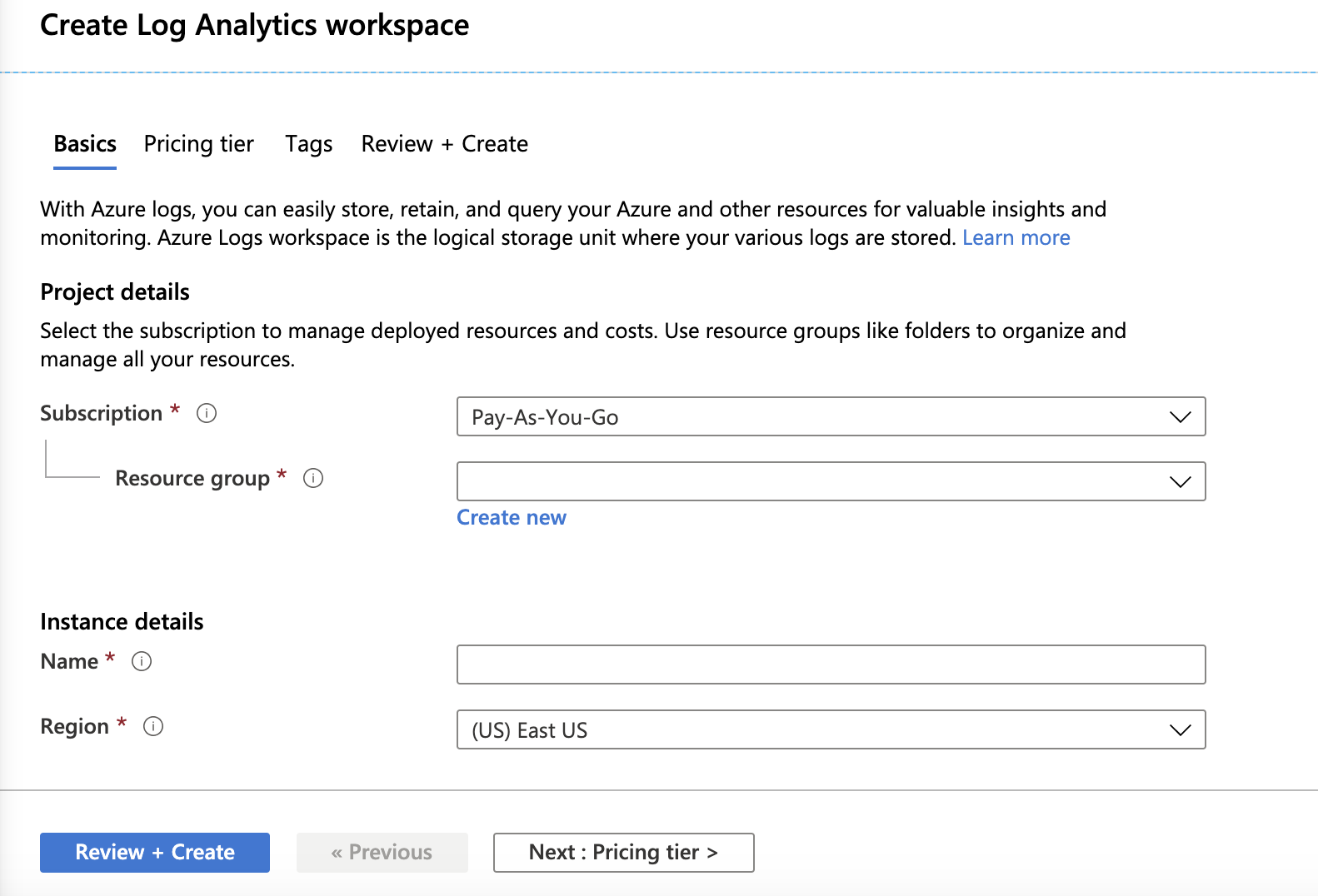
The Create Log Analytics workspace window appears.
-
Enter these:
-
Subscription - A subscription according to your business needs.
-
Resource group - Associate the log analytics workspace with the appropriate business unit.
-
-
Name - Name of the workspace. It must contain minimum four characters (alphabets, numerals and hyphen) up to 63. Make sure hyphen is not the first or last character.
-
Region: Physical location of the server generating the event collector. Select according to pricing and business requirement.
-
(Optional) Review the pricing tiers and set appropriate tags for the workspace.
-
-
Click Review + Create.
Step 2 - Linking the Log Analytics Workspace to Microsoft Sentinel
-
Log in to the Microsoft Azure portal.
-
Search for Azure Sentinel and select it.
-
Click Add.

-
Select the Log Analytics Workspace that you have created or an existing one that you want to utilize.
Step 3 - Finding your Log Analytics Workspace ID and Primary Key
-
Log in to the Microsoft Azure portal.
-
Search for Log Analytics Workspace and select it.
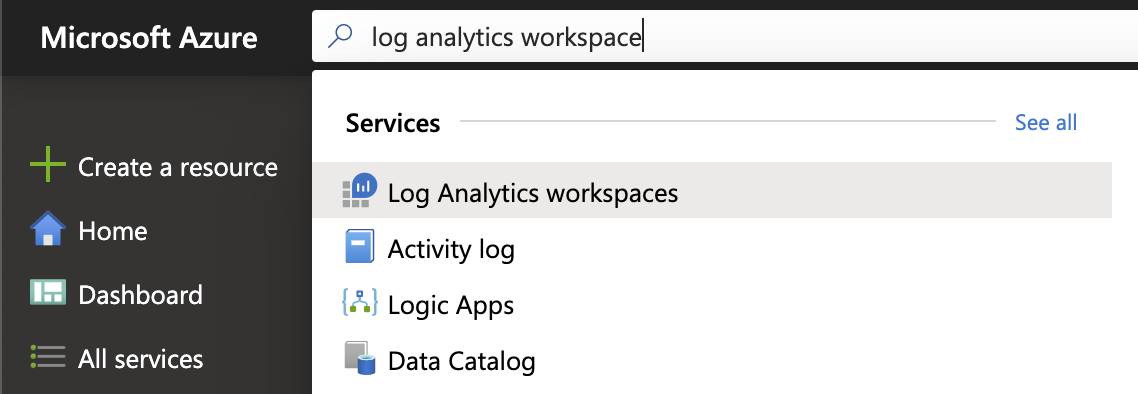
-
Select the workspace you connected to Microsoft Sentinel.
-
In the Settings section, click Advanced settings.
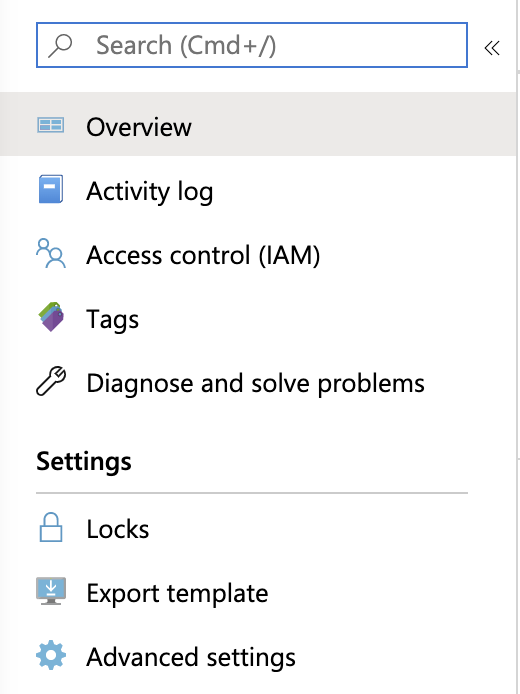
-
Click Connected Sources > Linux Servers and then copy the Workspace ID and the Primary Key.
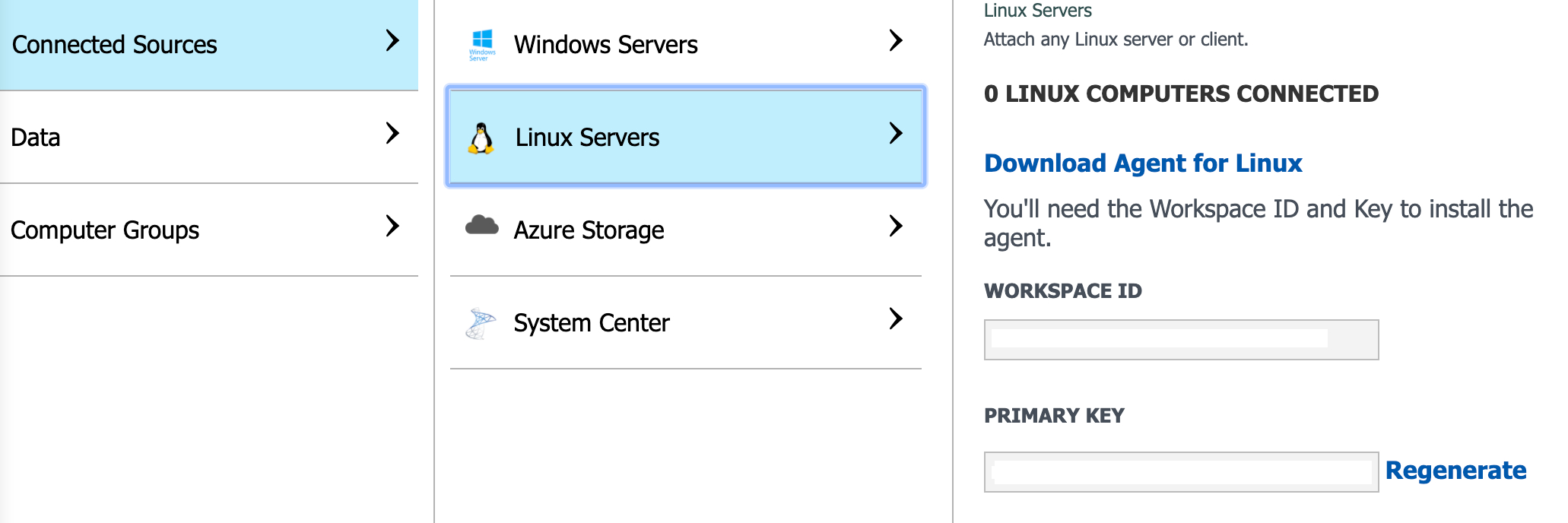
Configuring the Microsoft Sentinel Integration in the Harmony SASE Administrator Portal
-
Access the Harmony SASE Administrator Portal and click Settings > Integrations.
-
In the SIEM integrations section, in the Microsoft Sentinel row, click Add.
-
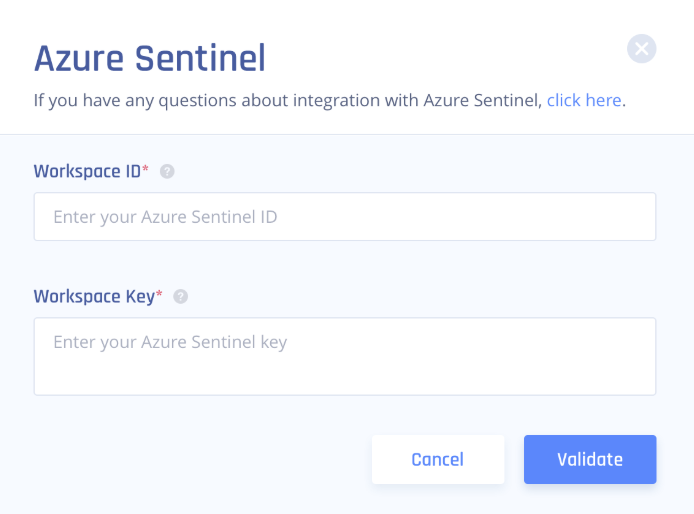
In the Workspace ID field, enter the Log Analytics Workspace ID from the above section.
-
In the Workspace Key field, enter the Log Analytics Primary Key from the above section.
-
Click Validate.
Troubleshooting
| Status Message | Action Required |
|---|---|
| Success | None. |
| SENTINEL_INACTIVE_CUSTOMER | The workspace has been deactivated. |
| SENTINEL_INVALID_CUSTOMER_ID | Make sure you have entered the correct customer ID. |
| SENTINEL_INVALID_AUTHORIZATION | The service failed to authenticate the request. Verify that the workspace ID and connection key are valid. |