Amazon S3
Amazon Simple Storage Service (Amazon S3) is an object storage service that offers industry-leading scalability, data availability, security, and performance.
Prerequisites
-
Ensure that the IAM user has the necessary permissions to access the S3 bucket.
-
Harmony SASE uses these IP addresses to deliver SIEM logs:
-
US tenant:
-
44.199.0.186
-
44.198.227.127
-
50.19.134.176
-
23.20.83.77
-
54.85.165.134
-
-
EU tenant
-
52.50.186.78
-
79.125.50.175
-
34.246.127.40
-
-
Configuring the Integration in the AWS Management Console
Step 1 - Creating a New Bucket
-
Log in to the AWS Management Console.
-
Go to AWS Services and select S3.
-
Click Create Bucket.
The Create bucket window appears.
-
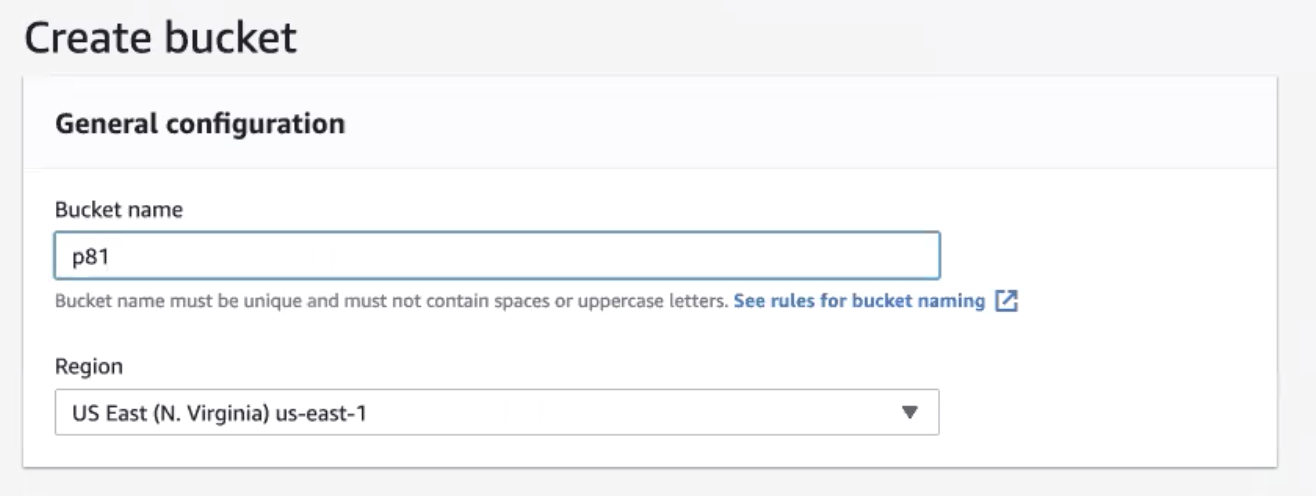
In the Bucket name field, enter the name of the bucket.
The name must contain alphabets only. Hypen (-) and period (.) are not supported.
-
In the Region field, enter the region where Amazon S3 creates buckets. Select the AWS region geographically nearest to you.
-
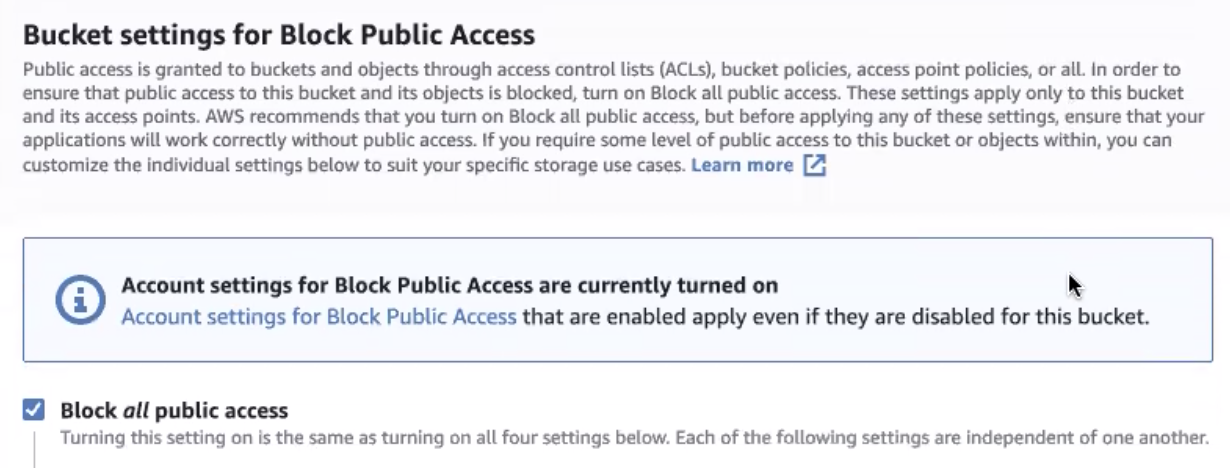
Select or clear the Block all public access checkbox according to your company policy. It is selected by default.
-
In Advanced settings > Object Lock, select Disable.

-
Click Create bucket.
Step 2 - Creating a New IAM Policy
|
|
Important - You can grant the user full access to your S3 buckets (by attaching the appropriate AWS managed policy) or create a new policy that applies only to the Harmony SASE bucket. If you grant full access, skip this procedure. |
-
Log in to the AWS Management Console.
-
Open the AWS Identity and Access Management (IAM) dashboard.
-
Go to the Policies tab and click Create policy.
-
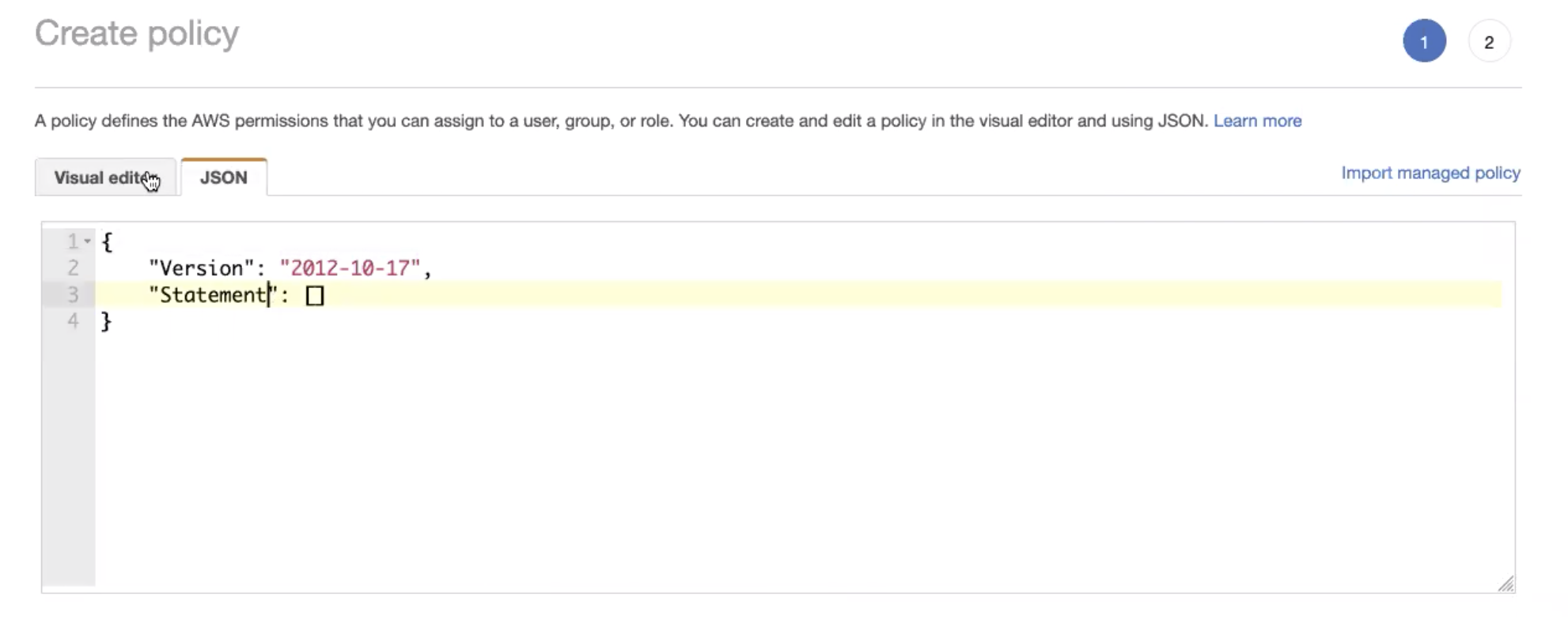
Paste this snippet as a JSON file. Replace
testwith the bucket name.Copy{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:*",
"Resource": "arn:aws:s3:::test"
},
{
"Effect": "Allow",
"Action": "s3:*",
"Resource": "arn:aws:s3:::test/*"
}
]
}
Important - For a full list of permissions granted, see permissions. To restrict the list of permissions, add the highlighted text to the syntax.
{ "Version" : "2012-10-17", "Statement" : [ { "Effect" : "Allow" , "Action" : [ "s3:ListBucket", "s3:GetBucketLocation" ], "Resource" : ["${aws_s3_bucket.pm81-logs.arn}"] }, { "Effect" : "Allow" , "Action" : [ "s3:PutObject" , "s3:GetObject" , "s3:DeleteObject" ], "Resource" : ["${aws_s3_bucket.pm81-logs.arn}/*" ] } ]} -
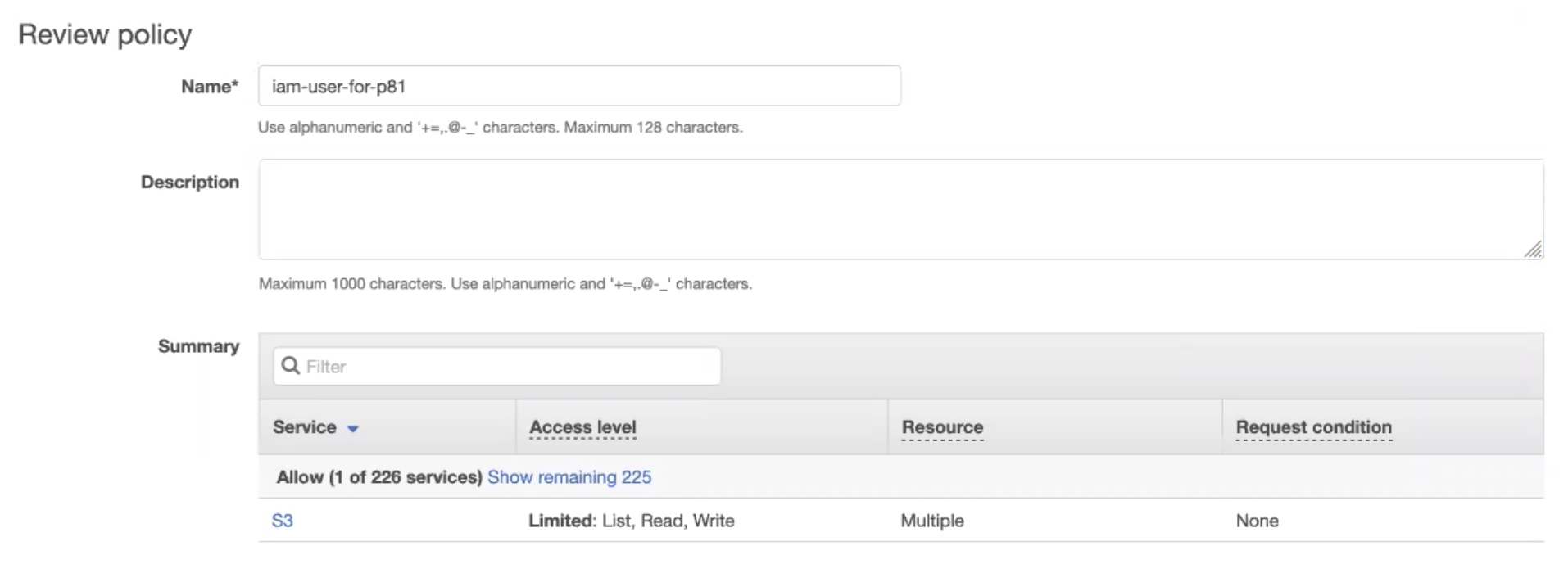
Click Review policy.
The Review policy window appears.
-
Enter these:
-
Name: Name of the policy.
-
(Optional) Description
-
-
Click Create policy.
Step 3 - Creating an AWS User
-
Log in to the AWS Management Console.
-
Open the AWS Identity and Access Management (IAM) dashboard.
-
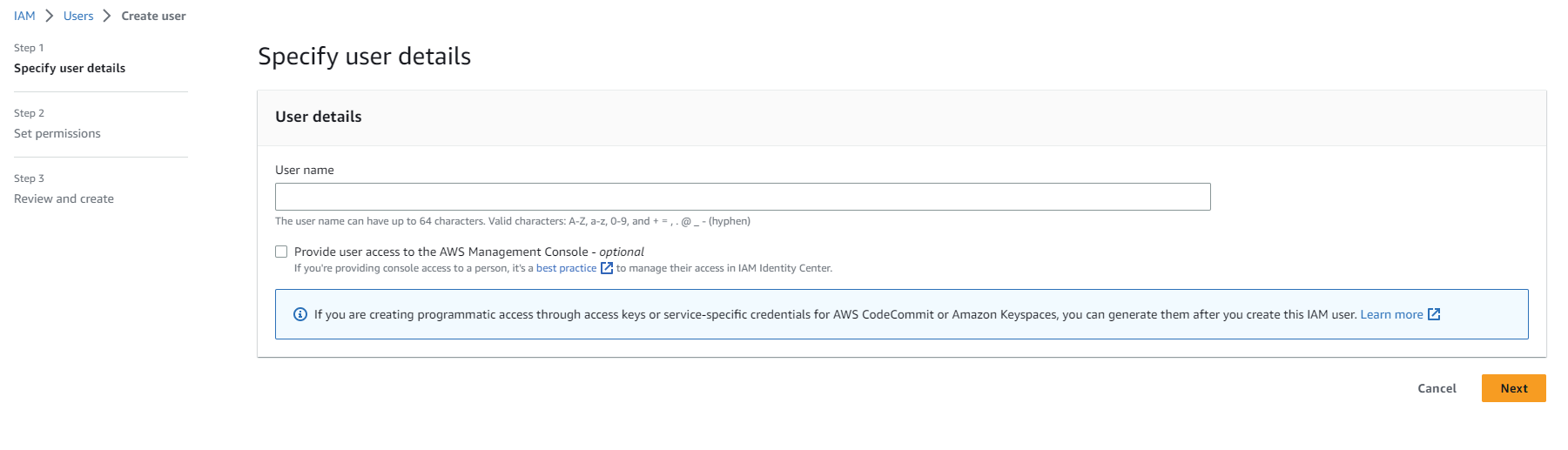
Go to the Users tab and click Create user.
-
In the Username field, enter a name.
Click Next.
-
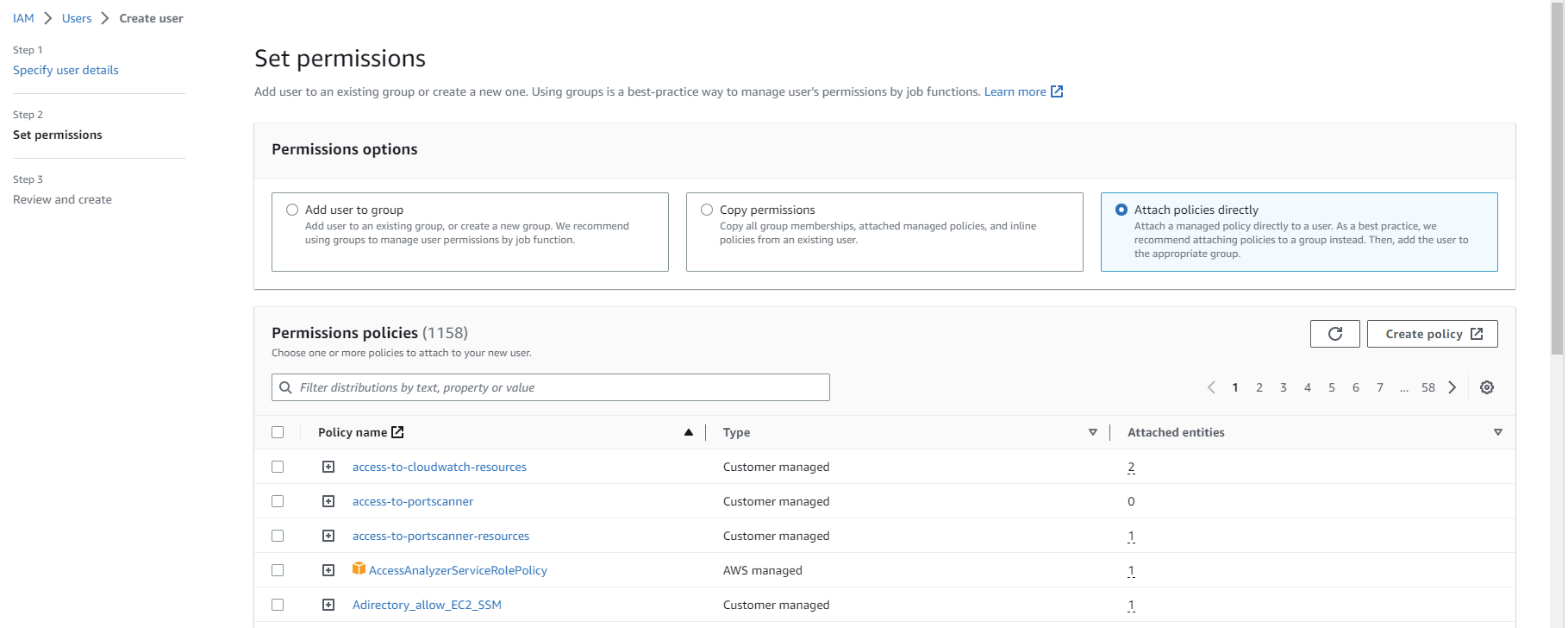
Click Attach policies directly and select the policy you created earlier.
If you have granted full access, then select the S3 full access AWS managed policy.
-
Click Next.
Step 4 - Creating an AWS Access Key
-
Log in to the AWS Management Console.
-
Open the AWS Identity and Access Management (IAM) dashboard.
-
Go to the Users tab and select the user you have created.
-
Click the Security credentials tab.
-
Scroll down to Access keys and click Create access key.
-
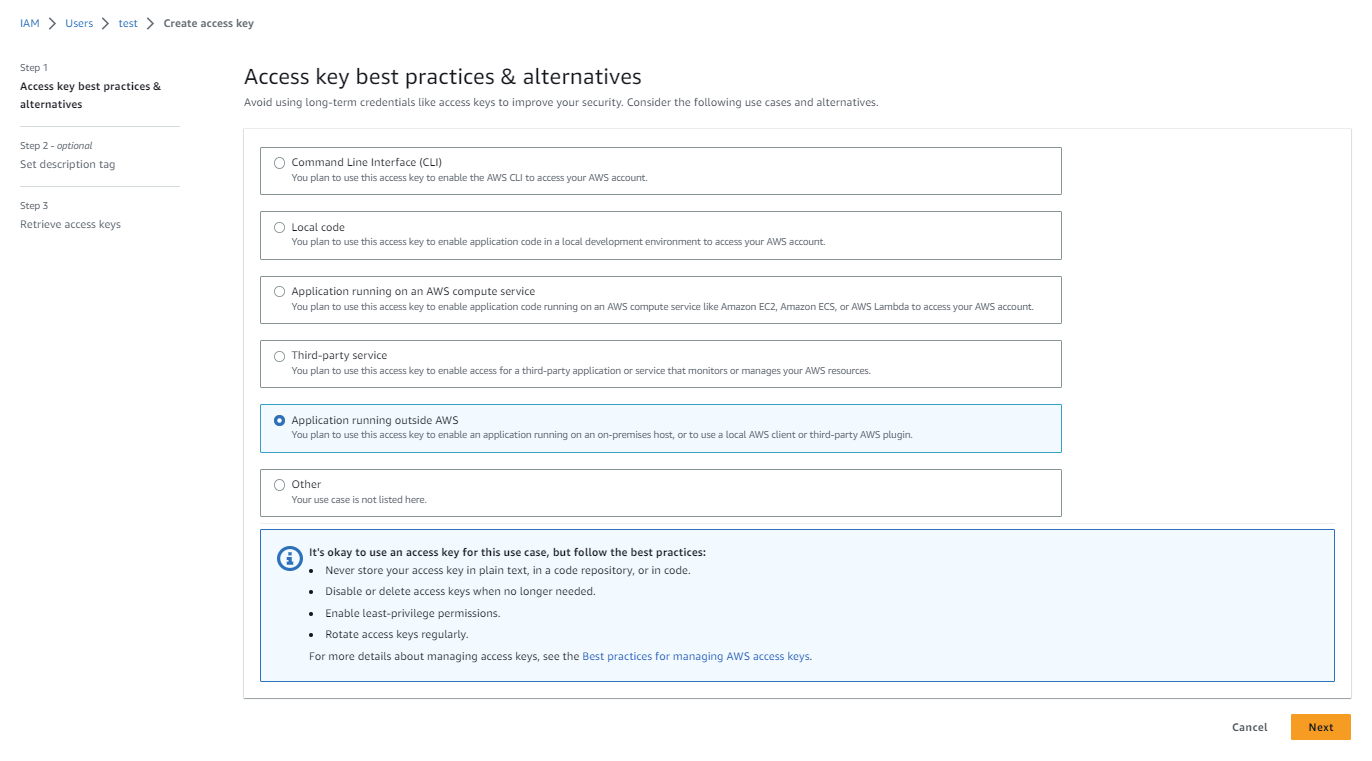
Select Application running outside AWS and click Next.
-
Select Create access key.
-
Description tag is optional.
-
Copy the Secret access key and the Access key.
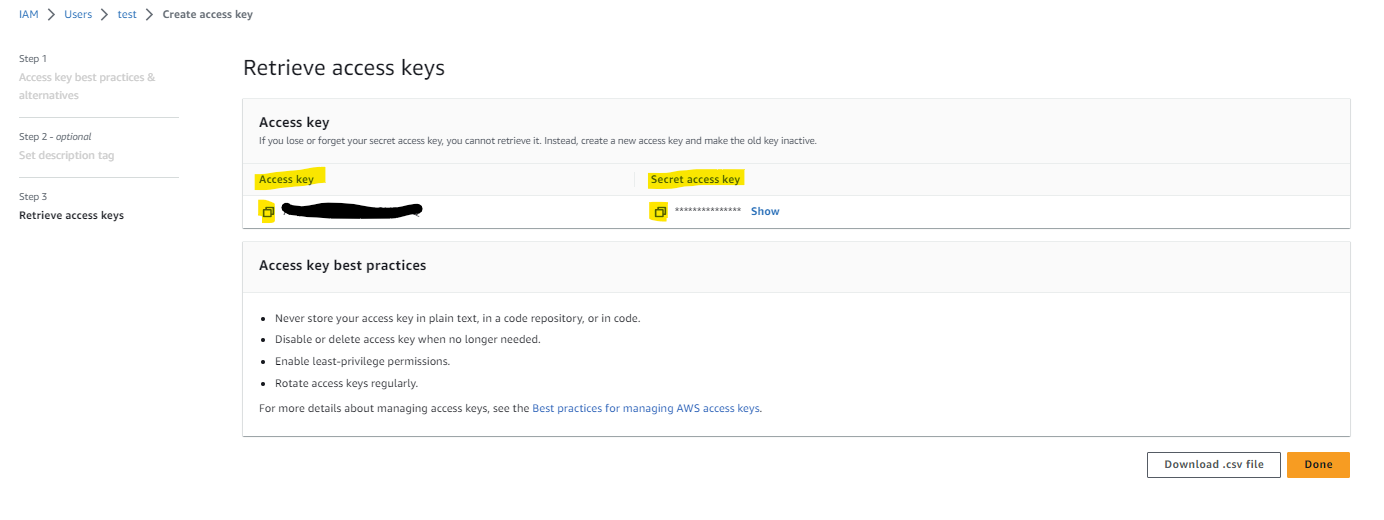
-
Click Done.
Configuring the Amazon S3 Integration in the Harmony SASE Administrator Portal
-
Access the Harmony SASE Administrator Portal and click Settings > Integrations.
-
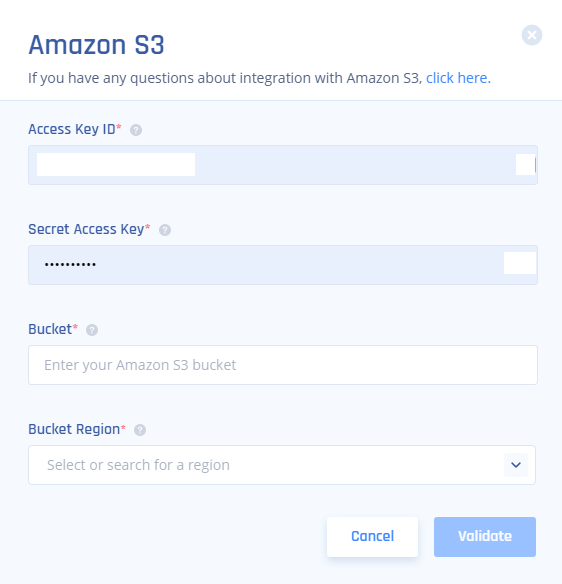
In the SIEM integrations section, in the Amazon S3 row, click Add.
The Amazon S3 window appears.
-
In the Access Key ID field, enter the Access key copied from AWS console.
-
In the Secret Access Key field, enter the Secret access key copied from AWS console.
-
In the Bucket field, enter the Amazon S3 bucket name (for example in this case, arn:aws:s3:::test, the bucket name is test)
-
In the Bucket region field, enter the region selected when you created the Amazon S3 bucket.
-
Click Validate.
Troubleshooting
| Status message | Action required |
|---|---|
| Success | None |
| S3_INVALID_ACCESS_KEY_ID | Make sure you copied the correct access key ID. |
| S3_INVALID_SECRET_ACCESS_KEY | Make sure you copied the correct secret access key. |
| S3_INVALID_BUCKET | Make sure the Bucket name in Harmony SASE matched the Bucket name in Amazon S3 (case sensitive). |
| S3_ACCESS_DENIED_BUCKET |
The IAM user does not have the required access permissions to the bucket. Make sure to attach the appropriate policy. |