Check Point Infinity NDR for AWS
Overview
Infinity NDR![]() Network Detection and Response automatically deploys a Check Point CloudGuard Network Security instance in Monitor Mode into your AWS
Network Detection and Response automatically deploys a Check Point CloudGuard Network Security instance in Monitor Mode into your AWS![]() Amazon® Web Services. Public cloud platform that offers global compute, storage, database, application and other cloud services. VPC
Amazon® Web Services. Public cloud platform that offers global compute, storage, database, application and other cloud services. VPC![]() Virtual Private Cloud through an AWS CloudFormation stack. The stack registers Lambdas (serverless compute instances) that use cloud-native APIs to provision cloud vendor traffic mirroring, to selectively mirror network traffic for analysis and threat detection. The sensors do not require any configuration and do not affect the traffic flow.
Virtual Private Cloud through an AWS CloudFormation stack. The stack registers Lambdas (serverless compute instances) that use cloud-native APIs to provision cloud vendor traffic mirroring, to selectively mirror network traffic for analysis and threat detection. The sensors do not require any configuration and do not affect the traffic flow.
Terminology
-
VPC
-
Region and Availability Zone (AZ
 Availability Zone)
Availability Zone) -
Traffic Mirroring
-
Elastic Network Interfaces (ENI
 Elastic Network Interface)
Elastic Network Interface) -
Elastic Load Balancing (ELB/NLB)
-
Lambda
-
CloudFormation
-
CloudWatch
-
Identity and Access Management (IAM)
If you are new to AWS, see Getting Started with AWS.
Scoping and Costs
Your AWS estate is allocated to accounts, regions, and VPCs. The Check Point Infinity NDR solution monitors network traffic between, into, and out of EC2 compute instances. Each EC2 instance is defined in one VPC and AZ and communicates with one or more ENIs.
NDR uses cloud-native AWS Traffic Mirroring to receive network traffic for inspection. A CloudGuard Network Security (CG![]() CloudGuard NS) instance functions as an NDR sensor through the CloudFormation stack. An AWS Network Load Balancer (NLB) is used in addition in front of the CG NS. Traffic mirroring is configured for a specific VPC and AZ to the NLB when mirroring sessions are created from all ENIs that match a mirroring policy. The NLB routes the mirrored traffic to the NDR sensor.
CloudGuard NS) instance functions as an NDR sensor through the CloudFormation stack. An AWS Network Load Balancer (NLB) is used in addition in front of the CG NS. Traffic mirroring is configured for a specific VPC and AZ to the NLB when mirroring sessions are created from all ENIs that match a mirroring policy. The NLB routes the mirrored traffic to the NDR sensor.
Traffic Mirroring on a per-mirrored ENI basis costs approximately $11/month for each ENI. (Pricing varies across different AWS regions.)
Required Resources for the AWS Account
Step 1: Preparing your AWS account
-
Make sure you know which VPCs and AZs you mirror, and that you have sufficient IAM permissions to provision the NDR components. Missing permissions cause a failure in the environment, and error messages appear on the AWS Console.
-
Use the region selector in the navigation bar to select the AWS region where you want to deploy the NDR instance on AWS.
-
You must have an SSH key pair in your preferred region.
-
If necessary, request a service limit increase for the AWS resources that you plan to use.
By default this guide uses:-
c5.xlarge for the Infinity NDR instances
-
-
The Infinity NDR Indicator Management instance is deployed into an existing VPC with existing workloads. You must create two subnets for use by Infinity NDR. These subnets must be in the same Availability Zone in the region:
-
1 internal subnet for the Infinity NDR Indicator Management instance's interface to receive traffic mirroring.
-
1 external subnet with Internet access for the instance to send logs to the Infinity NDR Indicator Management portal.
-
-
The external subnet must present a route out to the Internet. If it is placed behind a network Security Gateway
 Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources., the Infinity NDR instance can be allocated a local AWS IP
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources., the Infinity NDR instance can be allocated a local AWS IP Internet Protocol address. Otherwise you must configure an Elastic IP (EIP) for the Infinity NDR instance for direct outbound access.
Internet Protocol address. Otherwise you must configure an Elastic IP (EIP) for the Infinity NDR instance for direct outbound access.
Step 2: Subscribing to CloudGuard Network Security in AWS Marketplace
To deploy a Check Point Infinity NDR Sensor, you must first subscribe your AWS account to Check Point CloudGuard Network Security:
-
Log in to AWS Marketplace.

Note - You must have AWS-marketplace "Subscribe IAM" permission.
-
Select the BYOL
 Bring Your Own License licensing option for the Check Point CloudGuard Network Security:
Bring Your Own License licensing option for the Check Point CloudGuard Network Security:See CloudGuard Network Security with Threat Prevention & SandBlast BYOL.
-
If the account is already subscribed, a message appears at the top of this AWS Marketplace page that the AWS account is already entitled:
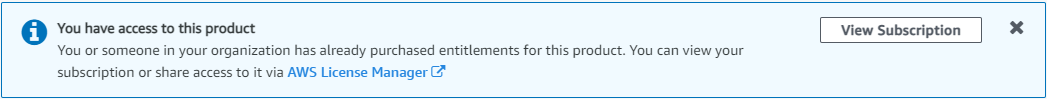
-
If you are not subscribed, select Continue to subscribe.
-
Click Accept Terms to accept the AWS Marketplace license agreement.
Launch in AWS
After you complete all the preparations, you can continue to deploy the sensor.
-
Log in to the Infinity NDR portal and go to the Customer Domain.
If there are no sensors on the domain, it opens on the Sensors tab.
-
From the left-hand menu, select Management > Sensors > Click New (top middle), then select Virtual and enter a name and a description for the sensor.
-
Select the correct time zone and click ADD in the lower right corner.
-
Select the new sensor entry and click Actions > LAUNCH IN AWS.
-
A registration key is created for the new virtual sensor and launches an AWS CloudFormation template in a new browser tab. You are redirected to log in to your AWS account.
|
|
Note - The Infinity NDR application portal does not receive or store customers AWS credentials. |
Infinity NDR CloudFormation Template
-
AWS General Configuration
Enter these parameters before you create the stack:
-
Stack Name: Automatically generated based on the sensor name. You can change this name to identify the sensors AZ.
If you relaunch the stack due to an error, for example, missing IAM permissions, we recommend that you change this name to prevent resource collision in case the previous stack did not complete the automated clean up operations.
-
VPC where you want to deploy the Infinity NDR instance.
-
Availability zone - A Infinity NDR instance must be deployed in each monitored AZ to prevent AWS inter-AZ network traffic mirroring costs.
-
AZ External subnet - This subnet must have access to the Internet (directly or routed through other networks).
In particular, the network must be able to pass TCP port 443 traffic to these IP addresses: 3.64.14.68 and 35.156.213.136. If there is an outbound proxy, it must exempt HTTPS traffic inspection to these addresses.
-
AZ Internal subnet - The mirrored traffic is delivered to an Infinity NDR instance's VXLAN endpoint on this subnet. It can be the same as the AZ External subnet.

Note - Make sure the selected subnets are compatible with the selected availability zone.
-
-
Infinity NDR Sensor Configuration
Enter these parameters before you create the stack:
-
EC2 Instance type - AWS instance size used for the NDR sensor instance.
The default is c5.xlarge. A sensor that is too large has greater AWS costs. An undersized sensor provides reduced visibility because of uninspected connections and may in extreme cases become unstable and disconnect from the Infinity NDR Indicator Management back end.
The primary sizing consideration is the volume of traffic mirrored to the sensor for inspection. See Appendix A for guidelines on how to estimate traffic volumes in AWS, with AWS CloudWatch.
For a rough guide on how to select the instance type:
AWS instance type
c5.large
c5.xlarge
c5.2xlarge
c5.4xlarge
c5.9xlarge
# vCores
2
4
8
16
32
Max total traffic/sec
~0.5 Gbps
~1 Gbps
~2 Gbps
~4 Gbps
~8 Gbps
-
EC2 key name - AWS security key pair for SSH access to the Infinity NDR Indicator Management instance. Usually, this key is not used, but you must enter a key pair for the instance deployment. There is no default.
-
Allocate EIP - By default, this attribute is set to No as in most customer VPCs the Infinity NDR Indicator Management EC2 instance created on the AZ External subnet receives an internal AWS IP address and a default gateway for outbound connectivity. Set this to Yes if you must allocate the AWS Elastic IP on the instance for direct Internet access.
Procedure for Resizing an Infinity NDR Sensor on AWS
For an activated sensor (in v state), in case it is undersized or too large and it is necessary to change instance Type, follow these steps to relaunch it with the new size:
-
On AWS, remove the stack. This will clean up all resources consumed by the Infinity NDR Indicator Management solution.
-
On the Infinity NDR application portal - on the MANAGEMENT > Sensors tab
-
Select the sensor entry (it shows as "Disconnected" - grey lightbulb icon)
-
Click on Actions > X DEACTIVATE
-
Click on Actions > LAUNCH IN AWS
-
-
Fill in the CloudFormation Template with the new parameters.

Note - We recommend that you make sure that the used stack is deleted before you launch the new one, or to manually change the stack name to prevent named collisions on deployed AWS resources.
-
-
CG NDR Configuration - Advanced
These parameters all have applicable default values, and it is not necessary to change them. They provide advanced Infinity NDR Sensor configuration.
-
Expiration period - Time after which the stack is automatically deleted. This releases all AWS resources allocated for this stack. Default is No expiration.
-
Include EC2 Instances with the following tags (default all) - Use to constrain the set of mirrored EC2 instances with a comma-separated list of Key=Value AWS tags.
-
Exclude EC2 Instances with the following tags (default none) - Use to further limit the set of mirrored EC2 instances.
-
Monitor all ENIs - For multi-homed EC2 instances, if you set this parameter to No, it monitors only the primary ENI.
-
VXLAN ID - VTEP number for mirroring sessions. Usually set to the default value of 1.
-
VPC scan interval - Default is 10 minutes.
-
Version - Do not change.
-
Registration key - Do not change.
-
-
Confirmation and Stack Creation
Examine the acknowledgment and click Create stack.
The CloudFormation Template (CFT
 CloudFormation template) spins up the Infinity NDR Indicator Management instance in your selected VPC and AZ, and runs two lambda functions that provision AWS traffic mirroring.
CloudFormation template) spins up the Infinity NDR Indicator Management instance in your selected VPC and AZ, and runs two lambda functions that provision AWS traffic mirroring.It typically takes up to 20 minutes before you start seeing logs on the Infinity NDR application portal. The sensor's icon on the portal changes to a green light-bulb icon with a v status. You can track the CFT progress in the AWS Console, including any applicable error messages.
-
AWS Resources Provisioned by the CFT
-
A security group is created for each ENI:
-
Internal ENI - Allow incoming vxlan (udp 4789), reject outbound.
-
External ENI - Allow incoming ssh/https (tcp 22/443), allow outbound.
-
-
AWS Traffic Mirroring sources and sessions for each mirrored ENI.
-
AWS Network Load Balancer (NLB), defined as the mirroring target, routes mirrored traffic to the NDR sensor instance on the defined VXLAN on the AZ Internal subnet.
-
Two lambda functions automatically configure AWS traffic mirroring. An EC2 instance creation event on the VPC triggers its examination against the mirroring policy (include and exclude lists). In addition, the VPC is scanned on the defined scan interval, and any deleted EC2 instances result in clean up of the corresponding mirroring sources and sessions. EventBridge rules control these invocations.
-
Elastic IP if enabled in the CFT.

Note - If you remove the stack from the AWS Console - it removes all related resources in your VPC, including the Infinity NDR Indicator Management CloudGuard Network Security instance, the lambda functions, and the traffic mirroring sessions.
-
Mirroring More VPCs
The LAUNCH IN AWS CFT provisions traffic mirroring for a specified VPC and AZ, and mirrors the traffic to a Load Balancer and Infinity NDR Sensor.
There is an alternative PROVISION AWS MIRRORING CFT that does not create those two instances. Instead, it accepts the mirroring target as a parameter. It allows one deployed NDR sensor to mirror traffic from multiple VPCs. As long as the sensor and the mirrored traffic are defined in the same Availability Zone, there are no additional AWS costs related to inter-VPC or even inter-account traffic mirroring.
|
|
Note - We recommend that you do not mirror across AZ boundaries even though there is no technical limitation. AWS costs grow significantly if traffic is mirrored between different AZs. |
To provision mirroring on a different VPC:
-
From the left-hand menu, select Management > Sensors > Click New (top middle), then clear Managed and enter a description/name for the sensor.
-
Select the correct time zone and click ADD in the lower right corner.
-
Select the new sensor entry and click Actions > PROVISION AWS MIRRORING.
This step launches an AWS CloudFormation template in a new browser tab. It first redirects you to log in to the customer's AWS account. Enter your AWS account number and access credentials to log in to your AWS Console.
-
The CFT parameters are equivalent to those of LAUNCH IN AWS, with these exceptions:
-
As no sensor is deployed, the CFT omits these parameters: AZ External Subnet, AZ Internal Subnet, the entire CG NDR Configuration section, Version, Registration key
-
A Traffic Mirror Target parameter is added. Enter a Infinity NDR Indicator Management Load Balancers mirror target ID
 Identifier (for example 'tmt-xxxxxx').
Identifier (for example 'tmt-xxxxxx').
-
-
Check the acknowledgment and click Create stack.
Traffic Mirroring Include/Exclude Lists
The Infinity NDR Indicator Management Cloud Formation template, which is deployed per sensor from the Infinity NDR portal, handles the traffic mirroring include and exclude lists. To include or exclude instances for traffic mirroring, enter comma-separated key-value pairs in the CFT, for example:
-
MYTAG=DOMIRROR,MYOTHERTAG=INSTANCE.
-
CKP_TYPE = Sensor
Apply these tags to each instance to include or exclude them from traffic mirroring.
To update your traffic mirroring include/exclude tags after initial CFT deployment, issue a CFT Stack update to revise the tags or to apply a different tag scan interval.
-
Find the CloudFormation Stack used to deploy your sensor, select the Change Sets tab, and click Create Change Set.
-
Select Use the current template and click Next.
-
Change the Include or Exclude tags as applicable, or change the VPC Scan interval, or both. Click Next.
-
Do not make any changes in the stack options and click Next.
-
At the review screen, examine all parameters, then acknowledge the stack capabilities and click Create Change Set.
-
Give the change set a name and click Create Change Set to make the changes to the applicable Infinity NDR sensors.
Sensor Deactivation on Stack Deletion
If you want to remove the Cloudformation Stack which deployed your NDR Sensor, and relaunch in AWS from the Infinity NDR application portal, you must first deactivate the sensor on the portal. This is because the Infinity NDR back end does not know if the sensor is deactivated, only that it is disconnected.
To deactivate the sensor:
-
On the MANAGEMENT > Sensors tab, select the applicable sensor.
-
From the Actions menu select X DEACTIVATE.
