NDR Security Check-up Report
Overview
The NDR![]() Network Detection and Response Web application lets users easily create a Security Check-up report and other more specialized reports.
Network Detection and Response Web application lets users easily create a Security Check-up report and other more specialized reports.
When it is necessary, you can approve more users to see this information on the application.
After the NDR sensor completes activation, it starts to send logs generated by the different Check Point software blades. By default, these include Threat Prevention (Anti-Bot![]() Check Point Software Blade on a Security Gateway that blocks botnet behavior and communication to Command and Control (C&C) centers. Acronyms: AB, ABOT., Anti-Virus
Check Point Software Blade on a Security Gateway that blocks botnet behavior and communication to Command and Control (C&C) centers. Acronyms: AB, ABOT., Anti-Virus![]() Check Point Software Blade on a Security Gateway that uses real-time virus signatures and anomaly-based protections from ThreatCloud to detect and block malware at the Security Gateway before users are affected. Acronym: AV., IPS
Check Point Software Blade on a Security Gateway that uses real-time virus signatures and anomaly-based protections from ThreatCloud to detect and block malware at the Security Gateway before users are affected. Acronym: AV., IPS![]() Check Point Software Blade on a Security Gateway that inspects and analyzes packets and data for numerous types of risks (Intrusion Prevention System)., Threat Emulation
Check Point Software Blade on a Security Gateway that inspects and analyzes packets and data for numerous types of risks (Intrusion Prevention System)., Threat Emulation![]() Check Point Software Blade on a Security Gateway that monitors the behavior of files in a sandbox to determine whether or not they are malicious. Acronym: TE.) and Access blades (Firewall, Application Control
Check Point Software Blade on a Security Gateway that monitors the behavior of files in a sandbox to determine whether or not they are malicious. Acronym: TE.) and Access blades (Firewall, Application Control![]() Check Point Software Blade on a Security Gateway that allows granular control over specific web-enabled applications by using deep packet inspection. Acronym: APPI., URL Filtering
Check Point Software Blade on a Security Gateway that allows granular control over specific web-enabled applications by using deep packet inspection. Acronym: APPI., URL Filtering![]() Check Point Software Blade on a Security Gateway that allows granular control over which web sites can be accessed by a given group of users, computers or networks. Acronym: URLF.). These logs stay on the customer's domain even after the sensor is deactivated.
Check Point Software Blade on a Security Gateway that allows granular control over which web sites can be accessed by a given group of users, computers or networks. Acronym: URLF.). These logs stay on the customer's domain even after the sensor is deactivated.
Generating an NDR Report
-
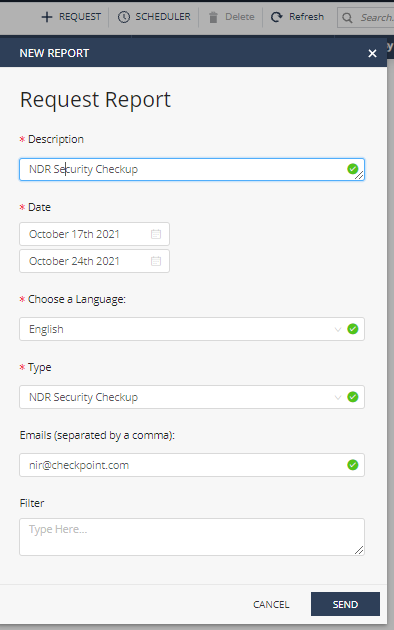
Browse to the Reports tab.
-
Click + REQUEST to submit a new report request.
-
Enter a Description for the report.
-
The Date range defaults to the last 7 days - this is typically sufficient for a Security Check-up.
-
Keep the Language setting as English - currently the only supported language.
-
Select the report Type: NDR Security Checkup or Security Checkup - Advanced (see below).
-
Enter your email address to send the report to.
-
Optionally enter a Filter. This is typically used to not include uninteresting data, or to focus on a specific part of the network.
-
Click SEND to send the report request.
-
After some minutes, you receive the report in your mailbox, and it is displayed in the Reports tab on the portal.
NDR Report Types for Security Check-up
-
Security Checkup - Advanced –Includes the findings of a variety of security threats: malware infections, usage of high risk web applications, intrusion attempts, loss of sensitive data, etc.
-
NDR Security Checkup – Customized and scoped report for NDR, that includes the findings of a security estimate conducted in your network leveraging AI
 Artificial Intelligence insights and threat analytics.
Artificial Intelligence insights and threat analytics.
Generating a Threat Topology Report
One of the advanced analytical tools on the NDR portal is the Threat Topology visualization. Threat Topology let you map network interactions and prioritize different event types.
To export a Threat Topology visualization for presentation out of the portal:
On ANALYTICS > Threat Topology, click Export HTML (bottom right)
This generates a report in HTML![]() HyperText Markup Language archive format, that you can send to the customer. Opening the report object provides an offline interactive experience that is equivalent to the one on the NDR application.
HyperText Markup Language archive format, that you can send to the customer. Opening the report object provides an offline interactive experience that is equivalent to the one on the NDR application.
