NDR Log Server Registration
Overview
If you have a Check Point Log Server![]() Dedicated Check Point server that runs Check Point software to store and process logs., you can use the Check Point Log Exporter (sk122323) to send your logs to the NDR
Dedicated Check Point server that runs Check Point software to store and process logs., you can use the Check Point Log Exporter (sk122323) to send your logs to the NDR![]() Network Detection and Response Indicator Management application in addition to or instead of using dedicated NDR Sensors. The NDR application receives the Log Exporter configuration, downloads it to the Log Server, and executes it with one command.
Network Detection and Response Indicator Management application in addition to or instead of using dedicated NDR Sensors. The NDR application receives the Log Exporter configuration, downloads it to the Log Server, and executes it with one command.
Prerequisites
-
The Log Server must run version R80.30 or higher.
-
If you have a firewall, it must allow the appliance's Management interface to connect through TCP port 443 to these IP
 Internet Protocol addresses: 35.156.213.136, 3.120.103.74, and 18.196.115.85 (for NDR Portal).
Internet Protocol addresses: 35.156.213.136, 3.120.103.74, and 18.196.115.85 (for NDR Portal). -
The Log Server uses TLS to authenticate to the NDR application portal. Therefore, if you use HTTPS Inspection
 Feature on a Security Gateway that inspects traffic encrypted by the Secure Sockets Layer (SSL) protocol for malware or suspicious patterns. Synonym: SSL Inspection. Acronyms: HTTPSI, HTTPSi. on the outbound path, you must create an exception for the log export traffic from the Log Server.
Feature on a Security Gateway that inspects traffic encrypted by the Secure Sockets Layer (SSL) protocol for malware or suspicious patterns. Synonym: SSL Inspection. Acronyms: HTTPSI, HTTPSi. on the outbound path, you must create an exception for the log export traffic from the Log Server. -
You must create an HTTPS Inspection exception to access the NDR Portal.
-
You must enable Extended Logging for the Application Control
 Check Point Software Blade on a Security Gateway that allows granular control over specific web-enabled applications by using deep packet inspection. Acronym: APPI. and URL Filtering
Check Point Software Blade on a Security Gateway that allows granular control over specific web-enabled applications by using deep packet inspection. Acronym: APPI. and URL Filtering Check Point Software Blade on a Security Gateway that allows granular control over which web sites can be accessed by a given group of users, computers or networks. Acronym: URLF. blades on your Check Point Security Gateways. Other recommended blades include IPS
Check Point Software Blade on a Security Gateway that allows granular control over which web sites can be accessed by a given group of users, computers or networks. Acronym: URLF. blades on your Check Point Security Gateways. Other recommended blades include IPS Check Point Software Blade on a Security Gateway that inspects and analyzes packets and data for numerous types of risks (Intrusion Prevention System)., Anti-Bot
Check Point Software Blade on a Security Gateway that inspects and analyzes packets and data for numerous types of risks (Intrusion Prevention System)., Anti-Bot Check Point Software Blade on a Security Gateway that blocks botnet behavior and communication to Command and Control (C&C) centers. Acronyms: AB, ABOT., Anti-Virus
Check Point Software Blade on a Security Gateway that blocks botnet behavior and communication to Command and Control (C&C) centers. Acronyms: AB, ABOT., Anti-Virus Check Point Software Blade on a Security Gateway that uses real-time virus signatures and anomaly-based protections from ThreatCloud to detect and block malware at the Security Gateway before users are affected. Acronym: AV., and Threat Emulation
Check Point Software Blade on a Security Gateway that uses real-time virus signatures and anomaly-based protections from ThreatCloud to detect and block malware at the Security Gateway before users are affected. Acronym: AV., and Threat Emulation Check Point Software Blade on a Security Gateway that monitors the behavior of files in a sandbox to determine whether or not they are malicious. Acronym: TE..
Check Point Software Blade on a Security Gateway that monitors the behavior of files in a sandbox to determine whether or not they are malicious. Acronym: TE..
Configuring the Sensors in the NDR Application Portal
To configure the NDR sensors:
-
Log in to the NDR Portal.
-
Go to the Customer Domain.
If there are no sensors on the domain, it opens the Sensors tab.
-
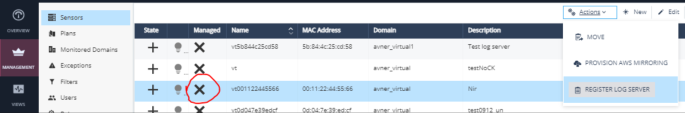
From the left-hand menu, select Management > Sensors > click New (top middle).
-
To create an unmanaged sensor, clear the NDR Managed checkbox. Do not enter a MAC address.
-
Enter a description/name for the sensor. Select the correct time zone.
-
If the Log Server is a Multi-Domain Log Server
 Dedicated Check Point server that runs Check Point software to store and process logs in a Multi-Domain Security Management environment. The Multi-Domain Log Server consists of Domain Log Servers that store and process logs from Security Gateways that are managed by the corresponding Domain Management Servers. Acronym: MDLS., enable Multi-Domain Log Server (MDS) and enter the applicable Domain Log Server name and IP address.
Dedicated Check Point server that runs Check Point software to store and process logs in a Multi-Domain Security Management environment. The Multi-Domain Log Server consists of Domain Log Servers that store and process logs from Security Gateways that are managed by the corresponding Domain Management Servers. Acronym: MDLS., enable Multi-Domain Log Server (MDS) and enter the applicable Domain Log Server name and IP address.For each Domain Management Server
 Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server. on a Multi-Domain Security Management Server
Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server. on a Multi-Domain Security Management Server Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server. that is to be exported to NDR, you must assign an individual NDR sensor.
Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server. that is to be exported to NDR, you must assign an individual NDR sensor. -
Click ADD in the lower right corner of the new sensor form.
-
Click on the new sensor entry you created and select REGISTER LOG EXPORTER from the Actions menu.
-
In the confirmation window, click CONTINUE.
-
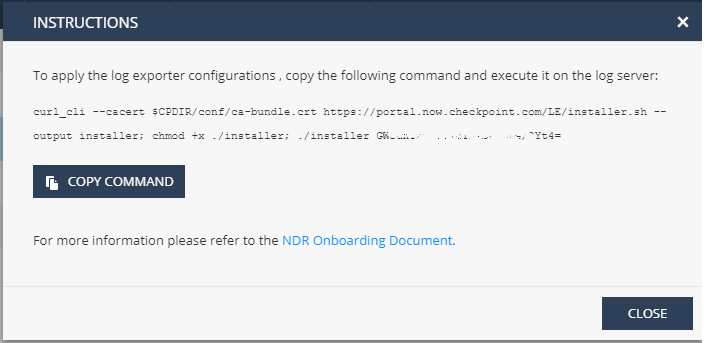
Click COPY COMMAND to copy the personalized script to your clipboard:
Registering the Log Server
To register the Log Server:
-
Connect to the command line on the Log Server.
-
Log in to the Expert mode.
-
Paste the personalized script and click Enter.
-
The script executes and a "good day" message appears.
If an error message appears, contact Check Point Support.
-
When logs start to move to the NDR, the light bulb icon next to the sensor turns green: