Integrating Infinity Identity with Microsoft Intune and Microsoft Defender
Infinity Identity can query Microsoft Entra ID to get identity information based on sign-in events from Microsoft Intune or Microsoft Defender on endpoint computers. When you export sign-in events to Event Hubs, Infinity Identity retrieves identities in a way that minimizes resource usage, reduces time delays, and ensures reliable access to the necessary data.
Prerequisites:
-
An Microsoft Entra ID IdP (Manual Sync) connected to Infinity Identity. See Microsoft Entra ID (formerly Azure AD).
-
Active Event-Hubs in Microsoft Entra ID with a Namespace and two partitions. Refer to the Quickstart guide to create an Event Hub using the Azure portal.
-
Active Storage account in Microsoft Entra ID. Refer to Microsoft documentation to create a storage account and disable the soft delete for blobs and containers.
Configuring Entra ID Query to Send Identities from Microsoft Defender or Intune to Infinity Identity
Watch this video for a full demonstration.
-
In Infinity Identity, from the left toolbar, click Integrations.
-
In the Integrations section, click the + (plus sign) button.
-
Select Identity Integrations.
-
Select Microsoft Intune or Microsoft Defender. If you want to integrate both of them, it does not matter which one you select.
The Microsoft Intune or Microsoft Defender integration window opens.
-
For the Integration Title, enter a tile. After you create the integration, this title appears in the Infinity Identity Integrations section.
-
Optional - If you want to integrate both Intune and Defender, select the relevant checkbox at the bottom of the window.
-
In a Microsoft Intune window, select Use this configuration to create Microsoft Defender integration as well.
-
In a Microsoft Defender window, select Use this configuration to create Microsoft Intune integration as well.
-
-
Keep Infinity Identity open.
-
In a new browser tab, open the Microsoft Entra ID application that you integrated with the Infinity Portal.
-
In the left menu, expand Manage and click API permissions.
-
In the Configured permissions section, click Add a permission.
The Request API permissions window opens.
-
Select Application permissions.
-
Add a permission to the application:
-
In the search bar below Select permissions, search for
deviceManage. -
Expand DeviceManagementManagedDevices.
-
Select DeviceManagementManagedDevices.Read.All.
-
-
If you are integrating Microsoft Defender, add another permission to the application:
-
In the search bar below Select permissions, search for
threat. -
Expand ThreatHunting.
-
Select ThreatHunting.Read.All.
-
-
Click Add permissions.
-
In the Configured permissions section, click Grant admin consent for Check Point Software Technologies.
-
In the confirmation window, click Yes.
-
On the Microsoft Azure
 Collection of integrated cloud services that developers and IT professionals use to build, deploy, and manage applications through a global network of data centers managed by Microsoft®. homepage, open Event Hubs.
Collection of integrated cloud services that developers and IT professionals use to build, deploy, and manage applications through a global network of data centers managed by Microsoft®. homepage, open Event Hubs. -
Open the Namespace that you want to use for the application.
-
Copy the name of the Namespace from Microsoft Azure and paste it into the Namespace Name field in Infinity Identity
-
In the Event Hub, from the horizontal toolbar, click Consumer group.
The Create consumer group window opens.
-
In the Create consumer group window:
-
Enter a name for the consumer group.
-
Click Create.
-
-
From the left toolbar, click Access control (IAM).
-
From the top toolbar click Add and then click Add role assignment
The Add role assignment window opens..
-
In the Add role assignment window:
-
In the Roles tab:
-
In the Job function roles section, search for
receiver. -
Select Azure Event Hubs Data Receiver.
-
-
In the Add role assignment window, in theMembers tab:
-
For Assign access to, select User, group, or service principal.
-
Click Select members.
The Select members window opens.
-
In the Select members window, search for the Entra ID application you created for Infinity Identity.
-
In the search results, select the application.
-
At the bottom of the Select members window, click Select.
-
-
In the Add role assignment window, in the Conditions tab, do not change the default configurations.
-
In the Add role assignment window, in the Review + assign tab, make sure the configuration is correct and then click the Review + assign button at the bottom of the window.
-
For more information, see Authorize access to Event Hubs with Azure Active Directory in Microsoft documentation.
-
On the Microsoft Entra ID homepage, in the search bar, search for
Storage Account. -
In the Services section of the search results, click Storage accounts.
-
Open the storage account that you want to use for Infinity Identity.
-
In the storage account window, from the left toolbar, open the Access Control (IAM) tab.
-
In the storage account window, from the top toolbar, click Add and then click Add role assignment.
The Add role assignment window opens.
-
In the Add role assignment window:
-
In the Roles tab:
-
Select Job function roles.
-
In the search bar, search for
owner. -
Click Storage Blob Data Owner.
-
-
In the Members tab:
-
Click + Select members.
The Select members window opens.
-
In the Select members window, in the search bar, enter the name of the Microsoft Entra ID application you created for Infinity Identity.
-
In the search results, select the application.
-
Click Select.
The Select members window closes. The application appears in the Members tab in theAdd role assignment window.
-
-
In the Conditions tab, do not change default settings.
-
In the Review + assign tab, make sure the configuration is correct and then click the Review + assign button at the bottom of the window.
-
You can integrate Intune and/or Microsoft Defender.
-
In the Azure portal, in the search bar, search for "
sign-in". -
Click Sign-in logs.
The Sign-in events window opens.
-
From the top toolbar, click Export Data Settings.
-
Click Add diagnostic setting.
-
Enter a name in the Diagnostic setting name field.
-
In the Logs section, select SigninLogs.
-
In the Destination details section, select Stream to an event hub.
-
For Event hub namespace, select the Namespace that you use for the Infinity Identity application.
-
In the Diagnostic setting window, from the top toolbar, click Save.
For more information, see How to stream activity logs to an Event Hub in Microsoft documentation.
-
In a web browser, go to security.microsoft.com and log in to your account.
-
From the left toolbar, click Settings.
-
In the table, click Microsoft Defender XDR.
-
In the General section, click Streaming API.
-
In the Streaming API section, click + Add.
The Add new Streaming API settings window opens.
-
In theName field, enter a name.
-
Select Forward events to Event Hub.
-
In a separate browser tab, open the Azure portal and do these steps:
-
In the search bar, search for "
event hubs". -
Open the Event Hub that you use for the Microsoft Entra ID application that you created for Infinity Identity.
-
In the Event Hub window, in the left toolbar, expand Settings and click Properties.
-
In the Essentials section, copy the IE string.
-
Keep the Azure portal open.
-
-
At security.microsoft.com, in the Add new Streaming API settings window, paste the IE string you copied from the Azure portal into the Event Hub Resource ID field.
-
In the Azure portal Event Hub window:
-
From the left toolbar, click Overview.
-
At the bottom of the screen, in the Event Hubs table, copy the name of the Event Hub that you use for the Microsoft Entra ID application that you created for Infinity Identity.
-
-
At security.microsoft.com, in the Add new Streaming API settings window:
-
Paste the name that you copied from the Azure portal into the Event-Hub name field.
-
In the Event Types section, expand Devices.
-
Select DeviceNetworkInfo.
-
Select DeviceLogonEvents.
-
Click Submit.
-
|
|
Important - Allow one hour for settings to propagate and take effect. |
-
In Infinity Identity, click Test connectivity to verify the connection between your Infinity Identity account and your Microsoft Entra ID account.
-
If the test passes, then Connectivity test successful shows.
-
If the test fails, a warning message appears that highlights the problematic field in red.
-
-
After a successful test, click Save.
Infinity Identity is integrated with Intune and/or Defender. A card for Microsoft Intune and/or Microsoft Defender appears in the Integrations section.
Finding the Event Hub Namespace, Event Hub Name, Consumer Group Name, and Storage Account Name in Microsoft Azure
-
Log in to your Microsoft Azure portal.
-
Navigate to Event Hubs.
-
In the Event Hubs section, locate and select the specific event hub that you want to configure.
-
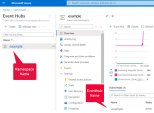
In Event Hub details, you can see the Eventhub Name and the associated Namespace, as shown in this example:
Note - A Name space in Azure can contain multiple Event Hubs, each serving different event streaming purposes. Ensure that you select the correct Event Hubs for your integration. To create an event hub, see Quickstart: Create an event hub using Azure portal.
-
Log in to your Microsoft Azure portal.
-
Navigate to Storage accounts and select the appropriate Storage account from the list.
-
In the selected Storage Account, go to Containers to view and select the desired Storage Name.