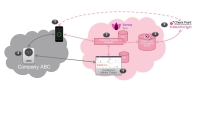
Solution Architecture
|
|
Component |
Description |
|---|---|---|
|
1 |
Harmony Mobile Protect app |
|
|
2 |
|
|
|
3 |
Harmony Mobile Gateway |
|
|
4 |
Harmony Mobile Management Dashboard |
|
|
5 |
Behavioral Risk Engine |
|
|
6 |
ThreatCloud |
|