Deploying the Harmony Mobile Protect app automatically (Zero Touch Deployment) [Optional]
UEM![]() Unified Endpoint Management. An architecture and approach that controls different types of devices such as computers, smartphones and IoT devices from a centralized command point. solutions traditionally prompt the mobile device user to install the application once it is registered. In addition, to get full protection, the user needs to approve the required permissions and profiles. Many users are vigilant about installing new mobile applications or granting different permissions, and as a Security company, Check Point even encourages that. Most of them don’t know that the Harmony Mobile Protect app is focused on device characteristics and behaviors and not the content stored on or flowing through the device. Furthermore, some users are incompliant with the company’s security policy
Unified Endpoint Management. An architecture and approach that controls different types of devices such as computers, smartphones and IoT devices from a centralized command point. solutions traditionally prompt the mobile device user to install the application once it is registered. In addition, to get full protection, the user needs to approve the required permissions and profiles. Many users are vigilant about installing new mobile applications or granting different permissions, and as a Security company, Check Point even encourages that. Most of them don’t know that the Harmony Mobile Protect app is focused on device characteristics and behaviors and not the content stored on or flowing through the device. Furthermore, some users are incompliant with the company’s security policy![]() Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection., especially when they use their own devices. Therefore, users often decide not to install the app or approve the required configuration. On top of that, users who do agree to install and accept the configuration will not often do it immediately, and it will take time until the application is activated. As a result, many devices remain exposed to potential cyber-attacks.
Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection., especially when they use their own devices. Therefore, users often decide not to install the app or approve the required configuration. On top of that, users who do agree to install and accept the configuration will not often do it immediately, and it will take time until the application is activated. As a result, many devices remain exposed to potential cyber-attacks.
Harmony Mobile’s innovative zero-touch technology allows the Protect app to be installed and activated automatically without any user interaction. The solution leverages Check Point’s unique bootstrap technology to establish zero-touch activation.
It is important to note that the following steps of zero-touch deployment are optional. If the organization does not want to force Harmony Mobile to activate itself on employees devices, please skip this chapter.
Zero Touch Deployment in Android Enterprise devices
-
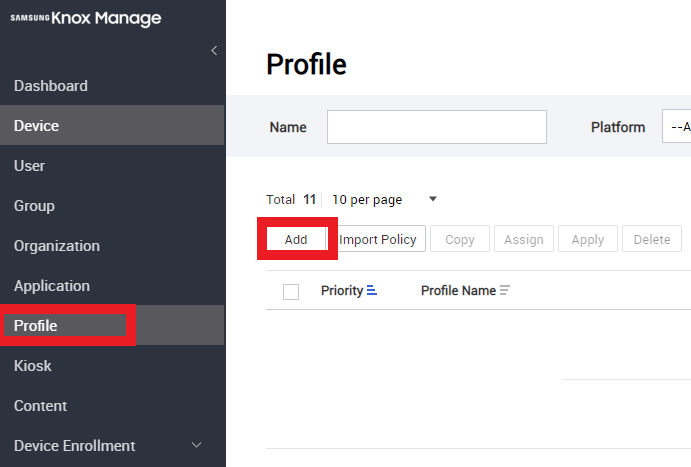
Create a new Profile.
Go to Profile > Add.
-
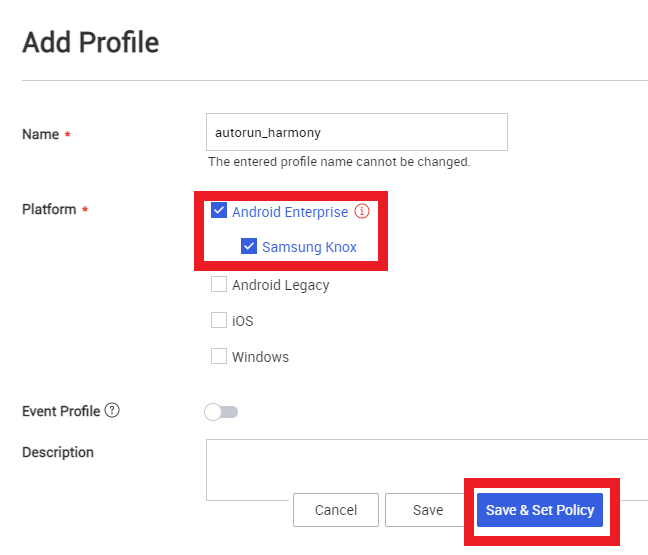
Select Android Enterprise and Samsung Knox, then click Save & Set Policy.
-
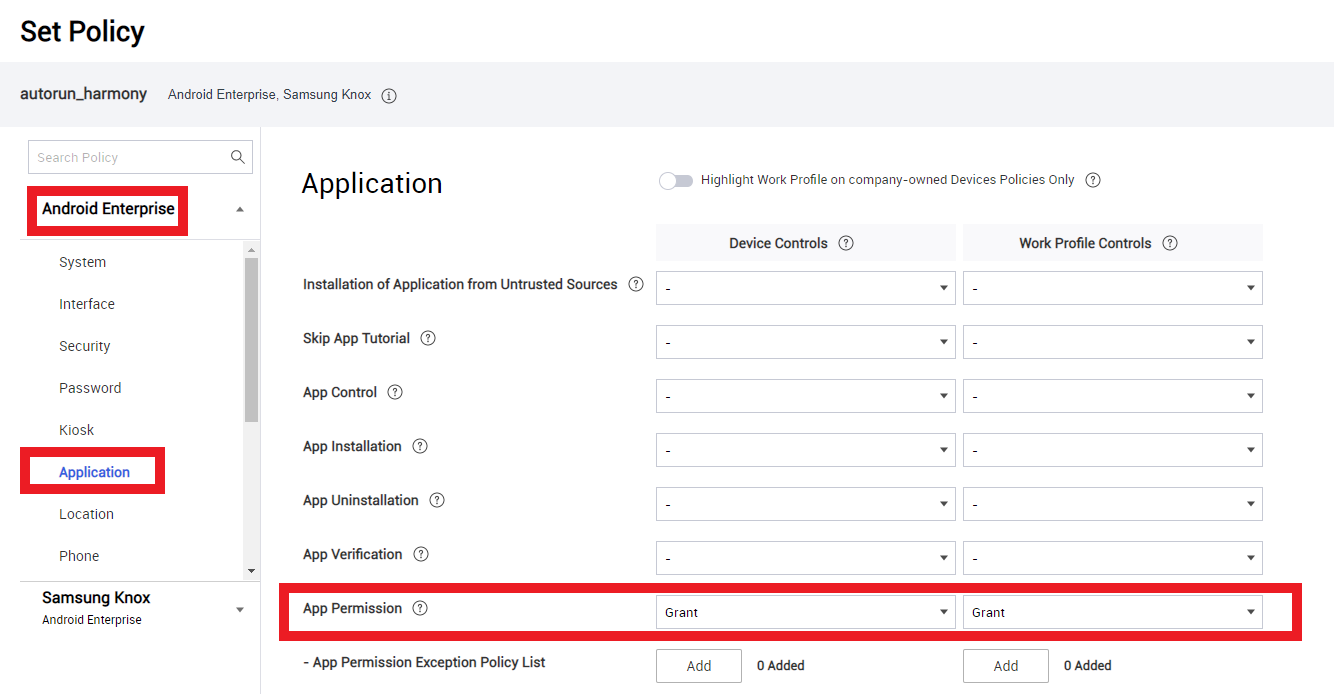
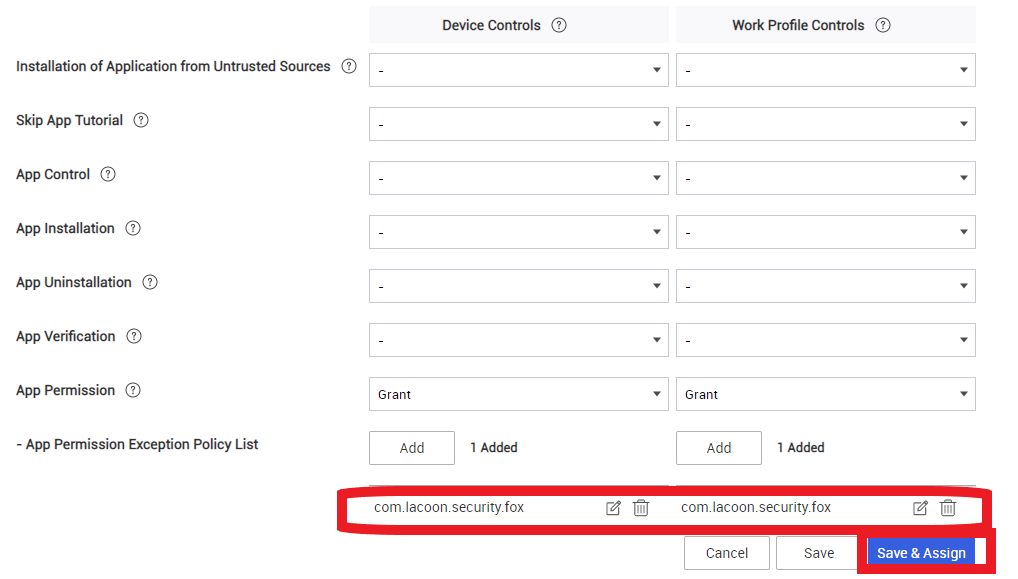
Under Android Enterprise > Application, select Grant for both Device Controls and Work Profile Controls.
-
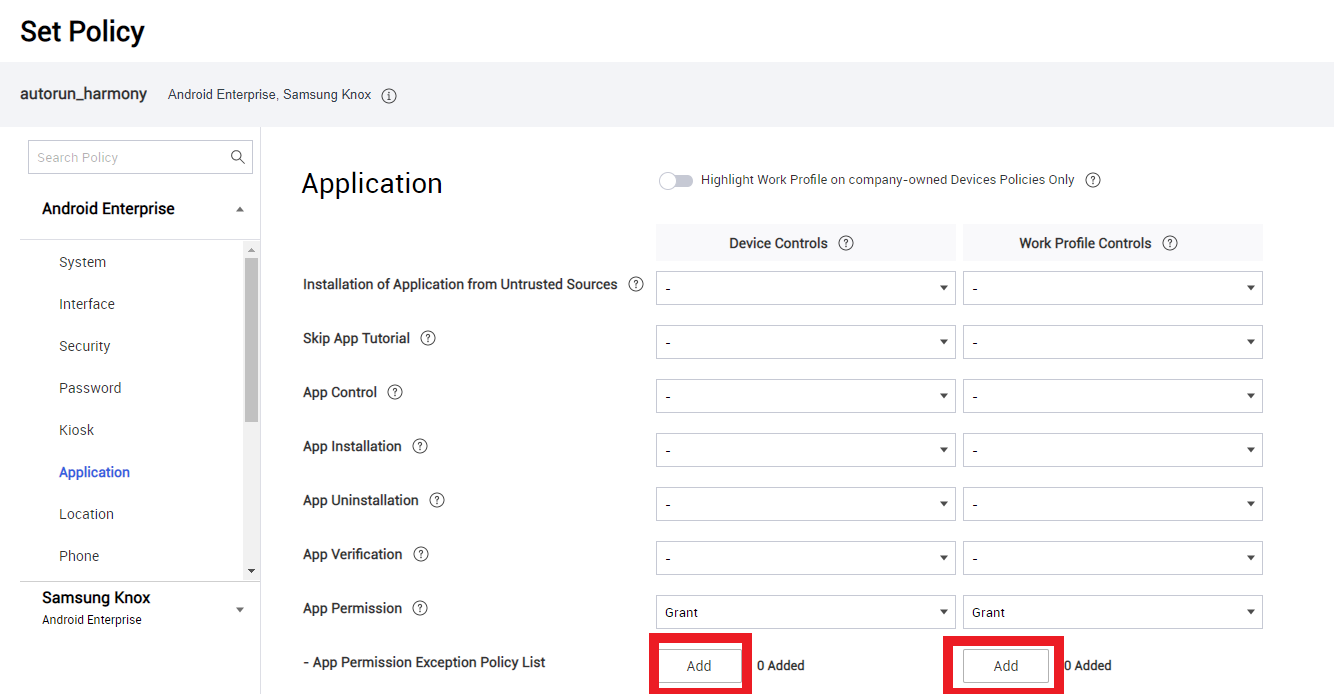
Click on both Add buttons for App Permission Exception Policy List.
-
Select Harmony Mobile Protect.
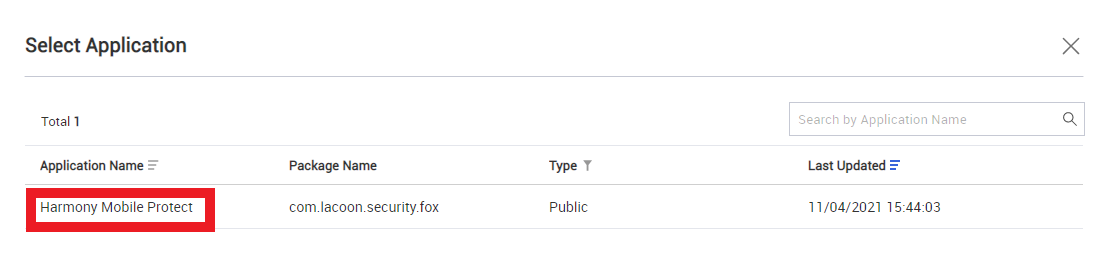
-
In Apply to all items below, select Grant and click Save.
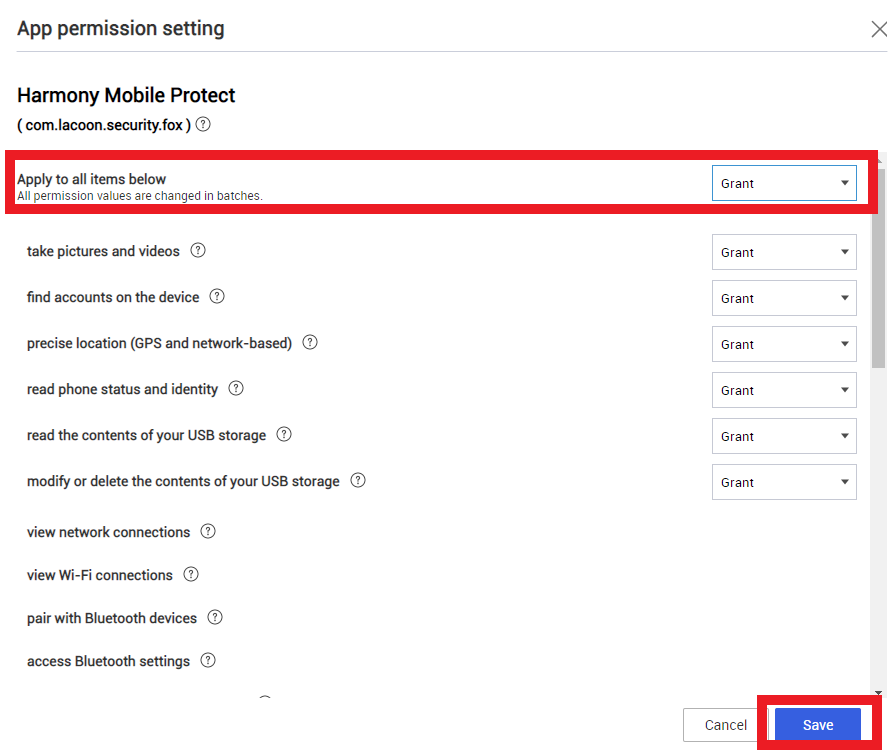
-
Navigate to Samsung Knox > Knox Service Plugin > Device Wide Policies.
For Enable device policy controls, select True .
Under Device Admin allowlisting, select True for Enable device admin controls, and click Add.
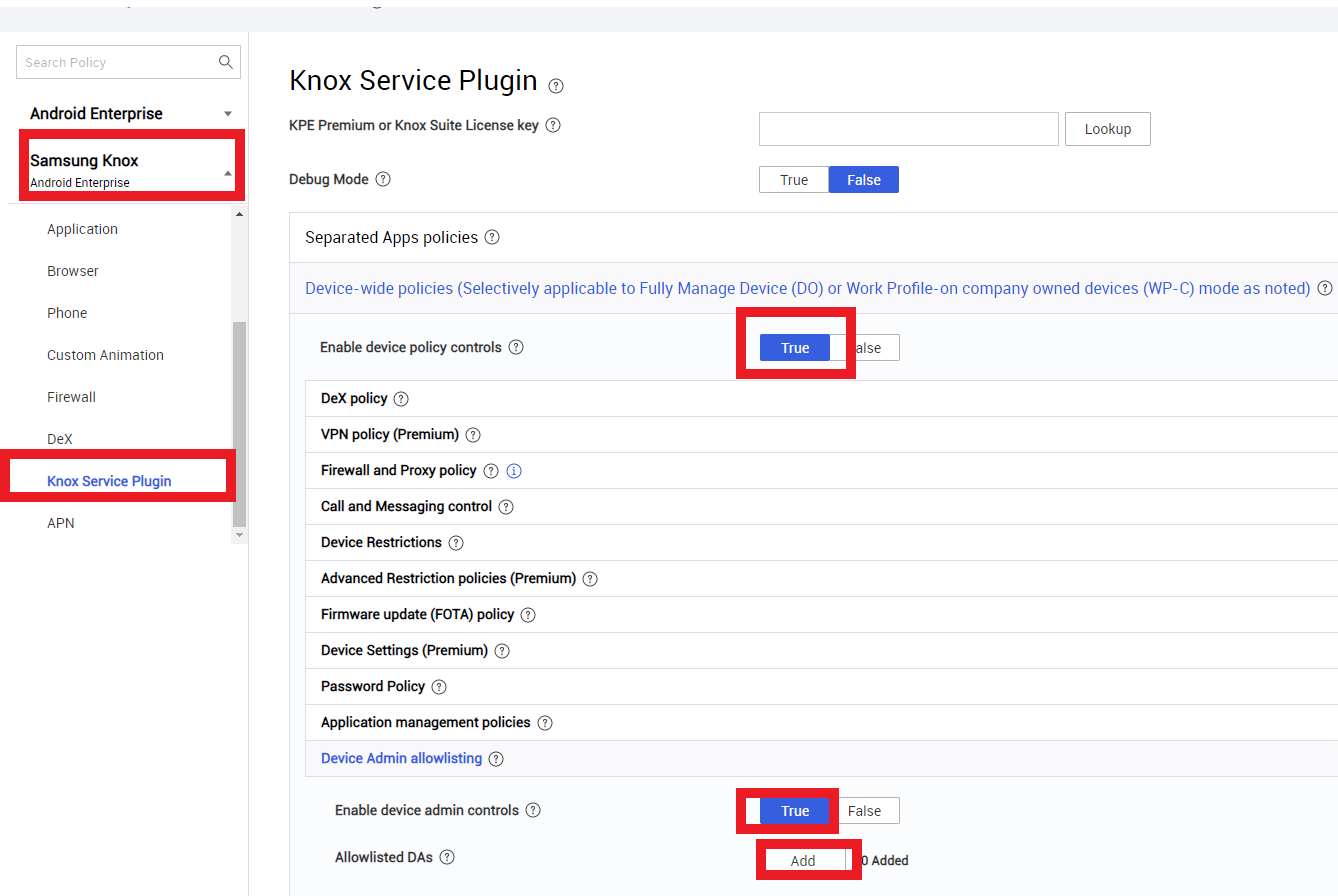
-
Select Harmony Mobile Protect and click OK.
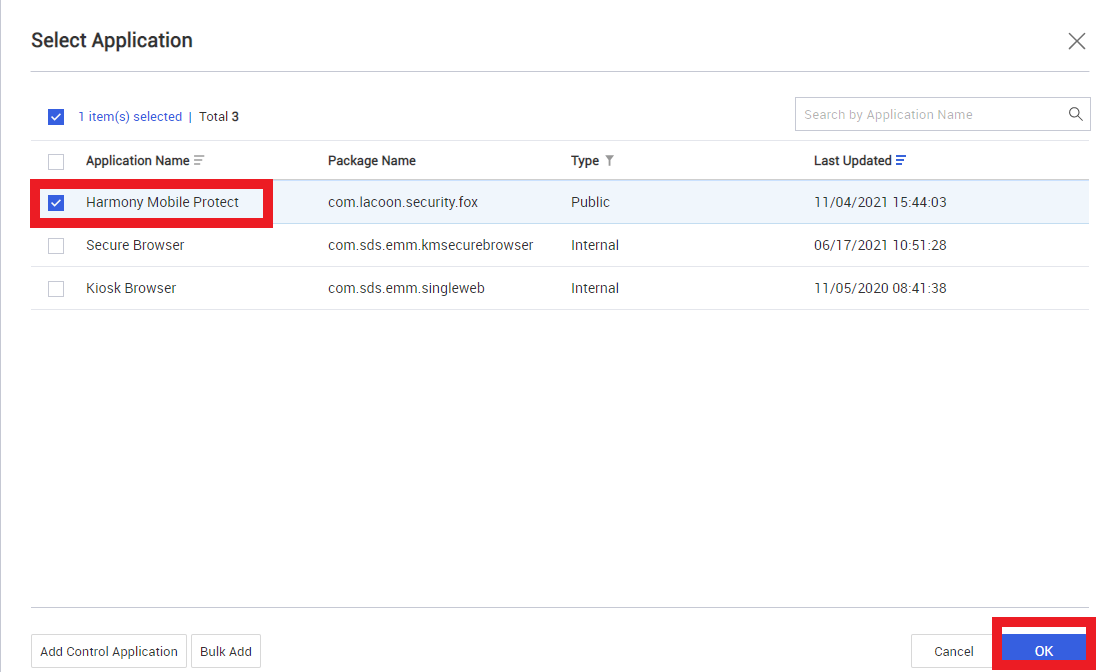
-
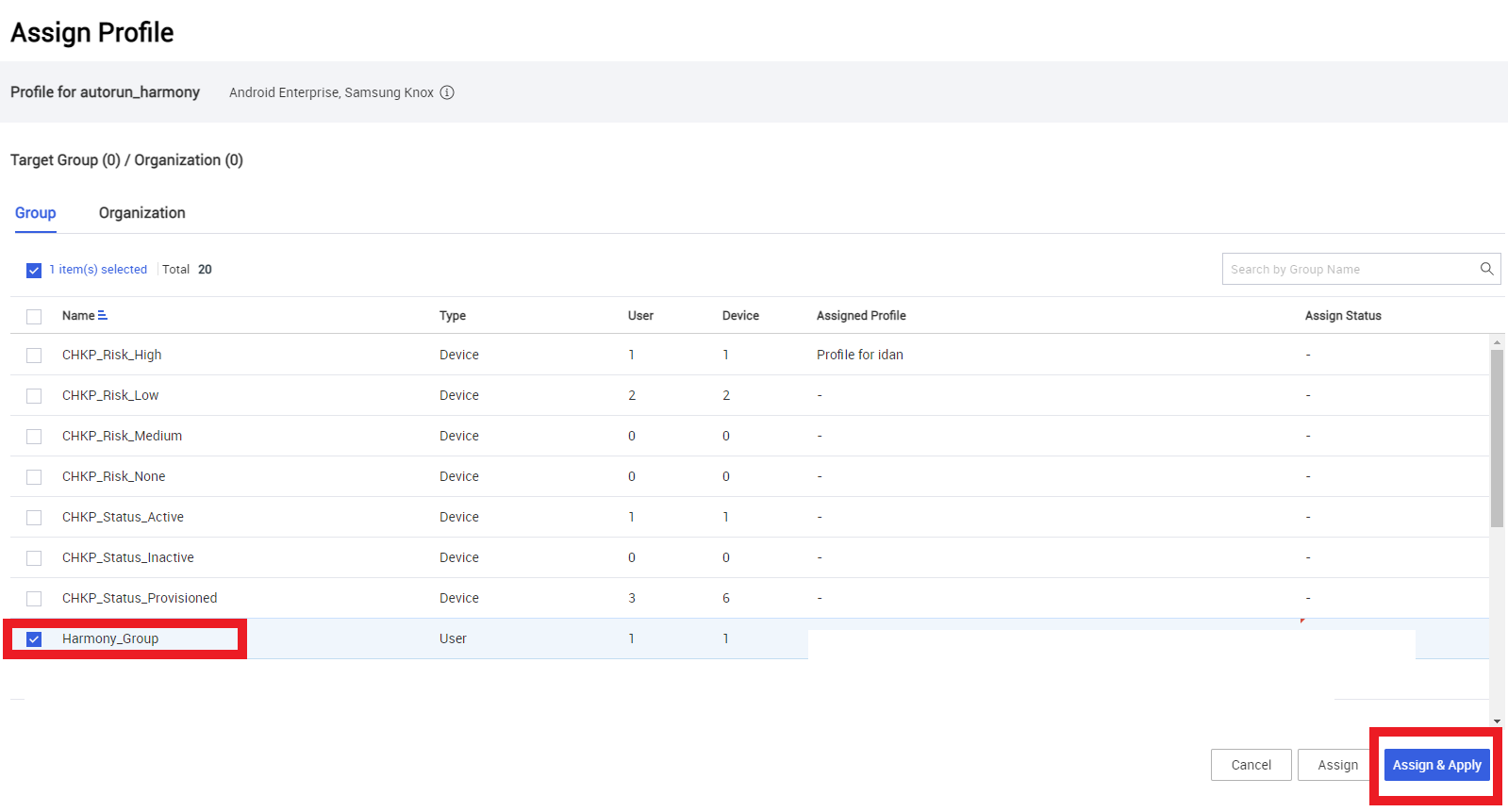
Click Save & Assign.
-
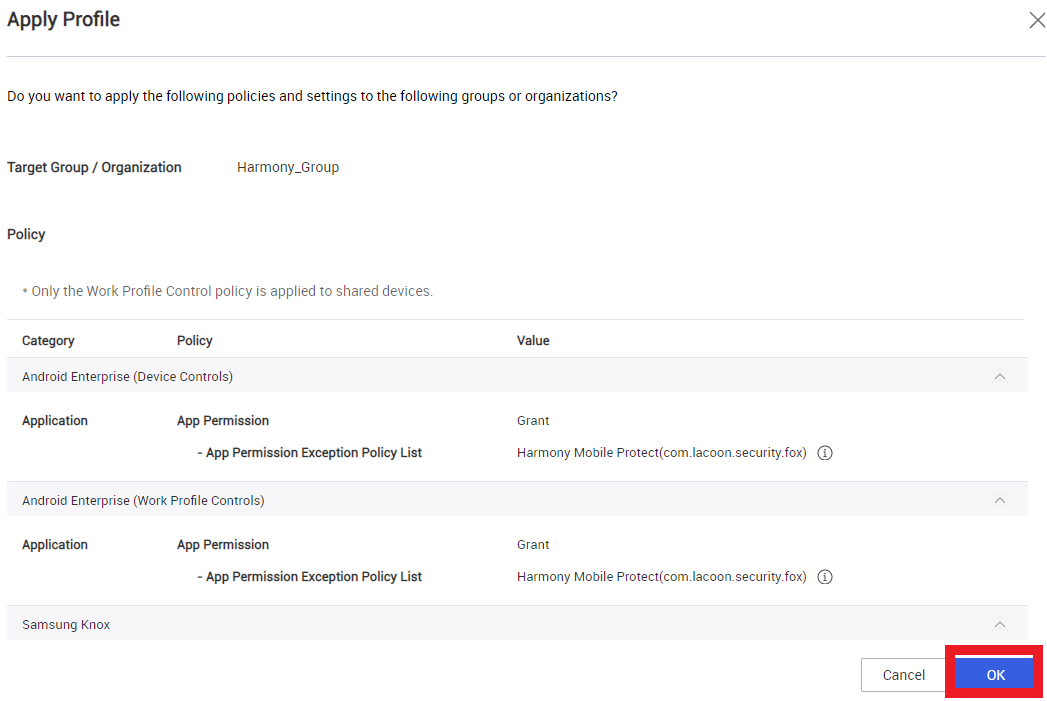
Select the group that integrated with Harmony, and click Assign & Apply.
-
Click OK.
CA certificate deployment using the UEM
This section is relevant if you use the On-device Network Protection (ONP) feature with the HTTPS Inspection option turned on.
First, you need to create a certificate in the Harmony Mobile dashboard and then set the configuration on the UEM to push it to the devices. This certificate is used for the ONP SSL![]() Secure Sockets Layer. The standard security technology for establishing an encrypted link between a web server and a browser. inspection.
Secure Sockets Layer. The standard security technology for establishing an encrypted link between a web server and a browser. inspection.
Creating the Certificate in the Harmony Mobile Dashboard
-
In the Harmony Mobile dashboard, go to Policy > Network Protection.
-
Under HTTPS Settings, select the HTTPS Inspection checkbox.
Under Inspection CA, select Central CA for UEM Deployment.
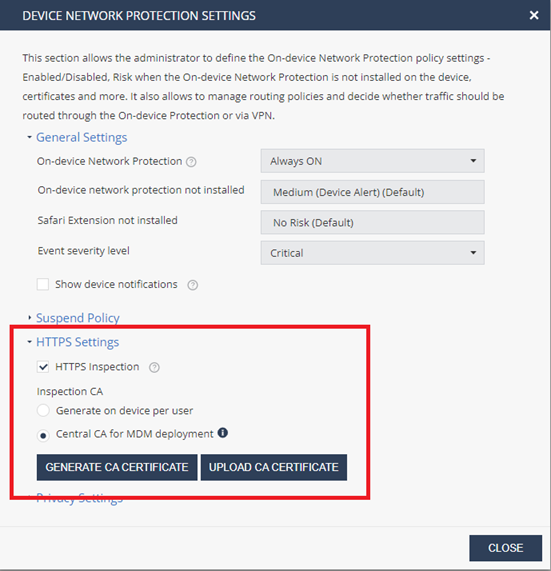
- Click Generate CA Certificate and download it to your computer.
Adding the External Certificate in Samsung Knox
You must add the CA certificate in Samsung Knox portal before you deploy it in the devices. To add an external certificate, see Adding external certificates in External certificates.
Creating a Certificate Profile in the UEM
-
Create a profile for Android Enterprise.
-
In the created profile, go to Policy > Certificate.
Add the CA certificate.
-
In Assigned Group/Organization, assign the profile to the required user groups.
-
Click Apply.
In the mobile device, the user receives a notification to install the certificate.
