Appendix
Integration Information
|
Information Name |
Description |
||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
MobileIron Core Server/API URL |
|
||||||||||||||
|
MobileIron Core API Admin Username |
|
||||||||||||||
|
MobileIron Core API Admin Password |
|
||||||||||||||
|
MobileIron Core Device Provisioning |
|
||||||||||||||
|
MobileIron Core Mitigation group (Device Group) (deprecated) |
|
||||||||||||||
|
Tag Device Risk (CHKP_Risk) |
None, Low, Medium, or High |
||||||||||||||
|
Tag Device Status (CHKP_Status) |
Provisioned, Active, or Inactive |
||||||||||||||
|
Tag Device Threat Factor (CHKP_TP) |
Free-form information provided by BRE |
||||||||||||||
|
Harmony Mobile Gateway |
Security gateway servers: Enter the Security Gateway
|
||||||||||||||
|
Harmony MobileApp Name (iOS) |
Harmony Mobile Protect |
||||||||||||||
|
Harmony Mobile App ID (iOS) |
com.checkpoint.capsuleprotect |
||||||||||||||
|
Harmony Mobile App Name (Android) |
Harmony Mobile Protect |
||||||||||||||
|
Harmony Mobile App ID (Android) |
com.lacoon.security.fox |
Deploying a CA certificate using Zero-Touch for HTTPS Traffic Inspection
Generate and download the certificate from you Infinity Portal dashboard:
-
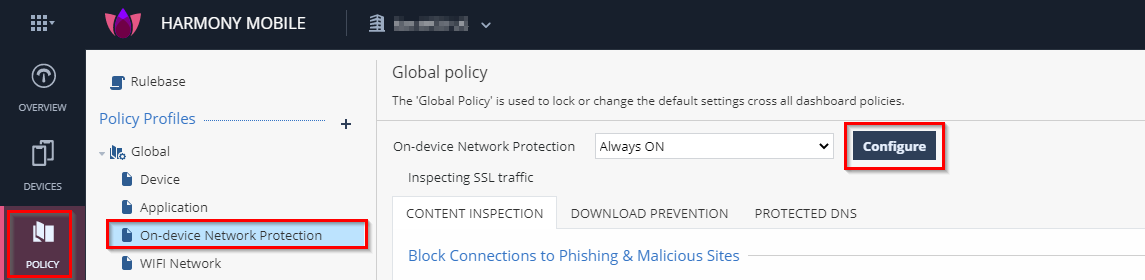
In your Infinity Portal dashboard, go to Policy > Global > On-device Network Protection > click on Configure:
-
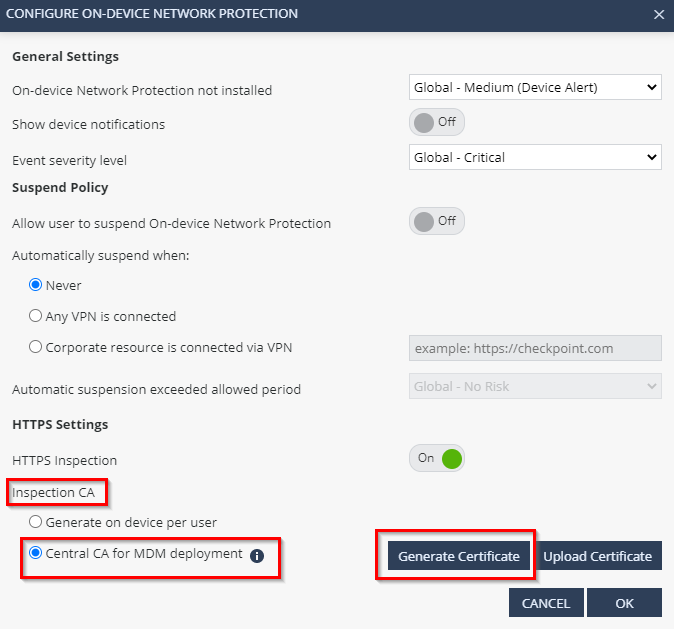
Under HTTPS Settings toggle HTTPS Inspection
 Feature on a Security Gateway that inspects traffic encrypted by the Secure Sockets Layer (SSL) protocol for malware or suspicious patterns. Synonym: SSL Inspection. Acronyms: HTTPSI, HTTPSi. to be ON, then under Inspection CA, select Central CA for UEM deployment and click on Generate Certificate:
Feature on a Security Gateway that inspects traffic encrypted by the Secure Sockets Layer (SSL) protocol for malware or suspicious patterns. Synonym: SSL Inspection. Acronyms: HTTPSI, HTTPSi. to be ON, then under Inspection CA, select Central CA for UEM deployment and click on Generate Certificate: -
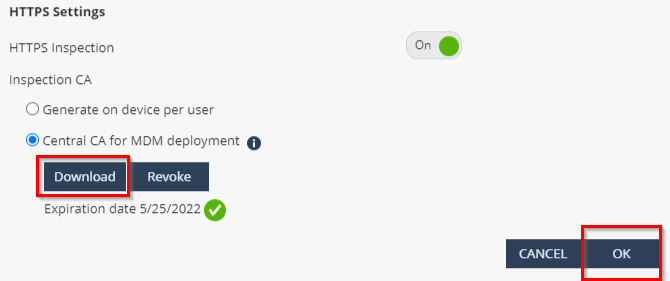
Validate the name, click on Download and on OK:
|
|
Note - When using different policies for device groups, the enforcement of the certificate pushed by UEM In case the Global Policy is being used for the entire fleet of devices this limitation is not relevant. |