Mobile Application Management (MAM) & Mobile Threat Defense (MTD) Integration
This section is relevant if you use Microsoft Intune Mobile Application Management (MAM) to manage the use of mobile applications in your organization. For more information, see Microsoft Intune App Management.
When you integrate MAM with Harmony Mobile:
-
For devices managed by Microsoft Intune UEM
 Unified Endpoint Management. An architecture and approach that controls different types of devices such as computers, smartphones and IoT devices from a centralized command point., it blocks access to Microsoft Office 365 applications if Harmony Mobile detects a device threat above a specific risk level.
Unified Endpoint Management. An architecture and approach that controls different types of devices such as computers, smartphones and IoT devices from a centralized command point., it blocks access to Microsoft Office 365 applications if Harmony Mobile detects a device threat above a specific risk level. 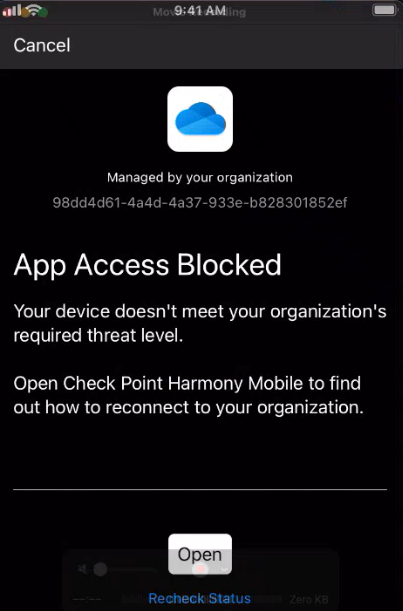
-
For Bring Your Own Device (BYOD), MAM blocks access to Microsoft Office 365 apps unless the Harmony Mobile Protect App is installed on the BYOD device. It automatically prompts the user to download and install the Harmony Mobile Protect App.
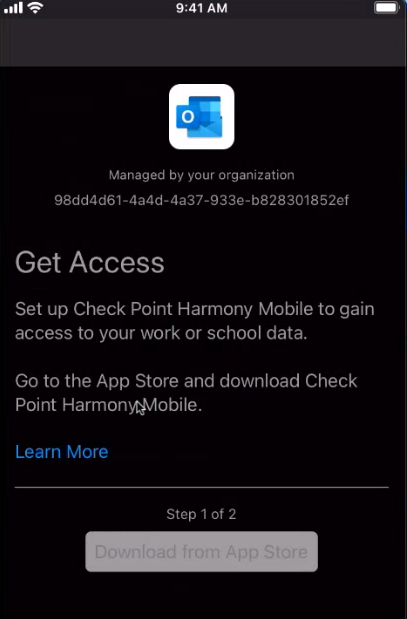
Applying the Mobile Application Management (MAM) Policy
|
|
Note - To manage the mobile applications, it is mandatory to enforce the MAM policy on the end-user device. |
-
Configure the MTD connector in Microsoft Intune. See Enabling the MTD Connector in Microsoft Intune Portal.
-
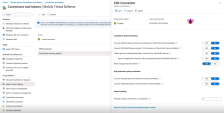
Go to Connectors and tokens > Mobile Threat Defense.
-
In the MTD Connector section, click Check Point Harmony Mobile.
-
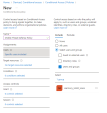
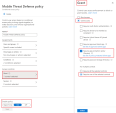
Set the Compliance policy evaluation and App protection policy evaluation sections for Android and iOS devices as shown in this screen.
-
On the Microsoft Intune Admin Center, go to Devices > Conditional Access > Policies.
-
Click Create new policy.
-
Enter Name as Mobile Threat Defense policy.
-
In the Users and groups section, search and assign the MTD policy to your group.
-
In Conditions:
-
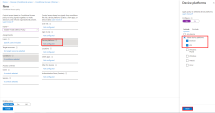
In Grant section, click controls selected and select Require app protection policy and the option for multiple controls as shown.
-
Turn on Enable policy and click Create.
-
-
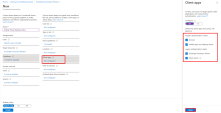
Go to Apps > App protection policies and create a new policy.
-
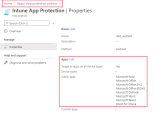
In the Apps section, select the apps that you want to enforce the MAM policy.
-
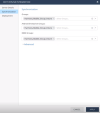
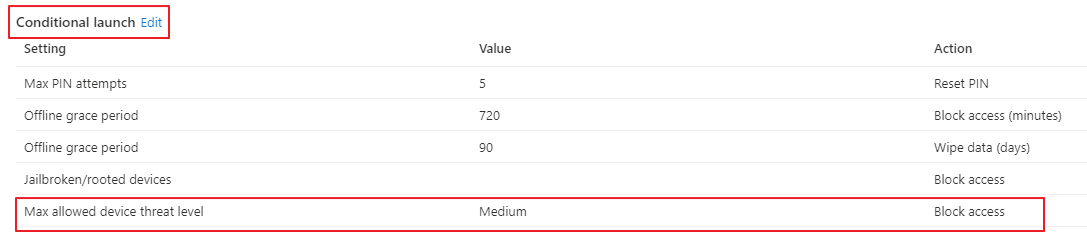
In the Conditional launch section, set the Max allowed mobile threat level.
The system blocks access to the selected apps if Harmony Mobile detects a device threat above the Max allowed mobile threat level.
-
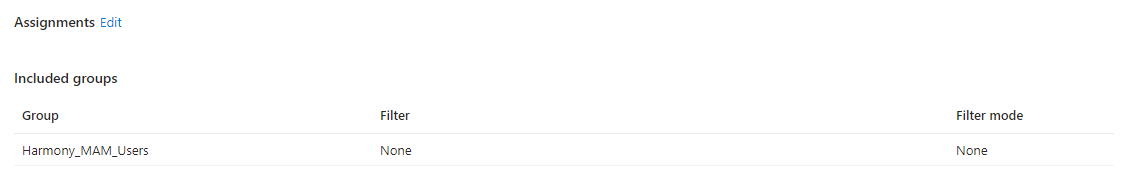
In the Assignments section, click Add Groups, select your security group and click Select.
-
Click Next.
-
Click Create.
MAM enforces the App protection policy on your device group.
-
Configuring the Harmony Mobile Administrator Portal
Prerequisite
Configure Microsoft Intune integration on Harmony Mobile Administrator Portal. See Configuring the Harmony Mobile Administrator Portal UEM Integration Settings.
To configure MAM integration:
-
In the Harmony Mobile Administrator Portal, go to Settings > Integrations > Microsoft Intune > Edit.
-
In the Synchronization section, add the MAM group in both Groups and MAM Groups.
The MAM policy is enforced on these device groups.

Best Practice - Use separate device groups for Microsoft Intune UEM managed devices and MAM devices.

Note - Make sure not to sync the MAM group to the Android Enterprise Groups section.