Introduction to Harmony Mobile
Check Point Harmony Mobile is the most complete threat defense solution designed to prevent emerging fifth generation cyber-attacks and allows workers to safely conduct business. Its technology protects against threats to the OS, applications, and network, scoring the industry’s highest threat catch rate without impacting performance or user experience.

Harmony Mobile delivers threat prevention technology that:
-
Performs advanced app analysis to detect known and unknown threats
-
Prevents man-in-the-middle attacks on both cellular and WiFi networks
-
Blocks phishing attacks on all apps: email, messaging, social media
-
Prevents infected devices from sending sensitive data to botnets
-
Blocks infected devices from accessing corporate applications and data
-
Mitigates threats without relying on user action or mobile management platforms
Harmony Mobile uses a variety of patent-pending algorithms and detection techniques to identify mobile device risks, and triggers appropriate defense responses that protect business and personal data.
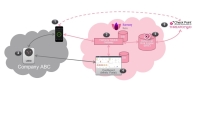
The Harmony Mobile solution ("the Solution") includes these components:
-
Harmony Mobile Behavioral Risk Engine ("the Engine")
-
Harmony Mobile Gateway ("the Gateway")
-
Harmony Mobile Management Dashboard ("the Dashboard")
-
Harmony Mobile Protect App ("the App") for iOS and Android
Solution Architecture
|
|
Component |
Description |
|---|---|---|
|
1 |
Harmony Mobile Protect App |
|
|
2 |
UEM |
For more information on how to integrate the Harmony Mobile solution with different UEMs, see Harmony Mobile UEM Integration Guide. |
|
3 |
Harmony Mobile Gateway |
|
|
4 |
Harmony Mobile Management Dashboard |
|
|
5 |
Behavioral Risk Engine |
|
|
6 |
ThreatCloud |
|
Supported Operating Systems (OS)
Harmony Mobile is supported on these mobile OS versions:
-
Android - Version 10.x or higher.
-
iOS/iPadOS - Version 13.x or higher.
|
|
Notes:
|
Supported Languages
Harmony Mobile Protect App supports the following languages:
-
Simplified Chinese
-
Traditional Chinese
-
Dutch
-
English
-
Finnish (Android only)
-
French
-
German
-
Italian
-
Japanese
-
Norwegian
-
Polish
-
Portuguese
-
Portuguese (Brazil)
-
Russian
-
Spanish
-
Turkish
|
|
Note - To select the language in the Harmony Mobile Administrator Portal user interface, go to the user Profile Settings.
|
API Reference
Harmony Mobile API allows you to view and configure users, devices, device groups, connect to UEMs, retrieve security events from third-parties and so on, using REST API calls.
To access Harmony Mobile API:
-
Go to https://sc1.checkpoint.com/documents/latest/api_reference/index.html#
-
Click Harmony.
-
In the Harmony Mobile API widget, click Open.
|
|
Note - To view and configure your tenants, users, services and licenses in the Infinity Portal, go to Infinity Portal API. |