Policy Operation
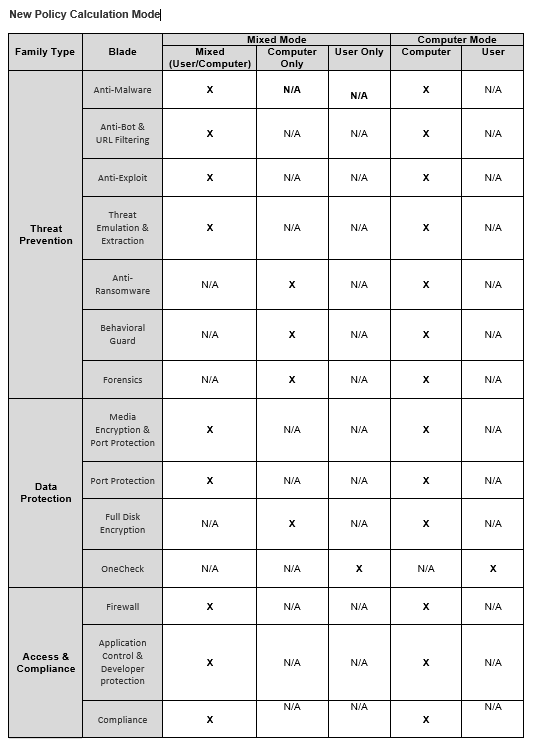
The new policy operation mode allows greater flexibility to the user by proving him with a choice of capability rule![]() Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. applicability. While under the old policy calculation the rule type of each capability determined whether the capability can work on user or computer, under the new policy the user has the ability to define for himself which method he wants the capability to work in (except in cases where it only makes sense for the capability to apply to users or computers, but not both).
Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. applicability. While under the old policy calculation the rule type of each capability determined whether the capability can work on user or computer, under the new policy the user has the ability to define for himself which method he wants the capability to work in (except in cases where it only makes sense for the capability to apply to users or computers, but not both).
In this new operation mode, most capabilities are "mixed", which means they can function per users or computers, according to the user’s choice. In each capability, the rules are ordered both by their assigned environment, from the specific down to the general, as well as by user/computer applicability: the first rule applies to the users, and if no match is found, the following rules apply to computers/devices as well.
To view the Policy Operations Mode page, click Endpoint Settings > Policy Operations Mode.
Old Policy Calculation Mode
.