Behavioral Protection
Behavioral protection includes Anti-Bot![]() Check Point Software Blade on a Security Gateway that blocks botnet behavior and communication to Command and Control (C&C) centers. Acronyms: AB, ABOT., Behavioral Guard and Anti-Ransomware protections.
Check Point Software Blade on a Security Gateway that blocks botnet behavior and communication to Command and Control (C&C) centers. Acronyms: AB, ABOT., Behavioral Guard and Anti-Ransomware protections.
The Anti-Bot Component
There are two emerging trends in today's threat landscape:
-
A profit-driven cybercrime industry that uses different tools to meet its goals. This industry includes cyber-criminals, malware operators, tool providers, coders, and affiliate programs. Their "products" can be easily ordered online from numerous sites (for example, do-it-yourself malware kits, spam sending, data theft, and denial of service attacks) and organizations are finding it difficult to fight off these attacks.
-
Ideological and state driven attacks that target people or organizations to promote a political cause or carry out a cyber-warfare campaign.
Both trends are driven by bot attacks.
A bot is malicious software that can invade your computer. There are many infection methods. These include opening attachments that exploit a vulnerability and accessing a website that results in a malicious download.
When a bot infects a computer, it:
-
Takes control over the computer and neutralizes its Anti-Virus
 Check Point Software Blade on a Security Gateway that uses real-time virus signatures and anomaly-based protections from ThreatCloud to detect and block malware at the Security Gateway before users are affected. Acronym: AV. defenses. Bots are difficult to detect because they hide within your computer and change the way they appear to the Anti-Virus software.
Check Point Software Blade on a Security Gateway that uses real-time virus signatures and anomaly-based protections from ThreatCloud to detect and block malware at the Security Gateway before users are affected. Acronym: AV. defenses. Bots are difficult to detect because they hide within your computer and change the way they appear to the Anti-Virus software.
-
Connects to a Command and Control (C&C) center for instructions from cyber criminals. The cyber criminals, or bot herders, can remotely control it and instruct it to execute illegal activities without your knowledge. These activities include:
-
Data theft (personal, financial, intellectual property, organizational)
-
Sending SPAM
-
Attacking resources (Denial of Service Attacks)
-
Bandwidth consumption that affects productivity
-
In many cases, a single bot can create multiple threats. Bots are often used as tools in attacks known as Advanced Persistent Threats (APTs) where cyber criminals pinpoint individuals or organizations for attack. A botnet is a collection of compromised computers.
The Check Point Endpoint Anti-Bot component detects and prevents these bot threats
The Anti-Bot component:
- Uses the ThreatCloud repository to receive updates, and queries the repository for classification of unidentified IP, URL, and DNS resources.
- Prevents damage by blocking bot communication to C&C sites and makes sure that no sensitive information is stolen or sent out of the organization.
The Endpoint Anti-Bot component uses these procedures to identify bot infected computers:
-
Identify the C&C addresses used by criminals to control bots
-
These web sites are constantly changing and new sites are added on an hourly basis. Bots can attempt to connect to thousands of potentially dangerous sites. It is a challenge to know which sites are legitimate and which are not.
The ThreatCloud repository contains more than 250 million addresses that were analyzed for bot discovery and more than 2,000 different botnet communication patterns. The ThreatSpect engine uses this information to classify bots and viruses.
Configuring Anti-Bot
There are three configuration options for the Anti-Bot protection:
-
Prevent - Blocks bots.
-
Detect - Logs information about bots, but does not block them.
-
Off - Ignores bots (does not prevent or detect them)
Advanced Anti-Bot Settings:
-
Background Protection Mode:
-
Background - This is the default mode. Connections are allowed while the bots are checked in the background.
-
Hold - Connections are blocked until the bot check is complete.
-
-
Hours to suppress logs for same bot protection - To minimize the size of the Anti-Bot logs, actions for the same bot are only logged one time per hour. The default value is 1 hour. To change the default log interval , select a number of hours.
-
Days to remove bot reporting after - If a bot does not connect to its command and control server after the selected number of days, the client stops reporting that it is infected. The default value is 3 days.
-
Confidence Level - The confidence level is how sure Endpoint Security is that an activity is malicious. High confidence means that it is almost certain that the activity is malicious. Medium confidence means that it is very likely that the activity is malicious. You can manually change the settings for each confidence level. Select the action for High confidence, medium confidence and low confidence bots:
-
Prevent - Blocks bots
-
Detect - Logs information about bots, but does not block them.
-
Off - Ignores bots (does not prevent or detect them).
-
-
DNS Inspection Mode - DNS Inspection Mode is a security feature that monitors and inspects all websites your device attempts to access, ensuring protection against malicious or harmful sites. This feature is turned on by default, even before any Security Policies
 Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. are applied to the device. Once you manually configure DNS Inspection Mode (turning it on or off), your settings will override the default settings from the management server. This ensures your device is protected immediately, allowing you to customize the settings later.
Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. are applied to the device. Once you manually configure DNS Inspection Mode (turning it on or off), your settings will override the default settings from the management server. This ensures your device is protected immediately, allowing you to customize the settings later.
The Behavioral Guard & Anti-Ransomware Component
Behavioral Guard constantly monitors files and network activity for suspicious behavior.
|
|
Note - Behavioral Guard also parses the email (through an add-in to Microsoft Outlook) to include the details in the forensics report in the event of a malicious attack through an email. |
The Anti-Ransomware creates honeypot files on client computers, and stops the attack immediately after it detects that the ransomware modified the files.
Starting from version E88.50 and later, the Anti-Ransomware creates the honeypot files in these folders:
-
Drive root (C:\ , D:\ , Etc) -
C:\Users\Public\Music -
C:\Users\<User>\Music (MyMusic) -
C:\Users\Public\Documents -
C:\Users\<User>\Documents (MyDocuments) -
C:\Users\Public\Videos -
C:\Users\<User>\Videos (MyVideos) -
C:\Users\Public\Pictures -
C:\Users\<User>\Pictures (MyPictures) -
C:\Program Files (x86) -
C:\ProgramData -
C:\Users\<User>\AppData\Roaming -
C:\Users\<User>\AppData\Local
For versions prior to E88.50, the Anti-Ransomware creates the honeypot files in these folders:
-
C:\Users\Public\Music -
C:\Users\<User>\Music (MyMusic) -
C:\Users\Public\Documents -
C:\Users\<User>\Documents (MyDocuments) -
C:\Users\Public\Videos -
C:\Users\<User>\Videos (MyVideos) -
C:\Users\Public\Pictures -
C:\Users\<User>\Pictures (MyPictures) -
C:\Program Files (x86) -
C:\ProgramData -
C:\Users\<User>\AppData\Roaming -
C:\Users\<User>\AppData\Local
Starting with version E88.41 and later, folders with restricted access are identified by a lock icon next to the folder name.
For example:

For versions prior to E88.41, folders with restricted access are identified by a lock icon next to the folder name.
For example:
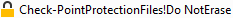
The file names include these strings, or similar:
-
CP
-
CheckPoint
-
Check Point
-
Check-Point
-
Sandblast Agent
-
Sandblast Zero-Day
-
Endpoint
Before ransomware attack can encrypt files, Anti-Ransomware backs up your files to a safe location. After the attack is stopped, it deletes files involved in the attack and restores the original files from the backup location.
-
Prevent - The attack is remediated. Logs, alerts and a forensic report are created.
-
Detect - Logs, alerts and a forensic report are created.
-
Off - Nothing is done on the detection, a log is not created
Advanced Behavioral Guard & Anti-Ransomware Settings
-
Enable network share protection - Enables the protection of shared folders on the network. All shared folders are protected, regardless of the protocol. Remote devices are not protected.
-
Block Volume Encryption tools (BitLocker and Similar Tools): As many ransomwares use volume encryption software, such as BitLocker to encrypt drives.

Note - This feature is supported with the Harmony Endpoint Security Client
 Application installed on end-user computers to monitor security status and enforce security policies. version E86.30 with the default client mode as Detect. With the Harmony Endpoint Security Client version E86.50 and higher, the default client mode is Prevent.
Application installed on end-user computers to monitor security status and enforce security policies. version E86.30 with the default client mode as Detect. With the Harmony Endpoint Security Client version E86.50 and higher, the default client mode is Prevent.You can block such programs from:
-
Encrypting unencrypted drives
-
Modifying the encryption of encrypted drives (such as changing password)
If you want to encrypt your drive with BitLocker or a similar software:
-
Encrypt the drive before you install the Harmony Endpoint Security Client, or
-
Disable this protection, encrypt and resume this protection
-
-
Allow extensive data collection: Allow Harmony Endpoint to collect extended information from endpoints.

Note - This may increase the resources used.
-
Low memory mode:
This setting reduces memory usage by loading a carefully selected subset of threat signatures, optimized for protection effectiveness and minimal memory footprint. While this can help improve performance on devices with limited memory, it may slightly reduce detection coverage in some scenarios.
Check Point recommends to enable this mode only on systems with low memory capacity, where resource constraints justify the trade-off.

Note - The Low memory mode setting is supported starting with Endpoint Security Client version E87.30 and above.
Backup Settings
When Anti-Ransomware is enabled, it constantly monitors files and processes for unusual activity. Before a ransomware attack can encrypt files,Anti-Ransomware backs up your files to a safe location. After the attack is stopped, it deletes files involved in the attack and restores the original files from the backup location.
-
Restore to selected location - - By default, files are restored to their original location. To restore files to a different location, select this option and enter the location to which you want to restore the files in the Choose location field. Each time files are automatically restored, they will be put in the selected location.
-
Anti-Ransomware maximum backup size on disk - Set the maximum amount of storage for Anti-Ransomware backups. The default value is 1 GB.
-
Backup time interval - Within this time interval, each file is only backed up one time, even if it is changed multiple times. The default value is 60 minutes.
-
Backup Settings - Change default types to be backed up - Click this to see a list of file types that are included in the Anti-Ransomware backup files. You can add or remove file types from the list and change the Maximum Size of files that are backed up.

Notes:
-
By default, the maximum file size for back up is 25 MB. To change the maximum file size, edit the Maximum Size (MB).
-
For information on HarmonyBackup (AKA SandBlastBackup) folder, see sk147454.
-
-
Disk Usage - By default, Forensics uses up to 1 GB of disk space on the client computer for data.
The Anti-Exploit Component
Harmony Endpoint Anti-Exploit detects zero-day and unknown attacks, and provides protection to vulnerable processes from exploitation. Files on your computer are sent to a testing area for emulation to detect malicious files and content.
There are three configuration options for the Anti-Exploit protection:
-
Prevent - Prevents the attack and suspends the application under attack.
-
Detect - Detects and logs the attack information. Does not prevent the attack.
-
Off - The Anti-Exploit protection is disabled.
