Performing Push Operations (Old User Interface)
|
|
Note - To make the user interface clear and helpful, there is a new interface available. See Push Operations. |
Push operations are operations that the server pushes directly to client computers with no policy installation required.
|
|
Note - If there is no response from the Endpoint Security client, the Push Operation will time out after 24 hours. You must reinitiate the Push Operation. |
To add a Push Operation:
-
Go to the Push Operation view and click Add.
-
Select the push operation and click Next.
Category
Push Operations
Windows
macOS
Linux
Scan for Malware
Yes
Yes
Yes
Update Malware Signature Database
Yes
Yes
Yes
Restore Files from Quarantine
Yes
Yes
Yes
Forensics and Remediation
Analyze by Indicator
Yes
Yes
No
File Remediation
Yes
Yes
Yes
Isolate Computer
Yes
Yes
No
Release Computer
Yes
Yes
No
Agent Settings
Deploy New Endpoints
Yes
No
No
Collect Client Logs
Yes
Yes
No
Repair Client
Yes
No
No
Shutdown Computer
Yes
Yes
No
Restart Computer
Yes
Yes
No
Uninstall Client
Yes
Yes
No
Application Scan
Yes
Yes
No
Kill Process
Yes
Yes
No
Remote Command
Yes
Yes
Yes
Search and Fetch files
Yes
Yes
No
Registry Actions
Yes
No
No
File Actions
Yes
Yes
No
VPN Site
Yes
Yes
No
Collect Processes
Yes
No
No
Run Diagnostics
Yes
Yes
No
Enable / Disable Self Protection
Yes
Yes
No
-
Select the devices on which you want to perform the push operation.

Note - You can perform Run Diagnostics on only one device at a time.
-
Click Next.
-
Configure the operation settings.
-
In the Full Path field, enter the path to file before it was quarantined including the file name. For example,
c:\temp\eicar.txt -
Click OK.
-
Click
and select the organization.
-
Click Update Selection.
-
Select the device and click Next.
-
Add Comment, optional comment about the action.
-
To move the files to quarantine, select Move the following files to quarantine.
-
To restore the files from quarantine, select Restore the following files from quarantine.
-
Click
.
-
From the drop-down:
-
Select Full file path or Incident ID:
-
In the Element field, enter the incident ID from the Harmony Endpoint Security client or enter the incident UID for the corresponding incident from the Logs menu in the Harmony Endpoint portal. To obtain the incident UID, open the log entry and expand the More section to view the incident UID.
-
Click OK
-
-
Select MD5 Hash:
-
Enter or upload the Element.
-
Click OK.
-
-
-
Click Finish.
-
For Windows:
-
For Endpoint Security Client
 Application installed on end-user computers to monitor security status and enforce security policies. versions E88.31 and higher, client logs are stored in the directory C:\ProgramData\CheckPoint\Endpoint Security\Temp.
Application installed on end-user computers to monitor security status and enforce security policies. versions E88.31 and higher, client logs are stored in the directory C:\ProgramData\CheckPoint\Endpoint Security\Temp. -
For Endpoint Security Client versions E88.30 and lower, client logs are stored in the directory C:\Windows\SysWOW64\config\systemprofile\CPInfo.
-
-
For macOS, client logs are stored in the directory /Users/Shared/cplogs.
-
Upload CPInfo reports to AWS S3 - If the push operation is successful, the administrator will receive a download link in the Harmony Endpoint EPMaaS Administrator portal to download the logs.

Notes -
-
This option is supported only with the Harmony Endpoint Security client for Windows version E88.30 and higher and for macOS version E88.50 and higher.
-
To enable this option, select a single user.
-
You can create and copy the link to download the logs using the copy to clipboard icon in the Operation output section of the Push Operation Endpoint Details. The copied link will be valid for 30 minutes.
-
-
Upload CPInfo reports to Check Point servers
-
Upload CPInfo reports to Corporate server - Update the relevant corporate server information.
-
Allows administrators to run both signed (introduced by CP) and unsigned (ones the customer creates) scripts on the Endpoint Client devices.
-
Especially useful in a non-AD environment.
-
Supplies tools/fixes to customers without the need to create new EP client/server versions.
-
Saves passwords securely when provided.
-
In the File table, click
.
-
Enter the file name. For example, test.txt or test.zip and click OK.
-
Repeat the steps 1 and 2 for additional files.
-
In the Folder Path table, click
-
Enter the path and click OK.
-
Repeat the steps 4 and 5 for additional paths.
-
In the File table, click
.
-
Enter the path where you want to search for the file and click OK.
-
Repeat the steps for additional paths.
-
Specify these:
-
Protocol
-
Server address
-
Path on server
-
Server fingerprint
-
-
If the server requires login to access it, select the Use specific credentials to upload checkbox, and enter Login and Password.
-
Add Key to Registry
-
Remove Key From Registry
 Caution - Removing a registry might impact the endpoint's operating system.
Caution - Removing a registry might impact the endpoint's operating system. -
Copy File
-
Move File
-
Delete File
 Caution - Deleting a file might impact Harmony Endpoint's protected files.
Caution - Deleting a file might impact Harmony Endpoint's protected files. -
For File - C:\Users\<user_name>\Desktop\test.doc
-
For Folder - C:\Users\Username\Desktop\
-
For File - C:\Users\<user_name>\Documents
-
For Folder - C:\Users\Username2\
-
The file or folder name you specify is used to rename the copied file.
-
If you provide the folder path only, the file is copied with the original file name.
-
If the file or folder already exists, the file is not overwritten and the operation fails.
-
If the file path or target folder does not exist, it is created during the operation.
-
For File - C:\Users\<user_name>\Desktop\test.doc
-
For Folder - C:\Users\Username>\Desktop\
-
For File - C:\Users\<user_name>\Documents
-
For Folder - C:\Users\Username1\Documents\
-
If you provide the full file path, the is moved with the specified name.
-
If you provide the folder path only, the file is moved with the original file name.
-
If the file or folder already exists, the file or folder is not overwritten and the operation fails.
-
If the file path or target folder does not exist, it is created during the operation.
-
This is not supported with Linux operating system.
-
You cannot create separate VPN sites for each user that access the endpoint. The same VPN site applies to all users.
-
SoftID and challenge-response authentication methods are not tested.
-
The system does not validate the entries (for example, Server Name or Fingerprint) that you specify.
-
Only one fingerprint operation is supported at a time.
-
You cannot add a new VPN site or remove a VPN site if a VPN site is already connected in the Harmony Endpoint client. Disconnect the VPN site before you add a new VPN site.
-
This operation is not supported if the firewall policy for the client is configured through the on-premise Security Gateway
 Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. (Policy > Data Protection > Access & Compliance > Firewall > When using Remote Access, enforce Firewall Policy from is Remote Access Desktop Security Policy). To enable the operation on such a client:
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. (Policy > Data Protection > Access & Compliance > Firewall > When using Remote Access, enforce Firewall Policy from is Remote Access Desktop Security Policy). To enable the operation on such a client:-
In the Security Gateway, change the parameter allow_disable_firewall to true in the $FWDIR/conf/trac_client_1.ttm file.
-
Install the policy on the Security Gateway.
-
Reboot the Harmony Endpoint client.
-
Perform the push operation.
-
-
Add VPN Site
-
Remove VPN Site
-
username-password
-
certificate (for a certificate stored in the CAPI store)
-
p12-certificate
-
securityIDKeyFob
-
securityIDPinPad
-
SoftID (not tested)
-
challenge-response (not tested)
-
Select certificate from hardware or software token (CAPI)
-
Use certificate from Public-Key Cryptographic Standard (PKCS #12) file
-
Other
-
Total CPU and RAM usage in the last 12 hours.
-
CPU usage by processes initiated in the last 12 hours. For example, the CPU used by Anti-Malware to scan files.
You can review the CPU usage data to identify processes (scans) that consume CPU more than the specified threshold and exclude such processes from future scans.

Note - This is supported with Endpoint Security client version E86.80 and higher.

Warning - Only exclude a process if you are sure that the file is not malicious and is not vulnerable to cyber-attacks.
To view the latest diagnostics report, see Show Last Diagnostics Report.
-
Enable - Enables the self protection capabilities.
-
Disable - Disables the self protection capabilities.
-
Timeout Command Expiration - Select the expiration time for the command.

Note - After the timeout, the command expires, and the self protection capabilities will be enabled automatically.
-
Process - Captures memory dumps for one or more processes using process name or PID.

Notes:
-
The system generates multiple memory dumps if several processes share the same name.
-
Memory dumps are not supported for Protected Process Light (PPL) processes.
-
-
Kernel - Collects a kernel memory dump without requiring a system reboot.

Note - Kernel memory dump is not supported on Windows 7 devices.
-
Full - Initiates a BSOD to collect a full or active memory dump (requires prior configuration on the target device). For more information, see Dell documentation.

Note - It is optional to reboot the endpoint to collect the Full memory dump.
-
Upload Memory Dump to AWS S3 - After the push operation is successful, the system shows a download option in the Operation output column of the Push Operation Endpoint Details section.
-
Upload Memory Dump to Check Point servers - After the push operation is successful, the system uploads the memory dump to this location:
-
For Windows Endpoint Security Client versions E88.31 and higher, client logs are stored in the directory C:\ProgramData\CheckPoint\EndpointSecurity\Temp.
-
For Windows Endpoint Security Client versions E88.30 and lower, client logs are stored in the directory C:\Windows\SysWOW64\config\systemprofile\CPInfo.
-
For macOS, client logs are stored in the directory /Users/Shared/cplogs.
-
-
Upload Memory Dump to Corporate server - Enter your corporate server details. After the push operation is successful, the system uploads the memory dump to the configured location in the corporate server.
-
Automated packaging and upload of memory dump - All memory dumps are automatically zipped, segmented if necessary, and uploaded to the designated destination (Check Point FTP, Amazon S3, or custom FTP servers).
-
On 32-bit Windows systems, the ZIP file name is not displayed when uploading full memory dumps to an FTP server.
-
The Memory Dump feature is supported only on Harmony Endpoint for Windows client version E89.05 and later.
-
Under User Notification:
-
To notify the user about the push operation, select the Inform user with notification checkbox.
-
To allow the user to post pone the push operation, select the Allow user to postpone operation checkbox.
-
-
Under Scheduling:
-
To execute the push operation immediately, click Execute operation immediately.
-
To schedule the push operation, click Schedule operation for and click to select the date.
-
-
Specify the duration after which the system automatically terminates the unexecuted push operation (For example, if the Endpoint client is offline):
-
7 days
-
Custom
-
Never
-
-
For Push Operations that support 2FA authentication, you are prompted to enter the verification code.
If you have not enabled 2FA authentication, a prompt appears to enable 2FA authentication:
-
To enable 2FA authentication for your profile, click Profile Setting, and follow the instructions. For more information, see Infinity Portal Administration Guide.
-
To enable 2FA authentication for the current tenant, click Global Settings, and follow the instructions. For more information, see Infinity Portal Administration Guide.
-
-
Click Finish.
-
View the results of the operations on each endpoint in the Endpoint List section (in the Push Operations menu) at the bottom part of the screen.
|
Push Operations |
Description |
2FA Required |
|---|---|---|
|
Scan for Malware |
Runs an Anti-Malware scan on the computer or computers, based on the configured settings. |
No |
|
Update Malware Signature Database |
Updates malware signatures on the computer or computers, based on the configured settings. |
No |
|
Restore Files from Quarantine |
Restores files from quarantine on the computer or computers, based on the configured settings. To restore files from quarantine: |
No |
|
Push Operations |
Description |
2FA Required |
|---|---|---|
|
Analyze by Indicator |
Manually triggers collection of forensics data for an endpoint device that accesses or executes the indicator. The indicator can be a URL, an IP, a path, a file name or an MD5. |
No |
|
File Remediation |
Quarantines malicious files and remediates them as necessary. To move or restore files from quarantine: |
No |
|
Isolate Computer |
Makes it possible to isolate a specific device that is under malware attack and poses a risk of propagation. This action can be applied on one or more devices. The Firewall component must be installed on the client in order to perform isolation. Only DHCP, DNS and traffic to the management server are allowed. |
No |
|
Release Computer |
Removes device from isolation. This action can be applied on one or more devices. |
No |
|
Push Operations |
Description |
2FA Required |
||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
Deploy New Endpoints |
Installs the Initial Client on the target devices remotely using any device as the medium to run the push operation. This is suitable if do not have third party tools such as Microsoft System Center Configuration Manager (SCCM) or Intune to install the client.
|
No | ||||||||||||||||||||||||||||
|
Collect Client Logs |
Collects CPInfo logs from an endpoint based on the configured settings.
|
No | ||||||||||||||||||||||||||||
|
Repair Client |
Repairs the Endpoint Security client installation. This requires a computer restart.
|
No | ||||||||||||||||||||||||||||
|
Shutdown Computer |
Shuts down the computer or computers based on the configured settings. |
No | ||||||||||||||||||||||||||||
|
Restart Computer |
Restarts the computer or computers based on the configured settings. |
No | ||||||||||||||||||||||||||||
|
Uninstall Client |
Uninstalls the Endpoint Security client remotely on the selected devices. This feature is supported for E84.30 client and above. |
Yes | ||||||||||||||||||||||||||||
|
Application Scan |
Collects all available applications in a certain folder on a set of devices and then adds them to the application repository of the "Application Control |
No | ||||||||||||||||||||||||||||
|
Kill Process |
Remotely kills/ terminate the processes. |
No | ||||||||||||||||||||||||||||
|
Remote Command |
|
Yes | ||||||||||||||||||||||||||||
|
Search and Fetch files |
Searches and uploads files to a server.
Supported fields are:
|
Yes |
||||||||||||||||||||||||||||
|
Registry Actions |
Add or remove a registry key.
Supported fields:
|
No |
||||||||||||||||||||||||||||
|
File Actions |
Copy, move or delete the file or folder. Supported fields:
|
No |
||||||||||||||||||||||||||||
|
VPN Site |
Adds or removes a VPN site.
Limitations: Note - If the operation fails with timeout, see sk179798 for troubleshooting instructions.
Supported fields:
|
No |
||||||||||||||||||||||||||||
|
Collect Processes |
Collects information about the process running on the endpoint.
Supported fields:
|
No |
||||||||||||||||||||||||||||
|
Run Diagnostics |
Runs diagnostics on an endpoint to collect this information: |
|
||||||||||||||||||||||||||||
|
Enable / Disable Self Protection |
This push operation allows the administrator to enable or disable the self protection capabilities on endpoints.
Supported fields: |
|
||||||||||||||||||||||||||||
|
Collect Memory Dump |
Collects Memory Dump from an endpoint based on the configured settings. Memory dump is a snapshot of system memory at specific instance of the active process and the operating system.
|
|
||||||||||||||||||||||||||||
Collecting Fingerprint details for a VPN Site:
-
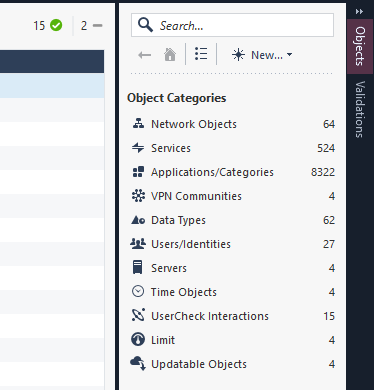
In SmartConsole, in the right pane, under Object Categories, click Servers > Trusted CA > internal ca.
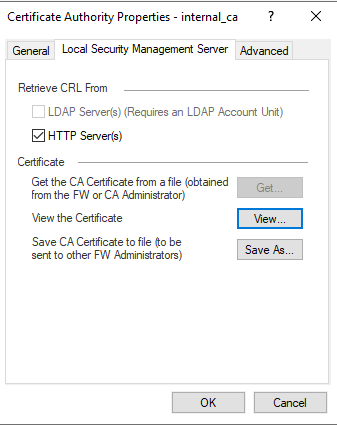
The Certificate Authority Properties window appears.
-
Click the Local Security Management tab.
-
Under Certificate, click View.
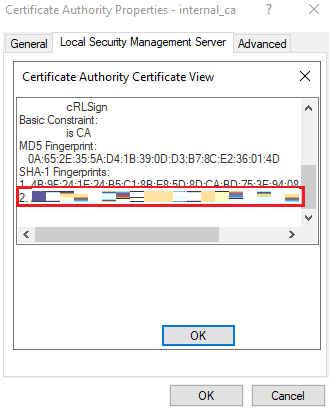
The Certificate Authority Certificate View window appears.
-
Scroll down to SHA-1 Fingerprints. The fingerprint is on line number 2.
-
Manually add the VPN site in the client. For more information, see Endpoint Security Clients User Guide.
-
After you add and connect to the VPN site successfully, In Registry Editor, go to Computer\HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\CheckPoint\accepted_cn.
-
It displays a folder with the display name of your VPN site.
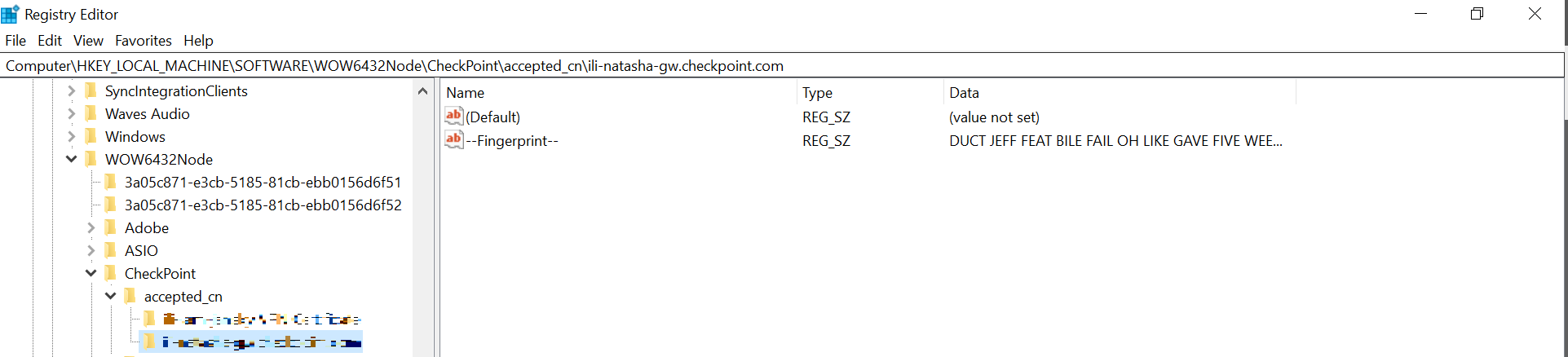
-
Double-click the folder.
-
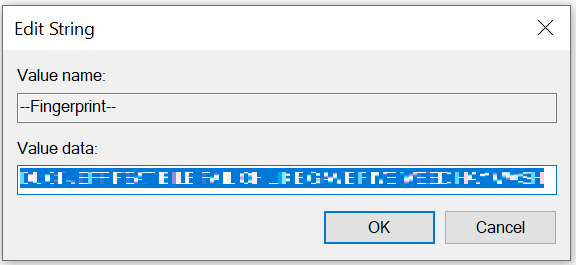
In the right pane, under Name, double-click -- Fingerprint--.
The Edit String window appears.
-
Copy the fingerprint key from the Value data field.
-
Click Cancel to close the window.
-
Paste the fingerprint key in the Fingerprint field.
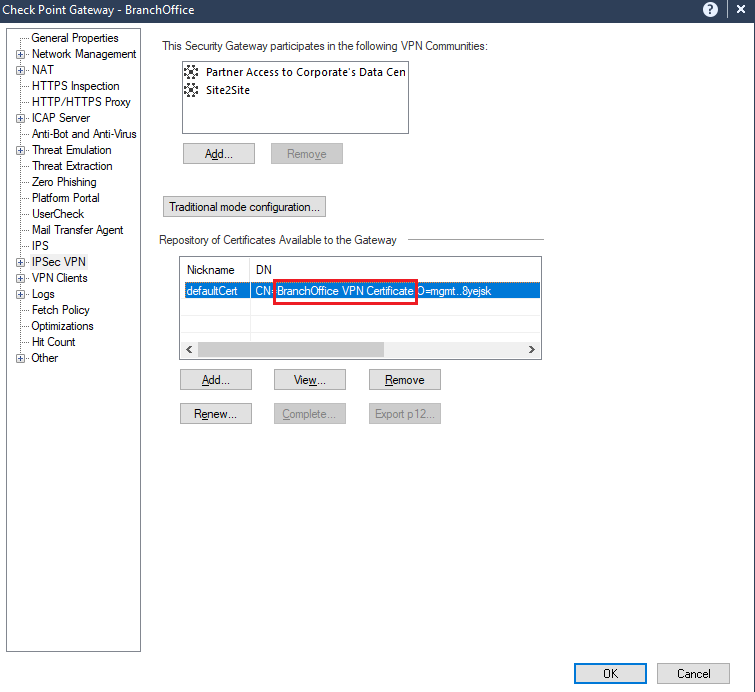
Collecting Remote Access Gateway Name
To get the Remote Access Gateway name from SmartConsole:
-
In SmartConsole, go to Gateways and Servers.
-
Double-click the gateway.
The Check Point Gateway window appears.
-
Double-click IPSec VPN.
-
Under Repository of Certificates Available to the Gateway, in the table, expand the DN column. The value after CN= indicates the remote access gateway name.
To get the remote access gateway name from the device:
-
In Registry Editor, go to Computer\HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\CheckPoint\accepted_cn.
-
It shows a folder with the display name of your VPN site. Copy the folder name and paste it in the Remote Access Gateway Name field.