Monitoring Cybersecurity Events
In this step, you can see which attacks various Check Point cybersecurity engines prevent.
To monitor Cybersecurity Events in Harmony Connect, go to Logs and Events > Internet Access.
The Logs page shows all security events on the sites. You can view the statistics and descriptions of the threats and attacks that Check Point system prevented.
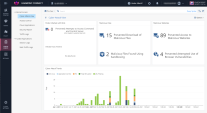
Cyber-Attack View
This window shows the list of all the attacks that Check Point ThreatCloud prevented on your branch offices, and their detailed description:
-
Hosts infected with Bots
-
Malicious Files
-
Malicious Websites
-
Cyber-Attack Trends
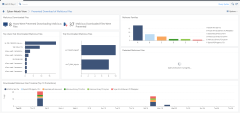
Access Control
This window presents a graphic of the most-accessed services and a timeline of the activity and total traffic. You can see the malicious applications that were prevented by Check Point, their total consumed traffic, and their visibility.
Security Report
Click Security Report to generate a detailed, real-time report of your branch office cybersecurity events and prevented attacks and Access Control. Export your report to Excel, PDF, and Export Template.
To select an option for the report extraction, go to Options > Export.
On the Infinity Portal, you can apply Time filters and view only the events from specified periods.
A basic version of this report is automatically generated for the past 7 days and sent to your email every Sunday.
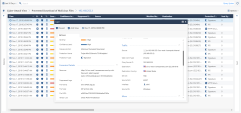
Logs Tab
Presents all the traffic in the system for this service, with their detailed description, in a single table.