Configuration Explorer
CloudGuard Configuration Explorer gives graphical visualizations of the network security of your cloud environment. It shows the hierarchy and structure and your cloud assets and their interconnectivity. These views are arranged to show the level of exposure to the external world. From this, you can identify assets that are misconfigured in the network, or overly exposed. In addition, you can drill down from these views to see details in CloudGuard for the Security Groups or assets and make corrections directly in CloudGuard.
You can use Configuration Explorer to analyze your cloud network for toxic combinations, such as access to sensitive components from the Internet. Or you can troubleshoot it for connectivity issues such as blocked paths to components.
Benefits
-
Logical visualization of inbound traffic to your VPC and its components, and the cloud perimeter
-
Visualize complex networks (for example, with many instances, cross-VPC, cross-region)
-
Easily identify toxic combinations, blocked paths
-
Agent-less & automated information gathering from Cloud environments
-
Automatically classifies protected cloud assets based on the level of exposure to the outer world
-
Real-time topology map of security groups, and the interrelationships between security policies
-
Visualization of traffic flow and dropped traffic between cloud assets - security groups, instances, etc.
-
Real-time topology view of cloud assets
-
Visibility into the interplay between security policies for multi-tier applications and the effective security posture in a cloud environment
-
Similar cross-cloud security visualization experience
-
Contextual VPC Flow Logs
-
Visualize virtual networks connectivity
Configuration Explorer Views
Configuration Explorer offers different views of your Security Groups, each highlighting different aspects of the Security Groups.
The following sections tell how to select and then visualize a cloud environment in Configuration Explorer, how to use the different views, and the actions you can do to see more information.
Security Group View
This view shows the relationship between the Security Groups in your network. They are grouped logically based on exposure to the Internet. Their interconnections are shown.
The steps below tell how to select a network and open this view, and then how to navigate and use the view.
-
Go to Network Security > Configuration Explorer. A list of your cloud accounts appears on the left.
-
Select an account from the list. A list of regions is shown, in which you have cloud environments. The numbers in brackets show the number of assets in the environment.
-
Select a region.
The VPCs in the region are shown as nodes (circles). For an AWS
 Amazon® Web Services. Public cloud platform that offers global compute, storage, database, application and other cloud services. account, the connections between them show peering connections between VPCs.
Amazon® Web Services. Public cloud platform that offers global compute, storage, database, application and other cloud services. account, the connections between them show peering connections between VPCs. -
Click a node. This represents a cloud network. The pane on the right shows the type and number of assets in the network.
-
Click the Legend button on the bottom left. The node color designates the VPC location:
-
Orange: VPC from the selected region
-
Blue: VPC from another region
-
Green: VPC from other Cloud Account
-
Gray: VPC from external CloudGuard Account
-
In this step, the network selected in the previous step is shown in the Security Group![]() A set of access control rules that acts as a virtual firewall for your virtual machine instances to control incoming and outgoing traffic. view. This view is available for AWS cloud accounts only.
A set of access control rules that acts as a virtual firewall for your virtual machine instances to control incoming and outgoing traffic. view. This view is available for AWS cloud accounts only.
-
Go to Network Security > Configuration Explorer > select a VPC (in the previous section) and then select Security Group from the menu bar on the top right.
This shows the Security Group view of the environment.
This view shows the following:
-
The view is divided into logical zones that show the level of exposure to the external world, from the External zone (red, at left), the most exposed, to the Internal zone (green, at right), the least exposed. Security Group nodes are located in the view based on their level of exposure.
-
Each Security Group is shown as a node. Security Groups that are managed by CloudGuard in Full-Protection are shown like this:

Security Groups that are managed as Read-Only are shown like this:

-
In addition, Sources are shown as nodes, with their IP address. These are typically in the External zone (external sources) and the Internal zone (instances).
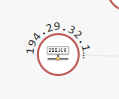
-
Lines between sources and Security Groups show that the address is controlled by the Security Group, that is, that a rule in the Security Group affects the address.
-
Lines between Security Groups show that one Security Group affects the other (by a rule).
-
-
Click on a Security Group node. Other Security Groups affected by it are highlighted, with the direction of the arrow that shows if the other group affects this Security Group (the arrow points to the selected Security Group), or is affected by it (the arrow points from it).
The pane on the right shows details for the Security Group. This shows the following:
-
Sources of inbound network traffic (an external source, or a different Security Group)
-
Targets
-
Assets controlled by rules in the Security Group
-
Inbound and outbound rules
Click the link symbol
 for a Security Group source or target, to open the CloudGuard page for it.
for a Security Group source or target, to open the CloudGuard page for it. -
-
Click on an external source node (on the left, in the External zone). The node is highlighted in the view, and the Security Groups that affect this source are highlighted. The detail pane on the right shows the IP address for the source.
Asset View
This view shows your cloud assets, such as instances and database servers, and the connections between them. Each node in this view shows an asset. They are grouped logically based on their exposure to the internet. Their interconnections are shown.
This view is available for all cloud providers.
-
Go to Network Security > Configuration Explorer > Select a VPC (Select a cloud network), and then select Asset View from the menu bar on the top right.
This shows the Asset View of the selected network.
This view, like the Security Group view, is divided into zones based on the level of exposure.
The view has these elements:
-
Each node is an asset.

-
Lines between nodes are network connections.
-
-
Click a node. The view highlights the connections to other assets, with the direction of the arrow showing the direction of the connection.
The pane on the right shows details for the asset, including the source and target connections (assets or Security Groups that the asset can receive from or send to)
Click a source to see more detail about it on the CloudGuard Protected Asset page.
Click the Flow Logs link at the bottom of the detail pane to see VPC Flow Logs, filtered for the selected asset.
Effective Policy Grouping
The Effective Policy grouping in the Asset view groups nodes (assets) together if they are affected by the same security groups.
The pane on the right shows the grouped assets.
Show Peered VPCs
You can see assets in peered VPCs in the Asset View. Move the Peer VPC switch at the top of the graph, to enable this.
Navigation and Controls
You can use the following controls from the menu bar to change the Security Group or Asset views.
|
Button |
Description |
|---|---|
|
|
Zoom the view in or out. |
|
|
Expand or close groups in the view (based on the selected grouping). |
|
|
Group external sources or Security Groups based on the selected parameter (affects the same assets). |
|
|
Search for elements by name. While you enter text in the text box, the elements with the name that match the text show from the list below the text box. In addition, same elements become highlighted in the visualization map. When you select an element in the search list, the same element is selected it in the map. |