Activity Explorer
Activity Explorer is a tool to search for and see events of interest in your environment's network traffic or event activities. It gathers and presents information from logs for the environments, enriched with information from more sources such as Threat Intelligence feeds, IP reputation databases, and geolocation databases.
Benefits
-
Quickly identify unwanted network traffic from unknown or suspicious sources
-
Identify gaps in cloud security settings or misconfigurations
-
Monitor and analyze user activity on your cloud environments for unusual behavior
Activity Explorer Views
Intelligence combines cloud assets and configuration information with real-time monitoring data from a variety of cloud platform sources and current threat intelligence feeds, IP reputation, and geolocation databases. This results in enhanced visualization that highlights suspicious traffic from legitimate traffic. For example, sources of network traffic from other cloud elements are shown based on type, and malicious external sources are marked as such.
The Activity Explorer provides visualization of event activities in your environment. You can view activities on all of your assets or filter the view for specific assets or activities. You can use this to identify anomalous activities from unwanted and potentially malicious sources or unexpected activities from trusted sources.
Actions
This view shows events in your environment, based on logs, such as CloudTrail for AWS![]() Amazon® Web Services. Public cloud platform that offers global compute, storage, database, application and other cloud services., or Log Search for Azure
Amazon® Web Services. Public cloud platform that offers global compute, storage, database, application and other cloud services., or Log Search for Azure![]() Collection of integrated cloud services that developers and IT professionals use to build, deploy, and manage applications through a global network of data centers managed by Microsoft®..
Collection of integrated cloud services that developers and IT professionals use to build, deploy, and manage applications through a global network of data centers managed by Microsoft®..
-
Navigate to CIEM > Visibility > Activity Explorer.
-
The Activity Explorer page opens and shows all events for all assets in the selected account (during the hour before).
-
To open the Query menu, click
 , in the top left.
, in the top left. -
Select a Query from the list of queries.
-
Click Select this query.
The page is refreshed, with the selected query applied to the log data for the account.
This view has the following elements:
-
The GSL query (2) enables you to search for network resources or network flows. You can specify in the query the details of specific packets, bytes, source, or destination to monitor traffic and interconnectivity of the resources that belong to your environment or cluster. Edit the query text directly in the box or open a graphic query editor.
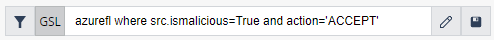
-
The time frame (3) is the period back from the current time (15 min, 1 h, 24 h, 7 d) or start and end dates for a specific time range. To change the time frame for the view, select a new value and click Run (4) to run a new query.


Note - The graph shows only actual traffic between entities. Entities without network activity during the selected time frame are not seen.
-
The Queries icon
 (5) allows you to select a query from an applicable category.
(5) allows you to select a query from an applicable category.
The central part of the view shows a graph of entities in the environment, and the account activities based on the selected query, and the time frame. The entities are grouped in zones that show the direction of activity, Identity, Issuer, and Target Asset. The Identity zone shows entities that did or initiated the activity, and the Target Asset zone shows the assets on which the activity was done. The Issuer zone shows the assets that were used to gain access to the Target, such as a role or token.
The default view groups assets by types (these are the large circles with numbers that show the number of assets). Click
 to ungroup assets.
to ungroup assets.Click on a node in the graph to highlight the events relating to it.
The pane at the right shows details for the node in the INFO tab.
Click on an identity to add it to the query (for example, you can narrow the query to this asset only by adding it as an AND clause to the current query. Or do not include it by adding it as an AND NOT clause).
The target assets list is organized into Top and Least type lists. Select one of the asset types in the list to add it to the query (as above).
-
You can control the view with these controls:
-
zoom: Select a point in the center section of the view, and use your mouse scroll wheel to zoom the display in or out, or use the zoom controls at the top of the view (
 )
) -
Select an entity in the view, to show details, in the pane on the right.
There are three tabs of details:
-
Info - Shows the list of Target Assets with details for each.
-
Statistics - Groups the entities into Identities and Target Assets.
-
Timeline - Shows a list of activities for the selected asset, organized as a timeline (this is only shown if a specific asset is selected, not a group of assets).
Click in the central part of the view (not on an entity), to go back to the previous view, of all entities.
-
- Group entities in clusters based on the entity types with the Group by selector at the top of the view. And then you select if to expand or collapse the groups with the expand/collapse symbol next to the group in the view or at the top of the view(
 ) .
) .
You can view Activity Explorer logs for specific events.
Select an event in the Activity Explorer graph, and then click OPEN LOGS in the detail pane on the right.
Logs for the selected entity show in a new tab.
Click a record in the logs to show more detail, for example, details for the Issuer, Identity, and Target Assets involved in the specific activity.
Click entities in the detail pane to add them to the query more phrases to narrow the query to specific items of interest.
Filter Views
You can filter the Activity Explorer view to focus on events of interest.
Activity Explorer filters
Select filter options from the following:
-
Status - The event status (success or failure)
-
Interactive - The event involved user interaction on the cloud platform console
-
Assets - Select specific asset types
After making changes to these filters, click  to run the query again and update the graph.
to run the query again and update the graph.
Statistics filters
In the Traffic Activity view, you can add more terms to the query based on results in the statistics pane (on the right).
-
Click a detail in the statistics pane.
-
Select the logic with which to add this to the query (AND, OR, NOT). The selected property is added to the query string.
In addition, in the Activity Explorer view, you can select details from the detail pane (on the right).
-
Click on an entity in the detail pane.
-
Select the logic with which to add this to the query (AND, OR, NOT). The selected property is added to the query string.
More Links
