Defining the App Security Policy
|
|
Important Update - Harmony App Protect End of Support
Check Point’s Harmony App Protect will be end of support soon. For more information on key actions and timelines, see Harmony App Protect End-of-Life - Check Point CheckMates. |
You can define a security policy![]() Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. with a set of actions that the Harmony App Protect SDK returns when it detects a security threat.
Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. with a set of actions that the Harmony App Protect SDK returns when it detects a security threat.
Based on the action returned, you must take the necessary action to protect the application on the user device.
For example, if the SDK detects an Ad Malware threat, it responds with a Log Event action.
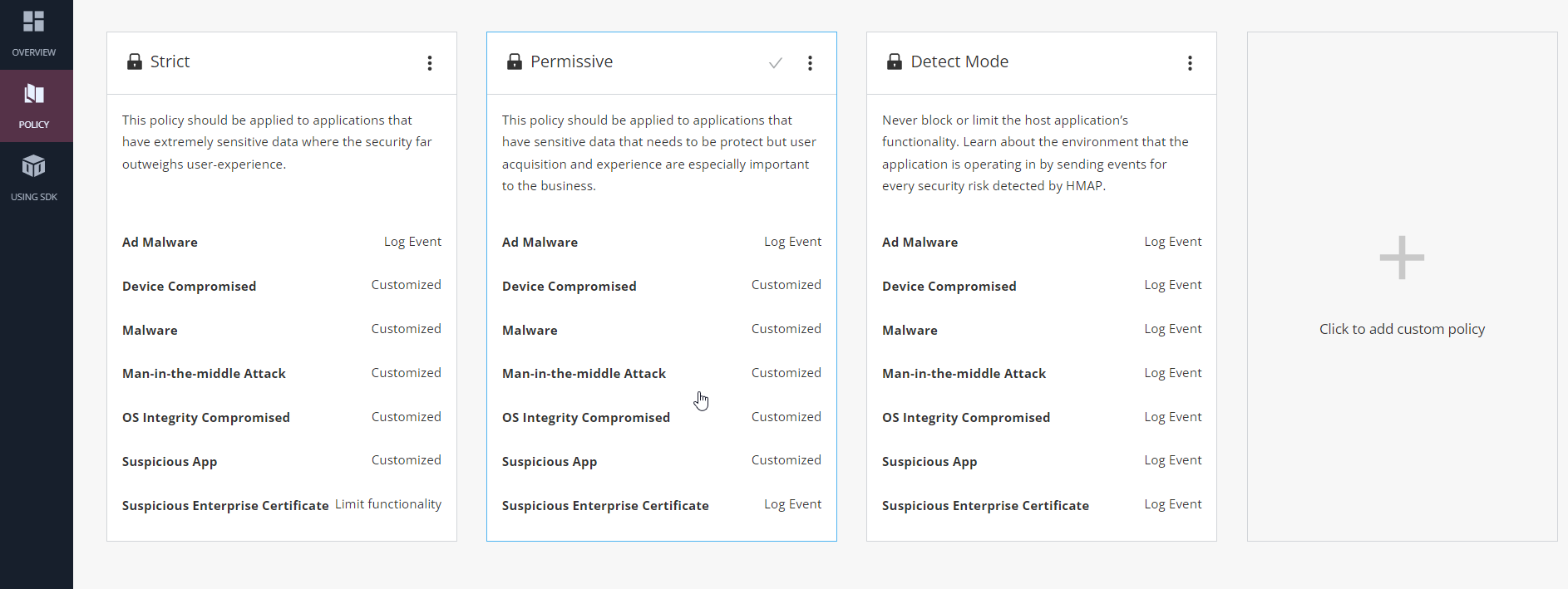
The Harmony App Protect provides four types of policies, from which, you can select and apply a policy. Out of the four policies, only one is customizable and the rest are default and non-customizable.
Default and non-customizable policies:
-
Strict - For applications with extremely sensitive data to protect, where the security outweighs user-experience.
-
Permissive - For applications with sensitive data to protect but user acquisition and experience are more important to the business.
-
Detect Mode - This policy does not block or limit the host application’s functionality. It learns about the application's operating environment by sending events for every security risk that the Harmony App Protect detects.
Customizable policy:
-
Custom Policy - You can customize the action for each threat category and create new actions. For more information, see Adding a Custom Policy.
Viewing Policy Details
To view the policy details, in the Policy menu, either click the policy pane or click the  icon in the top-right corner. It shows the different threat types, their sub-categories, supported OS, and the actions returned by the Harmony App Protect.
icon in the top-right corner. It shows the different threat types, their sub-categories, supported OS, and the actions returned by the Harmony App Protect.
This table lists the different threat types, threat categories, and supported OS.
|
Threat Type |
Threat Category |
Supported OS |
Description |
|---|---|---|---|
|
Ad Malware
|
Hidden Clicker |
Android |
The application simulates clicks in the background to generate traffic for one of these purposes:
|
|
Rough Ad-Network |
Android |
The application contains ad-network with dangerous capabilities that can leak sensitive data from the device and violates your policy. |
|
|
Device Compromised
|
Device Encryption disabled |
Android |
The device encryption is disabled. |
|
Device has an out of date OS version |
iOS |
The device OS is out of date. |
|
|
Screen lock protection disabled |
Android iOS |
The device screen-lock feature is disabled. |
|
|
Security Patch Level Outdated |
Android |
The device security patch level is out of date. |
|
|
USB debugging enabled |
Android |
USB debugging is enabled on the device. USB debugging allows an Android device to communicate with a PC that runs the Android SDK to use advanced operations. |
|
|
Unknown Sources Enabled |
Android |
Apps from sources other than the Play Store can be installed on the device. |
|
|
Malware
|
Botnet |
Android |
The application is part of a network of remotely controlled applications that carries out distributed attacks. |
|
Dropper |
Android |
The application drops malware into the device. |
|
|
Fake app |
Android |
The application appears to be legitimate. |
|
|
Financial Information Stealing App |
Android |
The application steals sensitive financial information. |
|
|
Hacking Tool |
Android |
The application compromises local network data, device data or application data. It can be used for authorized testing or for malicious purposes. |
|
|
Info Stealer |
Android |
The application collects and sends sensitive data from the device. |
|
|
Malware |
Android |
A malware application with dangerous capabilities. |
|
|
Man-In-The-Middle Attack App |
Android |
The application wiretaps network traffic through Man-in-the-Middle (MITM) attacks. |
|
|
Mobile Remote Access Tool |
Android |
The application logs user activity, performs surround recordings and collects personal information. |
|
|
Phishing App |
Android |
The application pretends to be a legitimate app to gather sensitive information. |
|
|
Premium Dialer |
Android |
The application sends SMS messages or calls premium numbers that may cause excessive monetary charges. |
|
|
Ransomware |
Android |
The application blocks the device or access to critical data and demands a ransom to unlock the device or data. |
|
|
Rootkit |
Android |
The application roots the device to perform malicious actions with elevated privileges. |
|
|
SMS Bot |
Android |
The application sends SMS messages in the background for malicious purposes. |
|
|
Man-in-the-middle Attack (MITM)
|
Android iOS |
Address Resolution Protocol (ARP) attack attempt which allows an unauthorized third party to gain access to the device's network traffic. |
|
|
MITM - SSL |
Android iOS |
MITM attack that intercepts network traffic redirection from HTTP to HTTPS and strips the HTTPS call as HTTP. |
|
|
SSL Interception (Advanced) |
Android iOS |
MITM attack that uses a valid certificate that does not match the server certificate, to intercept HTTPS traffic. |
|
|
SSL Interception (Basic) |
Android iOS |
MITM attack that uses an invalid certificate that does not exist on the device's trusted certificates or is not trusted by a root Certificate Authority (CA), to intercept HTTPS traffic. |
|
|
OS Integrity Compromised
|
Jailbroken Device |
iOS |
Privilege escalation to remove the Apple software restrictions on iOS. |
|
Rooted Device |
Android |
Android users gain privileged control (known as root access) over various Android subsystems. |
|
|
Non-Standard Rooting |
Android |
Rooting performed in a non-standard way. |
|
|
SELinux |
Android |
SE Linux is not enforced on the device. |
|
|
Verified boot is disabled |
Android |
When the user boots an Android device, this feature ensures that its state is not changed from the last used state. |
|
|
Suspicious App
|
Dangerous App |
Android |
A legitimate application used by a malicious user to compromise a device, cause configuration changes, or allow unauthorized access to corporate resources. |
|
Device Tracking Tool |
Android |
Allows remote access to the device's location and enables remote control, mostly without the user's consent. |
|
|
Location Tracking |
Android |
Allows remote access to the device's location without the user's consent. |
|
|
Network Redirection Tool |
Android iOS |
Redirects network communication without the user's consent. |
|
|
Not original certificate |
Android |
The application is signed with a fake certificate. |
|
|
Remote Access Tool |
Android |
Allows remote control of the device without the user's consent. |
|
|
Rooting Tool |
Android |
The application is detected as a rooting or jail-break tool that exposes the device to security threats. |
|
|
Suspected Malware |
Android |
The application is suspected to be malicious and must be analyzed further by Check Point's advanced detection engines. |
|
|
Suspicious App |
Android |
The application includes suspicious capabilities. |
|
|
Suspicious Enterprise Certificate
|
Developer Certificate Profile |
iOS |
A developer certificate profile that must be only used for official internal apps development is installed on the device. |
|
Enterprise Certificate Profile |
iOS |
An enterprise certificate profile that must be only used for official internal apps is installed on the device. |
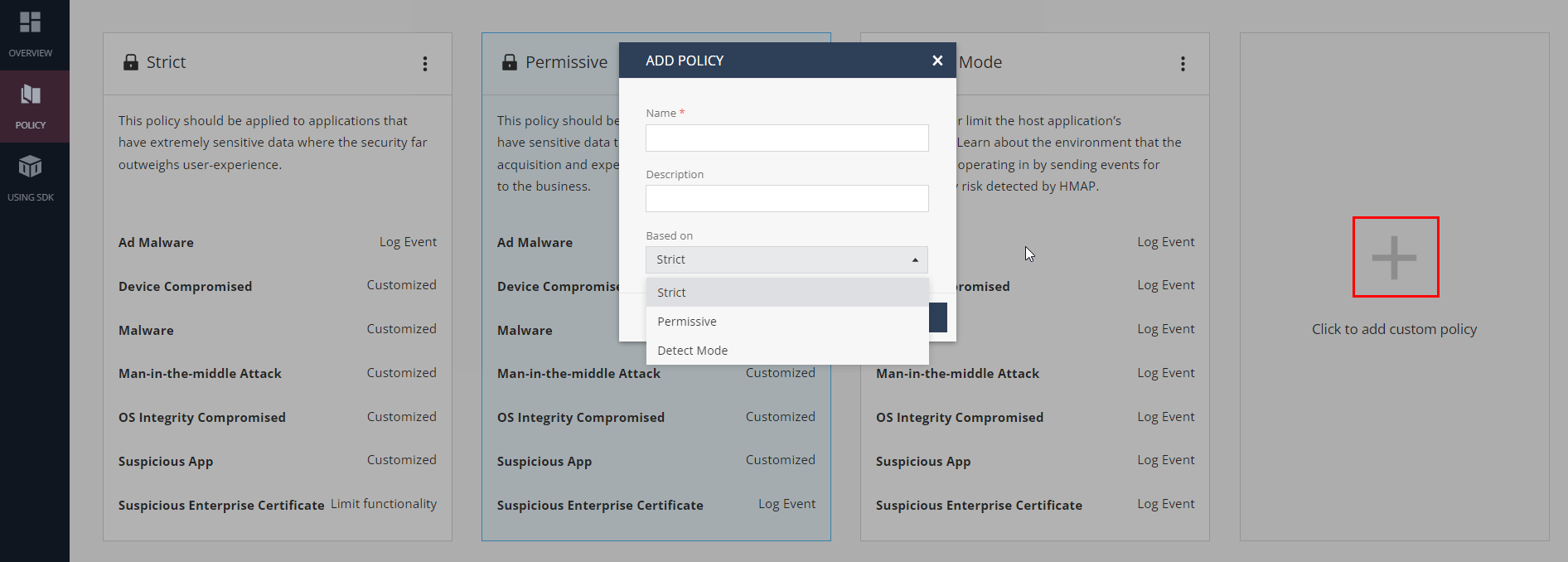
Adding a Custom Policy
-
Go to App Protect > Policy.
Click + in the custom policy pane.
-
In the Add Policy pop-up window, enter this information:
-
Click Add.
The new custom policy appears in the Policy menu.
-
To edit the custom policy Name or Description, click the
 icon in the top-right corner and select Edit.
icon in the top-right corner and select Edit. -
To edit the custom policy settings, click the policy pane or click the
 icon in the top-right corner and select Details.
icon in the top-right corner and select Details.The custom policy page appears.
-
Click the drop-down button to select a threat type (for example, Man-in-the-middle Attack) to view the threat categories.
-
From the corresponding drop-down list, select an action for each threat category.
 Note - If you set the same action for all the threat categories, the threat type's combo box displays the same action. If you set different actions for the threat categories, the threat type's combo box displays Customized.
Note - If you set the same action for all the threat categories, the threat type's combo box displays the same action. If you set different actions for the threat categories, the threat type's combo box displays Customized.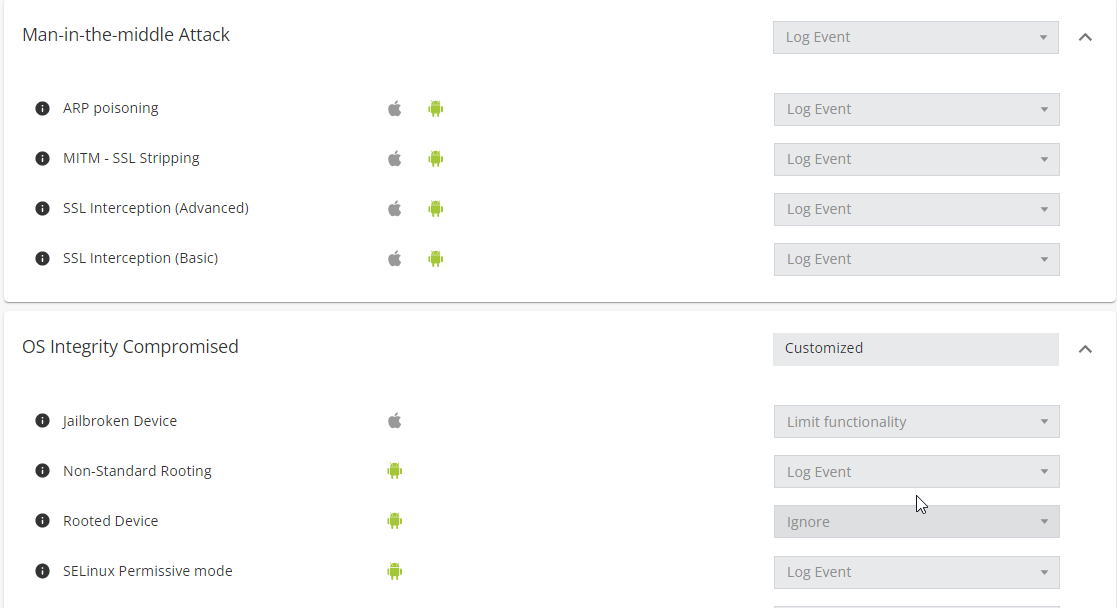
-
To set a new action to send to the hosting application:
-
Click Add action.
-
In the Add Action pop-up window, enter this information:
-
Display name - Name of the action.
-
Return code - The action text that the SDK returns.
-
(Optional) Description
-
For example, you define a new action Send Email. If the Harmony App Protect detects a threat in the application, the SDK returns Send Email to the hosting application which tells the app to send an email.
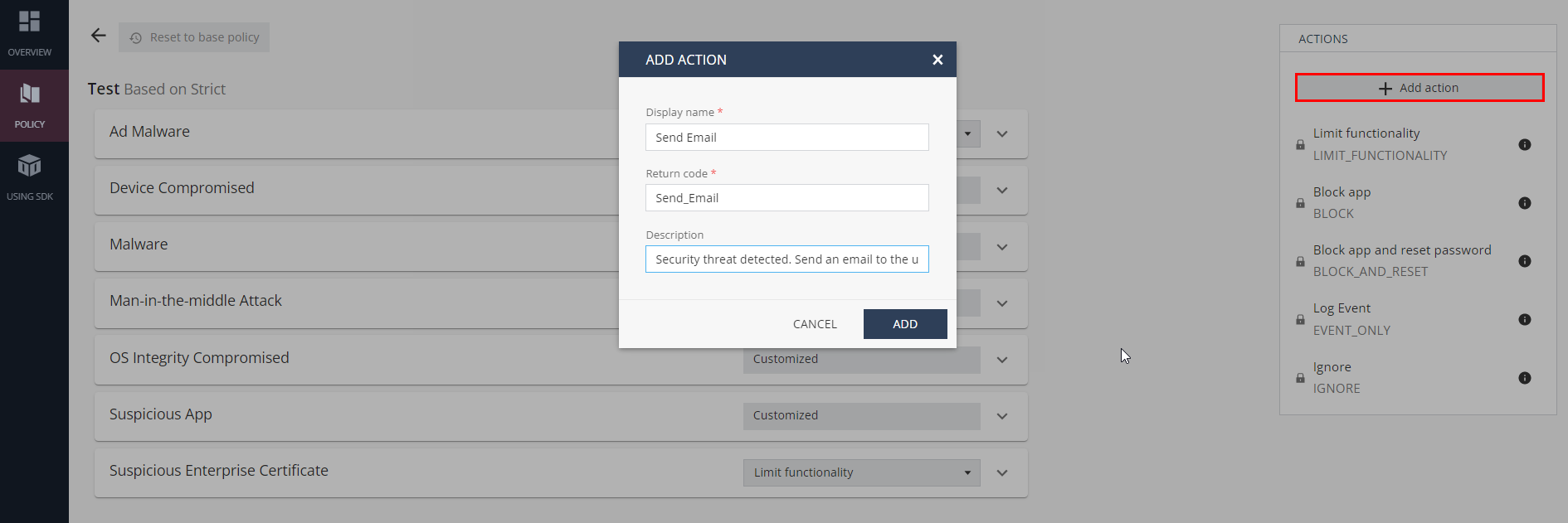
-
-
Click Add.
The new action is added to the action list.
-
To edit the action, click the
 icon.
icon.To delete the action, click the
 icon.
icon. Note - You cannot edit the pre-defined actions ( Limit functionality, Block App, Log Event).
Note - You cannot edit the pre-defined actions ( Limit functionality, Block App, Log Event). -
To reset the custom policy to the default, click Reset to base policy.
The policy that you selected in base policy is assigned to the device.
Selecting a Policy
-
Go to Policy menu.
-
For the policy that you want to select, click the
 icon in the top-right corner of the policy pane and select Use this policy.
icon in the top-right corner of the policy pane and select Use this policy.