Identity Collector
This section describes how to configure an Identity Collector![]() Check Point dedicated client agent installed on Windows Servers in your network. Identity Collector collects information about identities and their associated IP addresses, and sends it to the Check Point Security Gateways for identity enforcement. For more information, see sk108235. You can download the Identity Collector package from sk134312. (a type of Identity Client) for a Microsoft Server.
Check Point dedicated client agent installed on Windows Servers in your network. Identity Collector collects information about identities and their associated IP addresses, and sends it to the Check Point Security Gateways for identity enforcement. For more information, see sk108235. You can download the Identity Collector package from sk134312. (a type of Identity Client) for a Microsoft Server.
The Check Point Identity Collector serves as a specialized client agent that is deployed on Windows Servers within your network infrastructure.
Functionally, the Identity Collector is responsible for gathering identity-related data, which includes corresponding IP addresses, and subsequently transmites this information to the Check Point Security Gateway![]() Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources.. This exchange of data facilitates identity-driven enforcement measures.
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources.. This exchange of data facilitates identity-driven enforcement measures.
To facilitate its operation, the Identity Collector leverages the Windows Event Log mechanism to retrieve security logs from the Domain Controller. The Windows Event Log functionality is an integral part of the operating system, available both for client systems (starting from Windows Vista) and server systems (starting from Windows Server 2008).
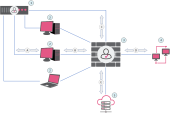
Example Topology and Traffic Flow
|
Item |
Description |
|---|---|
|
1 |
Windows Server with Identity Collector installed |
|
2 |
User endpoint computers |
|
3 |
|
|
4 |
Internal resources |
|
5 |
|
|
A |
Endpoint users authenticate on the Windows Server (1) |
|
B |
User endpoint computers (2) communicate with the Identity Awareness Gateway |
|
C |
Identity Collector on the Windows Server (1) sends user and machine identities to the Identity Awareness Gateway |
|
D |
Identity Awareness Gateway grants or denies access to internal resources (4) based on the Access Control Policy |
|
E |
Security Management Server |
These are the benefits of using Identity Collector instead of a standard AD Query![]() Check Point clientless identity acquisition tool. It is based on Active Directory integration and it is completely transparent to the user.
The technology is based on querying the Active Directory Security Event Logs and extracting the user and computer mapping to the network address from them. It is based on Windows Management Instrumentation (WMI), a standard Microsoft protocol.
The Check Point Security Gateway communicates directly with the Active Directory domain controllers and does not require a separate server.
No installation is necessary on the clients, or on the Active Directory server.:
Check Point clientless identity acquisition tool. It is based on Active Directory integration and it is completely transparent to the user.
The technology is based on querying the Active Directory Security Event Logs and extracting the user and computer mapping to the network address from them. It is based on Windows Management Instrumentation (WMI), a standard Microsoft protocol.
The Check Point Security Gateway communicates directly with the Active Directory domain controllers and does not require a separate server.
No installation is necessary on the clients, or on the Active Directory server.:
-
Reduced load on the Security Gateway - Identity Collector does the queries instead of the Security Gateway
-
Reduced load on the Domain Controller (DC) - the native Windows API consumes fewer resources
-
Lower permissions required - Identity Collector requires read-only access to the domain security logs
-
No changes are required in the Active Directory (AD) schema.
-
One Identity Collector can serve multiple Security Gateways, even from a different Domain Management Servers on a Multi-Domain Server
 Dedicated Check Point server that runs Check Point software to host virtual Security Management Servers called Domain Management Servers. Synonym: Multi-Domain Security Management Server. Acronym: MDS..
Dedicated Check Point server that runs Check Point software to host virtual Security Management Servers called Domain Management Servers. Synonym: Multi-Domain Security Management Server. Acronym: MDS.. -
Identity Collector can communicate with a maximum of up to 35 Active Directory (AD) servers.
-
Identity Collector can process a maximum of 1900 Active Directory (AD) events per second.
|
|
Note - For the support of Identity Collector on Quantum Spark Appliances, see sk159772 and sk178604. |
To set up the Identity Collector in High Availability mode, follow these steps:
-
Install the Identity Collector on two separate Windows servers.
-
Make sure that both Windows servers have identical configurations.
After installed, the Identity Collector performs the following tasks on each Windows server:
-
Collects events from AD/ISE Servers.
-
Forwards the collected events to the Security Gateway.
-
|
|
Note - If there are any duplicate events, the Security Gateway automatically disregards them. |