Creating Custom Identity Clients
You can use the Identity Agent Configuration Utility![]() Check Point utility that creates custom Identity Agent installation packages. This utility is installed as a part of the Identity Agent: go to the Windows Start menu > All Programs > Check Point > Identity Agent > right-click the 'Identity Agent' shortcut > select 'Properties' > click 'Open File Location' ('Find Target' in some Windows versions > double-click 'IAConfigTool.exe'). to create custom installation packages for:
Check Point utility that creates custom Identity Agent installation packages. This utility is installed as a part of the Identity Agent: go to the Windows Start menu > All Programs > Check Point > Identity Agent > right-click the 'Identity Agent' shortcut > select 'Properties' > click 'Open File Location' ('Find Target' in some Windows versions > double-click 'IAConfigTool.exe'). to create custom installation packages for:
-
Identity Agent for a Terminal Server
The Identity Agent Configuration Utility "IAConfigTool.exe" is installed as part of Identity Agent for a User Endpoint Computer and Identity Agent for a Terminal Server..
Identity Agent for a User Endpoint Computer and Identity Agent for a Terminal Server. have many advanced configuration parameters.
Some of these parameters are related to the installation process, while others are related to Identity Client functionality.
All of the configuration parameters have default values that are configured with the product and can remain unchanged.
Installing Microsoft .NET Framework
You must install Microsoft .NET Runtime framework 4.0 or higher before you install and run the Identity Agent Configuration Utility.
Working with the Identity Agent Configuration Utility
Getting the source MSI File
To create a custom Identity Client installation package, you must first download the customizable MSI file from sk134312 to your management computer. This is the computer, on which you use the Identity Agent Configuration Utility.
Running the Identity Agent Configuration Utility
You must install the Identity Client on your management client computer. The Identity Agent Configuration Utility is installed in the Identity Agent installation directory.
To run the Identity Agent Configuration Utility:
-
Go to the Identity Agent installation directory.
-
Click Start > All Programs > Check Point > Identity Agent.
-
Right-click the Identity Client shortcut and select Properties from the menu.
-
Click Open File Location (Find Target in some Windows versions).
-
Example path on Windows 32-bit:
C:\Program Files\CheckPoint\Identity Agent\IAConfigTool.exe -
Example path on Windows 64-bit:
C:\Program Files (x86)\CheckPoint\Identity Agent\IAConfigTool.exe
-
-
-
Double-click IAConfigTool.exe.
The Identity Agent Configuration Utility opens.
Example:
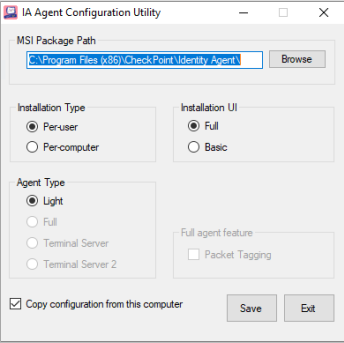
Configuring the Identity Client
You must configure all the features and options in the Identity Agent Configuration Utility window:
-
MSI Package Path
Enter or browse to the source installation package. You must use a Check Point customizable MSI file as the source.
Installation Type
Select whether the Identity Client applies to one user or to all users of the computer, on which it is installed.
-
Per-User - Install the Light Identity Agent only for the user who does the installation. Administrator permissions are not necessary for this installation.
-
Per Computer - Install any Identity Agent type for all users on the computer. Administrator permissions are necessary for this installation type.
-
-
Installation UI
Select one of these end user interaction options:
-
FULL (Default) - Interactive installation where the end user sees the full installation interface and can select options.
-
BASIC - Non-interactive installation where the end user only sees a progress bar and a Cancel button.
Identity Client Type
Select the type of Identity Client to install:
-
Full Identity Agent for a User Endpoint Computer - Predefined Identity Client includes packet tagging and computer authentication. It applies to all users of the computer that it is installed on. To use the Full Identity Client type, Administrator permissions are necessary.
-
Light Identity Agent for a User Endpoint Computer - Predefined Identity Client that does not include packet tagging and computer authentication. You can install this Identity Client individually for each user on the target computer. Administrator permissions are not necessary. You must select the Per-Computer installation type for this agent type.
-
Terminal Server Identity Agent Version 1 (MUH v1) - Predefined Identity Client that installs MAD services and the Multi-user host driver on Citrix and Terminal Servers. This Identity Client type cannot be used for endpoint computers.
-
Terminal Server Identity Agent Version 2 (MUH v2) - Predefined Endpoint Identity Client that installs MAD services and the Multi-User Host (MUH) 2 driver on Citrix and Terminal Servers. This Endpoint Identity Client type cannot be used for endpoint computers.
-
-
Full agent feature
Select this feature for the Full Identity Agent:
Packet Tagging - Install the packet tagging driver to enable anti-spoofing protection. The driver signs every packet that is sent from the computer. This setting is necessary if you have Firewall rules that use Access Roles and IP Spoofing is enabled.
-
Copy configuration
Copy configuration from this computer - Copy Identity Client configuration settings from this computer to other computers running a custom MSI file.
-
Click Save to save this configuration to a custom MSI file. Enter a name for the MSI file.
Configuring a Custom Identity Client with the Captive Portal
To configure a custom Identity Client with the Captive Portal:
-
Upload the custom
customAgent.msipackage to this directory on the Identity Awareness Check Point Software Blade on a Security Gateway that enforces network access and audits data based on network location, the identity of the user, and the identity of the computer. Acronym: IDA. Gateway:
Check Point Software Blade on a Security Gateway that enforces network access and audits data based on network location, the identity of the user, and the identity of the computer. Acronym: IDA. Gateway:/opt/CPNacPortal/htdocs/nacclients/ -
Configure the Captive Portal
 A Check Point Identity Awareness web portal, to which users connect with their web browser to log in and authenticate, when using Browser-Based Authentication. to distribute the custom Identity Client:
A Check Point Identity Awareness web portal, to which users connect with their web browser to log in and authenticate, when using Browser-Based Authentication. to distribute the custom Identity Client:-
Connect with SmartConsole
 Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on. to the Management Server
Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on. to the Management Server Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server. that manages this Identity Awareness Gateway.
Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server. that manages this Identity Awareness Gateway. -
From the left navigation panel, click Gateways & Servers.
-
Open the Identity Awareness Gateway object.
-
From the left tree, click the Identity Awareness page.
-
Near the Browser-Based Authentication option, click the Settings button.
-
In the section Identity Agent Deployment from the Portal, select Require users to download and select to Identity Client - Custom.
-
Click OK to close the Portal Settings window.
-
-
Click OK to close the Check Point Gateway window.
-
Install the Access Control Policy on this Identity Awareness Gateway.
