Identity Agent for a Terminal Server
This section is an introduction to Identity Agent![]() Check Point dedicated client agent installed on Windows-based user endpoint computers. This Identity Agent acquires and reports identities to the Check Point Identity Awareness Security Gateway. The administrator configures the Identity Agents (not the end users). There are two types of Identity Agents - Full and Light. You can download the Full and Light Identity Agent package from the Captive Portal - 'https://<Gateway_IP_Address>/connect' or from sk134312. (a type of Identity Client) for a Microsoft Terminal Server (also known as Multi-User Host (MUH).
Check Point dedicated client agent installed on Windows-based user endpoint computers. This Identity Agent acquires and reports identities to the Check Point Identity Awareness Security Gateway. The administrator configures the Identity Agents (not the end users). There are two types of Identity Agents - Full and Light. You can download the Full and Light Identity Agent package from the Captive Portal - 'https://<Gateway_IP_Address>/connect' or from sk134312. (a type of Identity Client) for a Microsoft Terminal Server (also known as Multi-User Host (MUH).
Identity Agent for a Terminal Server can identify user accounts that belong to an Active Directory domain, including service accounts. Identity Agent for a Terminal Server communicates with the Identity Awareness![]() Check Point Software Blade on a Security Gateway that enforces network access and audits data based on network location, the identity of the user, and the identity of the computer. Acronym: IDA. Gateway over SSL (by default, port 443).
Check Point Software Blade on a Security Gateway that enforces network access and audits data based on network location, the identity of the user, and the identity of the computer. Acronym: IDA. Gateway over SSL (by default, port 443).
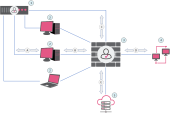
Example Topology and Traffic Flow:
|
Item |
Description |
|---|---|
|
1 |
Windows Server with Identity Agent for a Terminal Server installed |
|
2 |
User endpoint computers |
|
3 |
Identity Awareness Gateway |
|
4 |
Internal resources |
|
5 |
|
|
A |
Endpoint users authenticate on the Windows Server (1) |
|
B |
Endpoint user computers (2) communicate with the Identity Awareness Gateway (3) |
|
C |
Identity Agent for a Terminal Server on the Windows Server sends user and machine identities to the Identity Awareness Gateway (3) |
|
D |
Identity Awareness Gateway (3) grants or denies users access to internal resources according to the Access Control Policy |
|
E |
Security Management Server |
Comparing Terminal Server Identity Agent Versions
There are different versions of Identity Agent for Terminal Servers:
-
Terminal ServerIdentity Agent Version 1 (MUH v1) - Based on source ports. Supports older versions of Windows Server that MUH v2 does not support.
-
Terminal ServerIdentity Agent Version 2 (MUH v2) - Based on packet tagging. Supports more simultaneous users and more features than MUH v1. MUH v2 is a new installation, and is not an upgrade for MUH v1.
Known Limitations
-
Terminal Server Identity Agent Version 2 (MUH v2) supports only TCP and UDP protocols. It does not support other protocols such as ICMP. For unsupported protocols, such as ICMP, the Terminal Server Identity Agent cannot control the network connections. The Identity Server
 Check Point Security Gateway with enabled Identity Awareness Software Blade. is not aware of the user that initiates these connections.
Check Point Security Gateway with enabled Identity Awareness Software Blade. is not aware of the user that initiates these connections. -
IPv6 is not supported.
-
A PDP Security Gateway can support a maximum of 1000 MUH v2 agents connected to it directly. Check Point QA certified this with 20 users per MUH v2 client.
-
Upgrade from Terminal Server Identity Agent Version 1 (MUH v1) to Terminal Server Identity Agent Version 2 (MUH v2) is not supported.
-
Terminal Server Identity Agent Version 1 (MUH v1) does not support applications that do port tunneling on the Terminal Server.
-
When Terminal Server Identity Agent Version 2 (MUH v2) is configured, it is not supported for an application to make decisions based on user context (example: Windows Firewall). This is because when MUH v2 tags traffic, it changes the user context to SYSTEM context.