Introduction
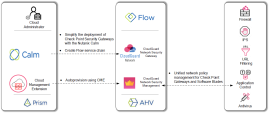
Check Point CloudGuard for Nutanix delivers multi-layered defense to protect East-West traffic in the Nutanix deployed data center. CloudGuard transparently enforces security at the hypervisor level and between Virtual Machines (VMs), and provides comprehensive visibility into Virtual Network traffic trends and threats. CloudGuard Network Security Gateway for Nutanix is automatically deployed as a service Virtual Machine (VM) in a virtual environment. The CloudGuard Gateway secures Nutanix Data Center traffic between VMs across the Virtual Network.
Check Point CloudGuard for Nutanix Flow meets organizational cloud security needs:
-
Next-Generation Firewall with Application Control, Data Awareness, HTTPS Inspection, NAT, and logging
-
IPS and virtual patching of cloud resource
-
URL Filtering for Internet-bound traffic
-
Anti-Bot and Anti-Virus, and Zero-day Threat Emulation and Threat Extraction
-
Automated solution with Nutanix Calm
Costs and Licenses
Customers are responsible for the cost of the Nutanix services used, when they deploy the solution as described in this guide.
The Nutanix Calm Blueprint for the CloudGuard Network Security Gateway includes parameters that you can configure. Some of these features, such as Nutanix Flow, affect the cost and requirements for the deployment. For estimated costs, see Nutanix Software Editions & Licensing.
For CloudGuard Network Security Gateway Private Cloud Images, see sk158292.
The Check Point CloudGuard Security Gateways, Check Point CloudGuard Security Management Server, Nutanix Prism Central, Nutanix Calm Blueprint, and Nutanix Flow described in this guide must have a license.
The license for Check Point CloudGuard Security Gateways is Bring Your Own License (BYOL).
To buy BYOL licenses, contact Check Point Sales.
Prerequisites
Before you use this solution, make sure to read the Nutanix terms and services:
-
Nutanix Prism Central
-
Nutanix Calm
-
Nutanix Flow
If you are new to Nutanix, see Getting Started with Nutanix.
Architecture
The diagram shows Check Point CloudGuard Network Security Gateway Solution for Nutanix Flow, a solution which includes:
-
Nutanix Calm multi-cloud application management framework
-
Nutanix Flow security feature that allows for firewall-type protection at the VM layer
-
Nutanix AHV (Acropolis Hypervisor) enterprise-ready hypervisor
-
Check Point Cloud Management Extension (CME), provides automatic provisioning of CloudGuard Network Security Gateways
-
Prism Central, a centralized management solution for Nutanix environments
-
Check Point R81 Security Management
-
Check Point R81 CloudGuard Network Security Gateway
When integrated with Check Point CloudGuard Network Security Gateways, Nutanix Flow ability to control traffic is increased with the best threat prevention capabilities. Micro-segmentation can deduce the total sum of vulnerabilities, while it helps to secure your assets and data in the Nutanix Data Center against the most sophisticated threats with multi-layered protections including: Firewall, IPS, Application Control, Antivirus, Anti-Bot, and award-winning SandBlast Threat Emulation and Threat Extraction technologies.
Integration Diagram:
Solution Overview
When integrating with Check Point Network Security Gateways, Nutanix Flow's ability to control traffic is augmented with industry leading threat prevention capabilities. Nutanix and Check Point have partnered to deliver an integrated solution with Check Point CloudGuard, which allows companies to realize the full potential of the SDDC and protect against potential vulnerabilities, malware, and other sophisticated threats. The joint solution for Nutanix Data Center effectively addresses one of the key challenges of modern data center networks, securing workloads at the perimeter with Check Point's industry leading edge firewall.
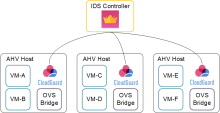
CloudGuard Network Security Gateways are placed on each AHV host and controlled by Check Point Security Management.
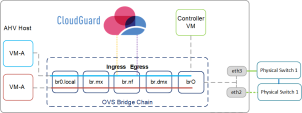
OVS Bridge Chain
The bridge mode operation intercepts traffic and has the ability to block traffic before it is sent along. Bridge network functions have ingress and Egress interfaces. In the diagram, the HR VM traffic is redirected through a bridge CloudGuard Security Gateway. This configuration is deployed on each AHV host in the cluster.
Use Cases
These are examples of how you can set up your Nutanix Flow Gateway architecture.
Micro-Segmentation
Micro-Segmentation is a component of Nutanix Flow networking that simplifies policy management. Micro-Segmentation uses Multiple Prism Central categories (logical groups), a powerful, distributed firewall that gives administrators an application-centric policy management tool for securing traffic.
Micro-Segmentation helps deduce the sum of vulnerabilities, by preventing activities along the east-west traffic in the perimeter. This is established by deploying CloudGuard Network Security Gateways integrated with Nutanix Flow. Nutanix Calm Blueprint creates a service chain and Security Gateways on each AHV host. Together with Nutanix Flow, you can redirect traffic to the CloudGuard Network Security Gateway in the service chain for inspection, based on the user-defined Nutanix Flow Policy.
Virtual Desktop Infrastructure
Nutanix Flow can separate groups of virtual desktops with a Security Policy and work with CloudGuard Network Security Gateways on Acropolis Hypervisor (AHV) to examine and enforce application layer traffic and block threats across the virtual desktop infrastructure.
Security Policy
A Security Policy package is a collection of different types of policies that are enforced after you install the policy on the CloudGuard Network Security Gateways.
A policy package can have one or more of these policy types:
-
Access Control
-
Desktop Security
-
Threat Prevention
The Standard policy package is the default Security Policy defined in a newly deployed Security Management Server. Each policy package has a default cleanup rule that drops all traffic.
When you configure the Check Point Security Management Server with the Cloud Management Extension (CME) utility, specify the name of the Security Policy package to install on the CloudGuard Network Gateways with the "-po" parameter. For the default Security Policy, use the value "Standard" (a capital "S" is required), for this parameter.
To configure more policy packages and install a different policy package on the Security Gateways deployed for the Nutanix Flow solution, then specify the policy package's name when you run cme_menu. Afterward, create and configure the policy by connecting to your Security Management Server with SmartConsole.
For more information, see the "CME Structures and Configurations" section in the Cloud Management Extension R80.10 and Higher Administration Guide.