Introduction to CloudGuard
Check Point CloudGuard for VMware NSX delivers multi-layered defense to protect East-West traffic within the VMware deployed Data Center. CloudGuard transparently enforces security at the hypervisor level between Virtual Machines. It automatically quarantines infected Virtual Machines for remediation, and provides comprehensive visibility into Virtual Network traffic trends and threats.
CloudGuard Gateway for NSX-V is automatically deployed as a service Virtual Machine in the VMware virtual environment. It fully integrates with VMware NSX components. The CloudGuard Gateway secures Data Center traffic between Virtual Machines across the Virtual Network.
Basic Deployment with Hypervisor mode
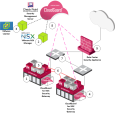
CloudGuard Gateways inspect all traffic that goes to, from, or inside the protected Security Group.
|
Item |
Entity |
Description |
|---|---|---|
|
1 |
ESXi host |
The physical infrastructure is multiple ESXi hosts in an ESXi cluster. |
|
2 |
NSX |
NSX Manager defines Security Groups and the redirection policy. |
|
3 |
vCenter Server |
vCenter manages ESXi hosts. |
|
4 |
CloudGuard Gateway |
Inspects traffic:
|
|
5 |
VMs |
Virtual Machines. |
|
6 |
Protected Security Group |
Collection of vSphere objects protected by NSX. |
|
7 |
Data Center core |
The Data Center switching and routing infrastructure. |
|
8 |
Physical Security Gateway |
Physical enforcement point. |
|
9 |
Check Point Management Server |
Check Point Management Server that is Software-Defined Data Center aware. |
ESXi Host Security Considerations
To learn how to secure your ESXi server, see VMware Best Practices - Security Hardening.
-
Use a separate secured network for the vSphere server management.
-
Permissions required for integration between different solutions should follow the least privileges model. This provides the minimum permissions required for proper function. For example, VMware NSX Manager and Check Point Management Server.
To learn more about VMware roles and permissions, see the best practices in the Managing VMware Virtual Center Roles and Permissions Guide.
 Note:
Note:
CloudGuard Gateway for NSX requires NSX Administrator Permissions and a Read-only role for the vCenter Server.
Requirements for VMware Tools
Install and run VMware Tools on guest Virtual Machines. Redirection of traffic to or from a specific Virtual Machine to the CloudGuard Gateway for NSX (or any other service), requires that NSX map the IP address for that specific Virtual Machine. To get a guest IP address, NSX Manager must have VMware Tools installed. NSX Manager cannot properly redirect workloads that involve Virtual Machines that do not run VMware Tools. See sk109460.
From NSX 6.4, there is no need to install VMware Tools.
CloudGuard for NSX Administration Guide