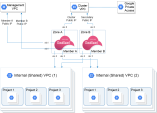
Network
Use this network diagram to configure your system. Make sure to replace the IP addresses in the sample environment with the IP addresses in your environment.
Network Diagram
-
Each CloudGuard Network Security Gateway
 Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. resides in a different GCP
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. resides in a different GCP Google® Cloud Platform is a suite of products and services that includes hosting, cloud computing, database services and more. Zone.
Google® Cloud Platform is a suite of products and services that includes hosting, cloud computing, database services and more. Zone. -
Each gateway has a network interface in a subnetwork (in the Cluster
 Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing. VPC). The CloudGuard Network High Availability
Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing. VPC). The CloudGuard Network High Availability A redundant cluster mode, where only one Cluster Member (Active member) processes all the traffic, while other Cluster Members (Standby members) are ready to be promoted to Active state if the current Active member fails. In the High Availability mode, the Cluster Virtual IP address (that represents the cluster on that network) is associated: (1) With physical MAC Address of Active member (2) With virtual MAC Address. Synonym: Active/Standby. Acronym: HA. solution inspects inbound traffic from this VPC. Therefore, the GCP Firewall rules and routes must be configured to allow all traffic.
A redundant cluster mode, where only one Cluster Member (Active member) processes all the traffic, while other Cluster Members (Standby members) are ready to be promoted to Active state if the current Active member fails. In the High Availability mode, the Cluster Virtual IP address (that represents the cluster on that network) is associated: (1) With physical MAC Address of Active member (2) With virtual MAC Address. Synonym: Active/Standby. Acronym: HA. solution inspects inbound traffic from this VPC. Therefore, the GCP Firewall rules and routes must be configured to allow all traffic. -
Private access to Google APIs must be enabled for this subnetwork. This is to allow the CloudGuard Network High Availability VM instances access to Google APIs to execute a failover
 Transferring of a control over traffic (packet filtering) from a Cluster Member that suffered a failure to another Cluster Member (based on internal cluster algorithms). Synonym: Fail-over. process.
Transferring of a control over traffic (packet filtering) from a Cluster Member that suffered a failure to another Cluster Member (based on internal cluster algorithms). Synonym: Fail-over. process. -
The cluster's public IP address is attached to the network interface of the active
 State of a Cluster Member that is fully operational: (1) In ClusterXL, this applies to the state of the Security Gateway component (2) In 3rd-party / OPSEC cluster, this applies to the state of the cluster State Synchronization mechanism. gateway in this network.
State of a Cluster Member that is fully operational: (1) In ClusterXL, this applies to the state of the Security Gateway component (2) In 3rd-party / OPSEC cluster, this applies to the state of the cluster State Synchronization mechanism. gateway in this network. -
Each gateway has a network interface in a subnetwork in the Management VPC. This is the network that manages the gateways.
-
The gateways have a network interface in each of the internal, optionally shared VPC networks that the cluster secures. In each of the internal VPC networks, a GCP Route routing all outbound traffic (0.0.0.0/0) to the active member is automatically created.
In the diagram:
- The cluster protects two web applications.
Each web application has:
-
Web server
-
Application server
You must manually configure these components:
|
Name |
Attached to |
Use |
|---|---|---|
|
Cluster primary public address |
The external interface (eth0) of the Active Cluster Member |
VPN and publishing services. Do not disable or delete this resource. |
|
Cluster secondary public IP address |
The external interface (eth0) of the Secondary Cluster Member. |
Gets important Check Point updates. Do not disable or delete this resource. |
|
Member A public address |
Management Network Interface of Member A (eth1). |
External management of Member A Do not disable or delete this resource. |
|
Member B public address |
Management Network Interface of Member B (eth1). |
External management of Member B Do not disable or delete this resource. |
Use the primary public IP address of the Active member (eth0) to forward traffic that comes from the Internet.
Important - You cannot use these ports:
-
80
-
443
-
444
-
8082
-
8880
Diagram Components
-
Four Virtual Networks in GCP, each contains four subnets:
-
Cluster
- Management
-
Web
-
App
-
Check Point High Availability consists of two Cluster Members - Member 1 and Member 2.
|
3
|
Destination |
Nexthop |
|
|
Default internet gateway (Default) |
|
|
|
Cluster Virtual Network |
|
4
|
Destination |
Nexthop |
|
|
Default internet gateway (Default) |
|
|
|
|
Management Virtual Network |
|
5
|
Frontend |
Nexthop |
|
|
Virtual Network (Internal VPC 1) |
|
|
|
Default internet gateway (with High Priority 1000) |
|
|
|
Instance Cluster Member-b (with High Priority 2) |
|
|
|
|
Instance Cluster Member-a (with High Priority 1) |
|
6
|
Frontend |
Nexthop |
|
|
Virtual Network (Internal VPC 2) | |
|
|
Default internet gateway (Priority 1000) | |
|
|
Instance Cluster Member-b (Priority 2) | |
|
|
|
Instance Cluster Member-a (Priority 1) |
|
Destination |
Nexthop |
0.0.0.0/0
|
External subnet's (eth0) router |
| Management Public IP | Management subnet's (eth1) router |
10.0.0.0/8
|
Internal subnet's (eth2) router |
172.16.0.0/12
|
Internal subnet's (eth2) router |
192.168.0.0/16
|
Internal subnet's (eth2) router |
|
|
Note - By default Cluster Members route inbound traffic destined to internal networks, defined in the RFC 1918, through the internal interface "eth2". If more than one internal interface is selected, the static routes to their subnets must be validated to avoid overlapping with the default ones |
Failover
- When the active gateway fails, the standby
 State of a Cluster Member that is ready to be promoted to Active state (if the current Active Cluster Member fails). Applies only to ClusterXL High Availability Mode. member will identify the failure
State of a Cluster Member that is ready to be promoted to Active state (if the current Active Cluster Member fails). Applies only to ClusterXL High Availability Mode. member will identify the failure A hardware or software problem that causes a Security Gateway to be unable to serve as a Cluster Member (for example, one of cluster interface has failed, or one of the monitored daemon has crashed). Cluster Member that suffered from a failure is declared as failed, and its state is changed to Down (a physical interface is considered Down only if all configured VLANs on that physical interface are Down)., and then do the following:
A hardware or software problem that causes a Security Gateway to be unable to serve as a Cluster Member (for example, one of cluster interface has failed, or one of the monitored daemon has crashed). Cluster Member that suffered from a failure is declared as failed, and its state is changed to Down (a physical interface is considered Down only if all configured VLANs on that physical interface are Down)., and then do the following:Detach the cluster's public IP address from the failed member
 A Cluster Member that cannot send or accept traffic because of a hardware or software problem..
A Cluster Member that cannot send or accept traffic because of a hardware or software problem..
Detach the cluster's secondary public IP address from the standby member. When the failed members returns to standby state, it will attach this address to itself.
Attach the cluster's public IP address to itself.
- For each of the internal VPC networks:
If Member A becomes the active member, it will create high priority routes that will route all outbound traffic in the internal networks to itself.
Note - A lower priority number equals a higher priority for the route.
If Member B becomes the active member, it will remove the high priority routes created by Member A. The result is that existing, lower priority routes will take effect, and route all outbound traffic in the internal networks to itself.
|
|
Note - This usually happens in less than 40 seconds. This affects East-West, inbound-outbound and VPN tunnel failover. |
|
Use Case |
Expected Failover Time |
Comments |
|---|---|---|
|
Site-to-Site VPN |
Less than 40 seconds |
Depends on GCP API. |
|
Inbound inspection through primary public IP |
Less than 40 seconds |
Depends on GCP API. |
|
Outbound inspection through primary public IP |
Less than 40 seconds |
Depends on GCP API. |
|
East-West inspection |
Less than 30 seconds |
Depends on GCP API. |
Traffic Flows
|
|
Note - Other Virtual Machines cannot be deployed in the Check Point solution subnets. |
-
Packet enters the frontend network interface (eth0) of the Active Cluster Member.
-
The Active Cluster Member decrypts the packet.
-
The Active Cluster Member forwards the packet to its destination.
-
Traffic travels to an Active Cluster Member based on the high priority route.
-
The Active Cluster Member inspects the traffic and forwards it to the destination.
-
Traffic travels from one of the internal servers to the Active Cluster Member.
-
The Active Cluster Member forwards the traffic to the destination.
Traffic travels freely in the subnet without inspection.