Configure CloudGuard Network for GCP MIG
Prerequisites
Make sure these components are configured before proceeding:
-
An external VPC with at minimum one public subnet. You can also create the external VPC during deployment.
-
An internal VPC with at minimum one private subnet. You can also create the internal VPC during deployment.
-
A Check Point Security Management Server
 Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server. running R81 or higher.
Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server. running R81 or higher. -
A group of applications or web servers deployed in the private subnet or in a subnet peered with the MIG backend subnet.
-
For Marketplace deployments - a Google Cloud Platform
 Google® Cloud Platform is a suite of products and services that includes hosting, cloud computing, database services and more. Acronym: GCP. Service Account with the following permissions:
Google® Cloud Platform is a suite of products and services that includes hosting, cloud computing, database services and more. Acronym: GCP. Service Account with the following permissions:-
Compute Admin
-
Cloud Infrastructure Manager Agent
-
Service Account User
-
Infrastructure Manager Service Agent
-
Service Usage Admin
-
Service Usage Consumer
You can also create the service account during the deployment.
-
Configuration steps:
-
Create a Google Cloud Platform Service Account.
-
Configure the Check Point Management Server
 Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server..
Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server.. -
Deploy the Check Point autoscaling Managed Instance Group (MIG).
-
Set up the External Load Balancer.
-
Set up the Firewall and NAT Rules.
Installing a Check Point Management Server
We recommend using Smart-1 Cloud (Check Point's Management Server as a Service) to manage the CloudGuard Network Autoscaling Managed Instance Group (MIG).
For step-by-step instructions on enabling Cloud Management Extension (CME) in Smart-1 Cloud management, refer to Quantum Smart-1 Cloud Administration Guide > Using the settings > Cloud Management Extension (CME) Configuration.
Alternative deployment options for the Check Point Security Management Server include Google Cloud Platform, other cloud platforms, or on-premises.
To control the CloudGuard Security Gateways, make sure:
-
The Management Server can open connections to the CloudGuard Security Gateways.
-
The CloudGuard Security Gateways can open connections to the Management Server (for example, for sending logs).
The autoscaling CloudGuard Security Gateway![]() Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. can be deployed with or without a public IP address.
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. can be deployed with or without a public IP address.
Deployments without a public IP address must have one of these topologies:
-
Install the Security Management Server in the same internal VPC.
-
Install the Security Management Server in a VPC peered with the internal VPC.
-
Install the Security Management Server on-premises and connect it to the internal VPC over Cloud Interconnect.
-
Install the Security Management Server on-premises and connect it to the internal VPC over a Cloud VPN.
To deploy the Security Management Server in GCP![]() See 'Google Cloud Platform'., refer to the Check Point CloudGuard Network Security NGFW and Threat Prevention (BYOL).
See 'Google Cloud Platform'., refer to the Check Point CloudGuard Network Security NGFW and Threat Prevention (BYOL).
|
|
Notes:
|
Creating a Google Cloud Platform (GCP) Service Account
The Check Point Security Management Server uses the GCP Service account to monitor the creation and status of the autoscaling Managed Instance Group. This lets the Security Management Server complete provisioning of these Security Gateways.
To create a GCP service account:
-
Go to https://cloud.google.com/iam/docs/creating-managing-service-accounts.
Use these parameters:
Namecheck-point-autoprovision
Role
Compute Engine \ Compute Viewer
-
Click Create Key > JSON (as the key type). A JSON file is downloaded to your computer.

Note - This JSON file is later used as the credentials file in Configuring the Check Point Management Server.
Deploying the Check Point Autoscaling Managed Instance Group
Deploy one of these Google Cloud Marketplace solutions:
- The Check Point CloudGuard Network Security autoscaling with the Bring Your Own License (BYOL) licensing model,
or
-
The Check Point CloudGuard Network Security autoscaling with the Pay as You Go (PAYG) licensing model.
|
Parameter |
Description |
|---|---|
|
|
The name of the deployment. Deployment name must contain only lowercase characters, numbers, or dashes. It must start with a lowercase letter and cannot end with a dash. |
|
|
Select an existing service account with the required permissions (as explained in the prerequisites section) or create a new one. |
|
|
The zone for deploying instances. The zone determines available computing resources and where your data is stored and used. See GCP Regions and Zones documentation for more information. |
|
|
Select the desired machine series. |
|
|
Select the desired machine configuration. |
|
|
The GCP Autoscaler automatically scales out if the average CPU use exceeds this target. |
|
|
The minimum number of Security Gateways in the autoscaling MIG. |
|
|
The maximum number of Security Gateways in the autoscaling MIG. |
|
|
The type of disk used for deploying the instances (see Choose a disk type for more information). |
|
|
The size of the disk used for deploying the instances. (see Choose a disk type for more information). |
|
|
The MIG's Public IP address will be translated to a private address assigned to the Security Gateway in this external network. Provide an RFC 1918 CIDR block in the Cluster |
|
|
These GCP rules will determine if ICMP / TCP / UDP / SCTP / ESP traffic is enabled by default for the provided IP CIDR sources. |
|
|
Provide an RFC 1918 CIDR block in the Cluster external subnet CIDR field or select a Network and a Subnetwork below the CIDR field. If a range is specified, a new VPC will be created and the deployment will ignore the selected network above. |
|
|
The Check Point Security Gateway version to be deployed. |
|
|
The MIG instance's network interface used to communicate with the Security Management Server.
When |
|
|
The name of the Security Management Server as it appears in the CME configuration file. Use the same name in the autoprovision configuration section Configuring the Check Point Management Server. For example, |
|
|
The configuration template name as it appears in the CME configuration file. Use the same name in the autoprovision configuration section Configuring the Check Point Management Server. For example, |
|
|
The SSH public key used for SSH authentication to the MIG instances. Leave it blank to use all project-wide pre-configured SSH keys. |
|
|
The Secure Internal Communication key that creates trusted connections between Check Point components. Trust is required to install policies on Security Gateways and to send logs between Security Gateways and Security Management Servers. |
|
|
Change the admin shell to enable advanced command line configuration. |
|
|
Do not select this checkbox if you do not want to automatically download Software Blade |
|
|
To manage the environment's security, administrators can connect to the Management Server with SmartConsole For additional security, it is recommended to change the password after deployment. |
|
|
Maintenance mode password hash (relevant only for R81.20 and higher versions). Generate a password hash with the command |
|
|
Select this checkbox to enable Stackdriver Monitoring. |
|
|
To manage the environment's security, administrators can connect to the Management Server with SmartConsole clients and via the Gaia WebUI using this password. For additional security, it is recommended to change the password after deployment. |
|
|
Notes:
|
Configuring Load Balancers
We recommend you to go through Google's Load Balancing documentation at: https://cloud.google.com/load-balancing/docs/network/.
The steps below are for TCP load balancers. Note that HTTP(S) load balancers are also supported and can be used alternatively.
External Load Balancer
You must set up the External (Internet-facing) Load Balancer to receive TCP traffic and distribute it to the pool of Check PointCloudGuardSecurity Gateways.
To create the External Load Balancer, do these steps:
-
Open the Load Balancing section in Google Cloud Console.
-
To create a new Load Balancer, click Create.
-
Select Type > Network Load Balancing. Click Next.
-
Select Passthrough load balancer. Click Next.
-
Select Public facing ("From Internet to my VMs"). Click Configure.
-
For the Backend type, select Backend Service.
-
Enter a name for the new External Load Balancer
Example:
"prod-ext-lb"
In the Backend configuration section:
-
Select the region where you deployed the Security Gateways autoscaling MIG.
-
Select the deployed Security Gateway's autoscaling Managed Instance Group (MIG) from the Instance group drop-down list.
-
In Health check, click Create a new health check.
-
Enter a name for the health check. For example, "
cloudguard-gateways-healthcheck" -
For the Port number, enter 8117.

Note - Other ports are not supported.
-
In the Request path, enter a correct path. The application server listens for HTTP health check requests from this path.
-
Click Save and continue.
-
From Session affinity, select Client IP and protocol.
-
In the Frontend configuration section:
-
Enter a name for the frontend.
Example:
"app1-ext-frontend" -
In IP, select a static public IP address or create a new one.
-
In Port, select the port on which this frontend must listen.
-
Click Review and finalize to review the Load Balancer configuration.
-
To create the Load Balancer, click Ready.
Internal Load Balancer
The Internal Load Balancer (ILB![]() Internal Load Balancer, used to load balance traffic in a virtual network) lets you use a next hop that redirects packets to the Load Balancer's targets and then to the instances in the MIG. You can find the route configuration instructions below.
Internal Load Balancer, used to load balance traffic in a virtual network) lets you use a next hop that redirects packets to the Load Balancer's targets and then to the instances in the MIG. You can find the route configuration instructions below.
When Virtual Machine (VM) instances in your Virtual Private Cloud (VPC) network send traffic to the Internet, the traffic is routed through the load-balanced Security Gateway virtual appliances.
|
|
Note - Using an internal load balancer with a MIG as the backend is supported starting from R81.10. |
To create the Internal Load Balancer, do these steps:
-
Open the Load Balancing section in Google Cloud Console.
-
To create a new Load Balancer, click Create.
-
Select Type > Network Load Balancing. Click Next.
-
Select Passthrough load balancer. Click Next.
-
Select Internal ("Only between my VMs"). Click Configure.
-
Enter a name for the new Internal Load Balancer.
Example:
"prod-int-lb"
In the Backend configuration section:
- Select the region where you deployed the Security Gateway's Auto Scaling MIG.
-
From the Instance group list, select the deployed Security Gateway's Auto Scaling Managed Instance Group (MIG) and select TCP/UDP protocol.

Note - L3 protocols are not supported.
-
In the Health check, click Create a new health check.
-
Enter a name for the health check. For example,
cloudguard-gateways-healthcheck. -
For the Port number, enter 8117.

Note - Other ports are not supported.
-
Click Save and continue.
-
In the Frontend configuration section:
-
Enter a name for the frontend.
Example:
"app1-int-frontend"
-
Select the MIG internal sub-network.
-
In Internal IP, select an existing internal IP address or create a new one.
-
Set the Port to All to make the ILB the internal network's next hop.
-
Click Review to review the Load Balancer configuration.
-
To create the Load Balancer, click Ready.
Implementing the Firewall and NAT Rules for inbound traffic
You must create Firewall and NAT rules to allow traffic to the published service or application. This traffic is then redirected to the Internal Load Balancer.
-
The autoscaling MIG deployed by the Google Cloud Marketplace template creates a network interface in the external and internal networks. Each Security Gateway in the autoscaling Managed Instance Group (MIG) has a dynamic object for each network interface. This allows for easier and clearer configuration of Firewall and NAT rules.
-
A dynamic object is a "logical" object where the IP address is resolved differently for each Security Gateway.
- With a dynamic object for each network interface, you can describe Firewall and NAT rules. This dynamic object uses the network interface on which the Security Gateway sends or receives traffic without explicitly stating its IP address.
These dynamic objects are created automatically on each Security Gateway in the autoscaling fleet:
Network
Interface
Dynamic Object
External
eth0LocalGatewayExternalInternal
eth1LocalGatewayInternal
How to create dynamic objects
|
|
Note - Dynamic objects on the Security Gateway are created automatically. |
To create dynamic objects on the Security Management Server, do these steps:
-
In SmartConsole, connect to the Security Management Server (also referred to as the Domain Management Server).
-
Create a Dynamic Object named
LocalGatewayExternal. For this, in the Object Browser, click New > More >Network Object > Dynamic object. A Dynamic Object window opens.
Note - Skip this step if this Dynamic Object
 Special object type, whose IP address is not known in advance. The Security Gateway resolves the IP address of this object in real time. already exists.
Special object type, whose IP address is not known in advance. The Security Gateway resolves the IP address of this object in real time. already exists. -
Enter the name of the object. For example,
LocalGatewayExternal. -
Click OK,
-
Repeat Step 2 for
LocalGatewayInternal.
How to create the External Load Balancer Host object
|
|
Note - Create a Host object for each Public IP address published on the External Load Balancer. |
-
In the Object Browser, click New > More > Network Object > Host. The Host window opens.
-
Enter a descriptive name (for example,
App1-ELB). -
Enter the External Load Balancer's public IP address.
Example:

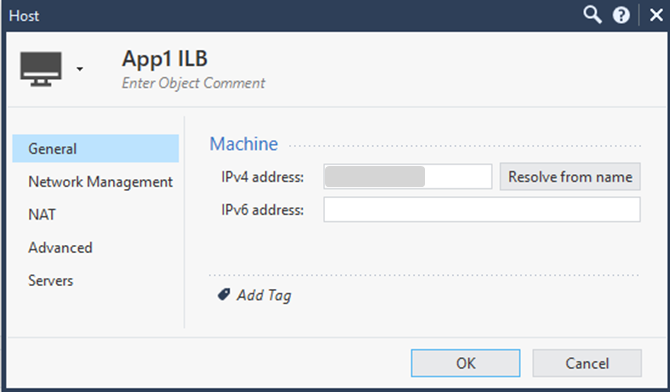
How to create the Internal Load Balancer Host object
|
|
Note - Create a Host object for each Internal Load Balancer. |
-
In the Object Browser, click New > More > Network Object > Host. The Host window opens.
-
Enter a descriptive name (for example,
App1-ILB). -
Enter the Internal Load Balancer's private IP address.
Example:
How to create a new TCP service
|
|
Note - Create a new TCP service for each service port on which the External Load Balancer listens. Skip this step if you use a standard port (such as HTTP 80 or HTTPS 443) that already exists in the services list. |
-
In the Object Browser, click New > More > Service > TCP.
-
Enter a descriptive name (for example,
acme-54321). -
From the General > Protocol list, select the protocol.
-
In the Match By > Port menu , select Customize.
-
Enter the port number (for example,
54321).
|
|
Notes:
|
|
|
Important - You must have an Outbound CA certificate for an inbound SSL inspection use case. |
How to set the HTTPS Inspection
-
In SmartConsole, go to each Security Gateway object and click the HTTPS Inspection tab.
-
Click Server Certificates > Create Certificate.
-
Enter the required information and click OK.
-
Create an HTTPS service similar to the HTTP service created in Implementing the Firewall and NAT Rules for inbound traffic (select port number 8443).
-
In the Security policy, go to the HTTPS inspection table and add this rule:
-
Source: Any
-
Destination: Any (do not use the Internet object)
-
Service: Select the HTTPS service created in External Load Balancer
-
Action: Inspect
-
Certificate: The certificate you created in Step 2
-
-
Save the changes. Click the diskette icon at the top or press CTRL+S.
To enable HTTPS Inspection (as explained in Enabling and Disabling Software Blades):
-
Publish the changes in SmartConsole.
-
Install the Security Policy on any existing CloudGuard Security Gateway.
Configuring the Check Point Management Server
|
Step |
Description |
|||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
1 |
Connect to the command line on the Management Server. |
|||||||||||||||||||||||||||
|
2 |
Log in to Expert mode. |
|||||||||||||||||||||||||||
|
3 |
Install the latest CME version. See sk157492 for instructions on downloading and installing the latest CME version.
|
|||||||||||||||||||||||||||
|
4 |
Run this command:
Where:
|
|||||||||||||||||||||||||||
|
5 |
To apply the modifications, enter yes when prompted "Would you like to restart the service now?", and press Enter. |
|
|
Note - In R81.10 and higher, you can configure CME with the CME API. For more information, see the Cloud Management Extension Administration Guide. |
Updating Auto Provisioning
To download and install the latest Auto Provisioning version, follow the instructions in sk157492 for the latest Cloud Management Extension (CME) updates

