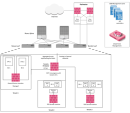
Deploying the CloudGuard Gateway
Preparing a Managed Device
ACI supports physical and virtual L4-L7 devices.
For physical devices, use Check Point appliances. For more information and to verify appliance compatibility, see the CloudGuard for ACI Release Notes.
For virtual devices, use Check Point CloudGuard VE for VMware. For more information, see sk104859.
In the CloudGuard for ACI model, the L4-L7 devices are mapped to Security Gateways that serve as concrete devices. Check Point supports VSX and non-VSX Security Gateways.
When you do the service insertion, the Cisco APIC server supports and provisions Virtual Systems or Security Gateways. See Basic Service Insertion Overview.
Deploying the CloudGuard Gateway for Virtual Devices
To deploy CloudGuard Gateway for virtual devices:
-
Open SmartConsole.
-
For a VSX Gateway, click the New icon (
 ) > VSX > Gateway.
) > VSX > Gateway.The VSX Gateway Wizard opens. Configure the Gateway as a VSX Gateway or a VSX Cluster as described in the R80.40 VSX Administration Guide.
-
For a non-VSX gateway click the New icon (
 ) > Gateway.
) > Gateway.The Gateway Wizard opens. Configure the Gateway as a regular Security Gateway or a Cluster.
-
-
Follow the wizard and verify the SIC and connectivity between the Security Management Server and the VSX Gateway or the Security Gateway.
These ports are allowed by intermediate devices which inspect the management connections. For more information, see sk52421.
For PBR deployments, ClusterXL VMAC mode is required. See sk50840 for configuration details.
For cluster deployment only:
The ClusterXL ARP forwarding mechanism must be disabled.
-
Connect to each of the Cluster Members.
-
Use the Expert Mode to add this configuration line to the
$FWDIR/modules/fwkern.conffile:fwha_enable_arp_resend=0
If the configuration file does not exist on the machine, you must create it. Reboot is required.
Important - Policy installation is required. Make sure to enable the cprid service (runs on TCP 18208).
Deploying the CloudGuard Gateway for Physical Devices
To deploy the CloudGuard Gateway for physical devices:
-
Open SmartConsole.
-
For a VSX Gateway, click the New icon (
 ) > VSX > Gateway.
) > VSX > Gateway.The VSX Gateway Wizard opens. Configure the Gateway as a VSX Gateway or a VSX Cluster as described in the R80.40 VSX Administration Guide.
-
For a non-VSX gateway click the New icon (
 ) > Gateway.
) > Gateway.The Gateway Wizard opens. Configure the Gateway as a regular Security Gateway or Cluster.
-
-
Follow the wizard and verify the SIC and connectivity between the Security Management Server and the VSX Gateway or the Security Gateway.
These ports are allowed by intermediate devices which inspect the management connections. For more information, see sk52421.
For cluster deployment only:
The ClusterXL ARP forwarding mechanism must be disabled.
-
Connect to each of the cluster members.
-
Use the Expert Mode to add this configuration line to the
$FWDIR/modules/fwkern.conffile:fwha_enable_arp_resend=0
If the configuration file does not exist on the machine, you must create it. Reboot is required.
Important - Policy installation is required. Make sure to enable the cprid service (runs on TCP 18208).
For PBR deployments, ClusterXL VMAC mode is required. See sk50840 for configuration details.
Supported Use Cases
CloudGuard for ACI solution supports L2 (GoThrough, transparent), and L3 (GoTo, routed) service function modes.
Before you start the deployment, we recommend that you designate the application profiles, network paths, and contracts that require security service, and determine the optimal insertion method. These considerations are specified in the CloudGuard for ACI TDM document.
ACI deployment topology example:
Basic Service Insertion Overview
Best practice - Use the steps below to insert a service installation into the ACI fabric.
-
Add APIC as a Data Center server object to the R80.40 Security Management Server.
To learn more, see the R80.40 CloudGuard Controller Administration Guide.
-
Create at least one policy package for each tenant.
The APIC service insertion process uses the policy package as the Security Policy Name parameter.
-
Upload the device package. See Uploading the CloudGuard Device Package.
-
Create a logical device for each managed L4-L7 VSX Gateway or non-VSX Security Gateway. See Adding an L4-L7 Device.
-
Create a service graph template. See Creating an L4-L7 Service Graph Template.
-
Apply the service graph to each contract in the fabric that requires security service. See Applying the Service Graph to a Contract.
Uploading the CloudGuard Device Package
You must install the CloudGuard device package on Cisco APICs to enable the insertion of managed L4-L7 Check Point devices. The CloudGuard device package is compatible with APIC versions 1.2 and higher.
You can manually upload the CloudGuard device package into the Cisco APIC. See the Cisco Administration Guide > Installing Device Packages. You can do this automatically with the vsec_config utility.
To configure a device package username:
-
Connect to the Security Management Server through CLI.
-
Run the
vsec_configutility > select Cisco ACI configuration > select APIC L4-L7 Device User > select Set Username.
Note - The username is the R80.40 admin name that the user wants to use for ACI provisioning actions. The user must set a read/write profile to assign use permissions.
To automatically upload a device package:
To upload the device package directly from the Check Point Security Management Server, verify that the credentials used to integrate the CloudGuard Controller with Cisco APIC allow device package uploads.
-
In SmartConsole, add APIC as a Data Center server object to the R80.40 Security Management Server.
To learn more, see the R80.40 CloudGuard Controller Administration Guide.
-
Connect to the Security Management Server through CLI.
-
From clish, run the
vsec_configutility > Cisco ACI configuration > Install device package.If more than one Cisco APIC Data Center object exists, select the Data Center server which represents the specified Cisco APIC server.
In a Multi-Domain deployment, use the domain context to upload the package.
-
Make sure the device package is successfully installed on the Cisco APIC.
-
From a browser, connect to the Cisco APIC server.
-
Go to L4-L7 services > Packages.
-
Note- For Multi-Domain Server High Availability, execute the command in a Multi-Domain context.
Adding an L4-L7 Device
When you configure a new device, it must be part of a domain that assigns dynamic VLANs.
Note- When you change the password for a device, the password for the concrete device under the main device does not change automatically.
To add an L4-L7 device:
-
In the APIC server web UI, select the designated tenant:
L4-L7 Services > L4-L7 Devices > Actions > Create L4-L7 devices.
-
Configure the properties in the table below.
-
Click Next > Finish, to confirm the creation of the L4-L7 Check Point device.
Property
Action
Property
Action
General
Managed
Make sure this option is selected.
Name
Use the exact Security Gateway/VSX object name you created in SmartConsole.
Service Type
Select Firewall.
Device Type
Select Physical for a Check Point appliance or Virtual for CloudGuard VE.
Domain
Select the physical or VMM domain where the Security Gateway/VSX Gateway is deployed.
Mode
Select Single node for a single Security Gateway.
Select HA cluster for a solution based on VSX Cluster/VSX Gateway.
Device Package
Select Gateway Device Package from the drop down list.
Model
Select the relevant model for all Check Point appliances:
-
CloudGuard-Virtual - For VSX Gateway or Security Gateway that use CloudGuard
-
Check Point 5400 - The 5400 appliance model
-
Check Point 5600 - The 5600 appliance model
-
Check Point 5800 - The 5800 appliance model
-
Check Point 15400 - The 15400 appliance model
-
Check Point 15600 - The 15600 appliance model
-
Check Point 23500 - The 23500 appliance model
-
Check Point 23800 - The 23800 appliance model
-
Check Point 4400 - The 4400 appliance model
-
Check Point 4600 - The 4600 appliance model
-
Check Point 4800 - The 4800 appliance model
-
Check Point 12200 - The 12200 appliance model
-
Check Point 12400- The 12400 appliance model
-
Check Point 12600 - The 12600 appliance model
-
Check Point 13500 - The 13500 appliance model
-
Check Point 13800 - The 13800 appliance model
-
Unknown - For other platforms (open server)
Function Type
Select GoTo for routed (L3) Mode use case, including PBR.
Select GoThrough for transparent (L2) mode use case.
Connectivity
APIC to Device Management Connectivity
Configure based on environment design.
Best practice -Use Out Of Band connectivity for management connections.
Credentials
Username
Enter the username provided in the
vsec_configwizard.Password
Enter the user password.
Device 1 (and Device 2 when a High Availability cluster is selected)
Management IP address
Enter the IP address of the Check Point Security Management Server.
For Management High Availability, use the primary server IP address.
Note - Devices are managed through IPv4. IPv6 is not supported for management connectivity to the device.
Management Port
Select https.
VM
(Relevant to virtual device types only).
Select the CloudGuard VE VM used to inspect the traffic.
Chassis
(Leave blank)
Device Interfaces
Physical domain:
-
Name - From the drop down list, select the interface name of the appliance. For bond or extension interfaces, manually enter the interface name as shown in the Gaia interfaces list.
-
Path - Select the leaf ports to where the interfaces are connected.
Virtual domain:
-
Name - Select the interface name of the appliance from the drop down list.
-
vNIC- Select the vNIC mapped to the interface.
-
Path Use this for route peering only. Select the leaf ports to where the interfaces are connected.
Note - Mapping of the Name and vNIC must be verified on the CloudGuard VE VM. For example, there is no guarantee that
eth0is mapped to Virtual adapter 1.Cluster
Management IP address
Enter the Check Point Security Management Server IP address.
For Management High Availability, use the primary server IP address.
Management Port
Select https.
Device Manager
For Management High Availability, select the device manager you configured. For more information, see Configuring Management High Availability Integration.
For others, leave blank.
Cluster Interfaces
Physical device:
-
Type -Select Consumer or Provider topology.
-
Name - For Consumer, enter consumer. For Provider, enter provider.
-
Concrete interfaces - Select the applicable appliance interface name.
Virtual device:
-
Type-Select Consumer, Provider, or Consumer and Provider based on the topology.
-
Name Enter the name of the interface.
-
Concrete interfaces - Select the applicable VM interface name.
-
Configuring a Service Bridge Domain - PBR Deployment Only
A service BD is a bridge domain that the L4-L7 device connects to (either the Check Point VSX or Security Gateway).
-
Create a new Bridge Domain.
-
Configure the Bridge Domain.
-
Create a subnet. The IP address of the firewall interface is on this subnet.
-
Clear Enable the Learning of the Source VTEP on Remote Leafs.
-
Set L2 Unknown Unicast to Flood.
-
Verify that the BD is configured as a regular BD and not a Legacy.
-
Creating an L4-L7 Service Graph Template
To create an L4-L7 Service Graph template:
-
In the APIC server web UI, select the designated tenant: L4-L7 Services > L4-L7 Service Graph Templates > ACTIONS > Create L4-L7 Service Graph Template.
-
Create a Service node - Drag and drop the CloudGuard device from the device cluster table to the work pane.
-
Configure the properties in the table below.
-
Click SUBMIT.
Property
Action
Graph Name
Enter the graph name.
Graph Type
Select a graph creation option:
-
Create A New One
-
Clone An Existing One
If you select Clone An Existing One enter the graph template.
Type
Select the graph type based on the design considerations:
-
Transparent Mode - for L2.
-
Routed Mode - for L3 and PBR. Select the Route Redirect checkbox for PBR deployments.
Profile
Select the default profile based on the graph type you choose:
-
NGFW_L2 for L2 deployments
-
NGFW_L3 for L3 deployments
-
NGFW_PBR for PBR deployments
-
Configuring L4-L7 PBR Policy - PBR Deployment Only
To configure PBR policy with the APIC GUI:
-
In the Navigation window, select Tenant tenant_name > Networking > Protocol Policies > L4-L7 Policy Based Routing.
-
In the Work window, select Action > Create L4-L7 Policy Based Routing.
-
In the Create L4-L7 Policy Based Routing window, add the cluster interface that will be associated with the service BD, as the destination. For MAC, use the VMAC.
Use this policy when you apply the L4-L7 service graph template.
Note - For N9K-93128TX, N9K-9396PX, N9K-9396TX, N9K-9372PX, and N9K-9372TX switches, the service appliance must not be in the same leaf switch as the source or destination endpoint group.
For N9K-C93180YC-EX and N9K-93108TC-EX switches, the service appliance can be in the same leaf switch as the source or destination endpoint group.
Applying the Service Graph to a Contract
You can apply a service graph that describes a Check Point L4-L7 device insertion. A Virtual System is created automatically or an existing Virtual System is added with interfaces and routes based on configured parameters.
For a directly connected (general) insertion, any new interface that you configure for the device is automatically added to the Virtual System. An interface that you configure connects it to the bridge domain that contains the EPG.
Notes:
Directly connected (L2 adjacency) insertion requires that you enable ARP Flooding on the bridge domains connected to the L4-L7 device.
When you use a virtual device in a cluster configuration with VMAC enabled, make sure that Promiscuous Mode is enabled on the shadow port group. It is created by the APIC after the service graph is applied.
To apply the service graph to a contract:
-
In the APIC server web UI, select the designated tenant: L4-L7 Services > L4-L7 Service Graph Templates.
-
Right click on the service graph you want to apply, and select Apply L4-L7 Service Graph Template.
-
Enter the EPGs information and contract information.
-
Click Next and configure the consumer, provider, and route.
-
Click Next and select the All Parameters tab.
-
Enter the device parameters to start the insertion.
-
Click Finish.
EPGs and Contract Information
|
Property |
Action |
|---|---|
|
EPGs Information |
|
|
Consumer EPG/External Network |
Select the consumer EPG name or the external network name. |
|
Provider EPG/External Network |
Select the provider EPG name or external network name. |
|
Contract Information |
|
|
Contract |
Select a contract option:
|
|
Contract Name (For a new contract only). |
Enter the contract name. |
|
No Filter (For a new contract only). |
If No Filter is checked, the contract applies to all traffic types and security is enforced only based on the Check Point security policy installed on the device. If No Filter is cleared, the Filter Entries table opens and shows the ACI filters you can add before Check Point inspection. Note - For PBR, a contract must have filters that only match IP traffic. |
|
Existing Contracts with Subject |
The contract subject name. |
Consumer, Provider and Route Configurations
|
Property |
Action |
|---|---|
|
Graph Template |
Verify the graph template name. |
|
Consumer Connector |
General - Use this to configure a directly connected service insertion, L2 adjacency or PBR. In this mode, the routed or transparent service interface is connected directly to the BD you choose. For PBR it is a service BD and for L2 adjacency, it is an endpoint BD. In General Mode, configure the BD that is connected to the device on the consumer interface, and select Cluster Interface consumer. Virtual Deployment Select the corresponding interface name. Route Peering - Use Route Peering to configure route peering, L3 out, and service insertion. In this mode, the device learns networks through static or dynamic routing, and traffic is steered to the device through the external L3 network. In Route Peering Mode, configure the L3 external network connected to the device on the consumer interface. Select Cluster Interface consumer. Redirect Policy (for PBR only) - Select the PBR redirect policy you created. |
|
Provider Connector |
General -Use this to configure a directly connected service insertion, L2 adjacency or PBR. In this mode, the routed or transparent service interface is connected directly to the BD you choose. For PBR it is a service BD and for L2 adjacency, it is an endpoint BD. In General mode, configure the BD connected to the device on the provider interface and select Cluster Interface provider. Virtual Deployment - Select the corresponding interface name. Route Peering - Use Route Peering to configure route peering, L3 out, and service insertion. In this mode, the device learns networks through static or dynamic routing and traffic is steered to the device through the external L3 network. In Route Peering mode, configure the L3 external network connected to the device on the provider interface. Select Cluster Interface provider. Redirect Policy (for PBR only) - Select the PBR redirect policy you created. |
|
Routing Config (Route Peering only). |
Select:
|
Device Parameters
|
Parameter |
Function |
|---|---|
|
IPv4 Consumer Facing Address IPv4 Provider Facing Address |
Configures the network interfaces, IPv4 address, and prefix for the consumer and provider interfaces. Use this format:
|
|
IPv6 Consumer Facing Address IPv6 Provider Facing Address |
Configures the network interfaces, IPv6 address, and prefix for the consumer and provider interfaces. You can write the IPv6 address in its abbreviated form. For example, 20a1:0db8::0001/112 Note - A prerequisite for using an IPv6 address is enabling IPv6 support on the relevant Virtual System or Security Gateway. See sk39374. |
|
Instance Name |
Use this for instantiation of a new Virtual System on the VSX gateway. If an instance that runs the required policy already exists on the device, the existing instance is modified and a new instance is not created. To create a new instance, assign it a specific name. |
|
Security Domain |
Required for Multi-Domain Server deployment. The default is no MDM. Specifies the domain server name that contains the device. |
|
Security Policy Name |
Determines the policy package that is installed on the security instance. The policy package must exist on the Security Management Server. |
|
Route Entry |
Static routes are added to the VS routing table. Multiple routing entries may be added. Static route entries include:
Note - To set a default static route, use 0.0.0.0/0 in the Destination Address field. |
Device Parameters for PBR
|
Parameter |
Function |
|---|---|
|
Firewall Interface Address |
Configures the IP address (CIDR notation) for the firewall interface. Put it in the same subnet you define on the service BD.
|
|
Instance Name |
Use this for instantiation of a new Virtual System on the VSX gateway. If an instance that runs the required policy already exists on the device, the existing instance is modified and a new instance is not created. To create a new instance, assign it a specific name. |
|
Security Domain |
Required for Multi-Domain Server deployment. The default is no MDM. Specifies the domain server name that contains the device. |
|
Security Policy Name |
Determines the policy package that is installed on the security instance. The policy package must exist on the Security Management Server. |
|
Service-BD Gateway Address |
IP address of the gateway defined for the service BD. |
Configuring Management High Availability Integration
To configure Management High Availability integration, you must create a Device Manager:
-
In the APIC server WebUI, L4-L7 tab, Inventory section, select Device Manager Types > ACTIONS > Create Device Manager Type.
-
For these parameters, enter the information as it shows on the Check Point L4-L7 Service Device.
-
Vendor
-
Model
-
Version
-
-
For L4-L7 Service Device Type, select Check Point L4-L7 Service Device.
-
In the APIC server web UI, select the designated tenant > L4-L7 Services > Device Managers > ACTIONS > Create Device Manager.
-
For Device Manager Name, enter as it appears on Check Point L4-L7 Service Device.
-
For Device Manager Type, select the Device Manager Type from Step 1.
-
For Management, in the table, enter the Management details:
-
Host - Management IP
-
Port - Management Port (443)
-
-
Enter the Management Username and Password. These credentials were set with the
vsec_configcommand and are the same as the ones used in Adding an L4-L7 Device. -
Confirm the password.
Note -Only Management High Availability with two devices is supported.
-
Follow the instructions to create an L4-L7 device.
Note -The Management IP address defined in Adding an L4-L7 Device is treated as the primary management.
-
Use the Check Point Administration Guide to continue with the Management High Availability settings.
Configuring Multi-Domain Server Integration
The Cisco ACI solution is VSX based. You can select the domain that holds and manages the Virtual Systems. You must configure the domain in the Service Parameters to integrate the solution with the Check Point Multi-Domain Server.
To configure the domain in the Service Parameters:
-
Install the Multi-Domain Server.
-
When you configure Service Parameters, select the domain that is used to host the applicable Virtual System object.
Note - The domain name is part of the Virtual System object name that is provisioned by APIC.
Removing Service Insertion
Before you remove a tenant, we recommend that you remove all service graphs from the contracts. APIC removes tenants by best effort, which can leave configuration and constructs (such as service graphs) in the tenant that you would have removed.
When you remove a service graph used to insert a Check Point device, interfaces and routes configured by APIC on the inserted Virtual System are also removed. When you remove all service graphs attachments that render a specific Virtual System, that Virtual System is also removed entirely, including from the Security Management Server.
To remove Service Insertion:
-
In the APIC server web UI, click Select the designated tenant > Security Policies > Contracts.
-
Select the contract between the EPGs in which the service is currently inserted.
-
Select the subject with the Service Graph of the relevant L4-L7 Device.
-
Remove the Service Graph.
Removing L4-L7 Managed Devices
To remove L4-L7 managed devices:
-
Remove all service insertions related to the L4-L7 device you want to remove. See Removing Service Insertion above.
-
In the APIC server web UI, select the designated tenant > L4-L7 Services.
Note -Make sure that there are no entries that are related to the L4-L7 device you want to remove in the Deployed Devices section and in the Deployed Graph Instances sections.
-
In the APIC server web UI, select the designated tenant > L4-L7 Services > Device Selection Policies, and remove all the entries related to the L4-L7 device.
-
In the APIC server web UI, select the designated tenant > L4-L7 Service Parameters, and remove all the entries that use the Graph Templates that use the L4-L7 device.
-
In the APIC server web UI, select the designated tenant > L4-L7 Services > L4-L7 Service Graph Templates, and remove all the Graph Templates that use the L4-L7 device.
-
In the APIC server web UI, select the designated tenant > L4-L7 Services > L4-L7 Devices, and delete the device.
Configuring Dynamic Routing - OSPF
To use OSPF route protocol in outside connections:
-
Create an L3 outside connection with OSPF configuration.
Note - To adjust the configuration to work with Check Point gateways, see the Gaia Advanced Routing Administration Guide.
-
Connect the L3 outside connection to apply the service graph.