Check Point CloudGuard Network for AWS
Check Point CloudGuard for AWS![]() Amazon® Web Services. Public cloud platform that offers global compute, storage, database, application and other cloud services. easily extends comprehensive Threat Prevention security to the AWS cloud and protects assets in the cloud from attacks, and at the same time enables secure connectivity.
Amazon® Web Services. Public cloud platform that offers global compute, storage, database, application and other cloud services. easily extends comprehensive Threat Prevention security to the AWS cloud and protects assets in the cloud from attacks, and at the same time enables secure connectivity.
Use CloudGuard Network to enforce consistent Security Policies![]() Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. across your entire organization. It protects data between the corporate network and the Amazon VPC. CloudGuard Network inspects data that enters and leaves the private subnet in the Amazon VPC to prevent attacks and mitigate data loss or leakage. CloudGuard Network protects services in the public cloud from the most sophisticated threats, unapproved access, and prevents application layer Denial of Service (DoS) attacks.
Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. across your entire organization. It protects data between the corporate network and the Amazon VPC. CloudGuard Network inspects data that enters and leaves the private subnet in the Amazon VPC to prevent attacks and mitigate data loss or leakage. CloudGuard Network protects services in the public cloud from the most sophisticated threats, unapproved access, and prevents application layer Denial of Service (DoS) attacks.
Check Point CloudGuard for AWS meets organizational cloud security needs:
-
Automatically deployed tags-based IPsec VPN between AWS Transit Gateway and the security VPC.
-
Automatic configuration of AWS VPN Gateways on spoke VPCs. This includes planning of IP addresses to prevent subnet IP address conflicts.
-
Next Generation Firewall with Application Control
 Check Point Software Blade on a Security Gateway that allows granular control over specific web-enabled applications by using deep packet inspection. Acronym: APPI., Data Awareness, HTTPS Inspection
Check Point Software Blade on a Security Gateway that allows granular control over specific web-enabled applications by using deep packet inspection. Acronym: APPI., Data Awareness, HTTPS Inspection Feature on a Security Gateway that inspects traffic encrypted by the Secure Sockets Layer (SSL) protocol for malware or suspicious patterns. Synonym: SSL Inspection. Acronyms: HTTPSI, HTTPSi., NAT, and logging.
Feature on a Security Gateway that inspects traffic encrypted by the Secure Sockets Layer (SSL) protocol for malware or suspicious patterns. Synonym: SSL Inspection. Acronyms: HTTPSI, HTTPSi., NAT, and logging. -
IPS
 Check Point Software Blade on a Security Gateway that inspects and analyzes packets and data for numerous types of risks (Intrusion Prevention System). and virtual patching of cloud resources.
Check Point Software Blade on a Security Gateway that inspects and analyzes packets and data for numerous types of risks (Intrusion Prevention System). and virtual patching of cloud resources. -
URL Filtering
 Check Point Software Blade on a Security Gateway that allows granular control over which web sites can be accessed by a given group of users, computers or networks. Acronym: URLF. for Internet-bound traffic.
Check Point Software Blade on a Security Gateway that allows granular control over which web sites can be accessed by a given group of users, computers or networks. Acronym: URLF. for Internet-bound traffic. -
Anti-Bot
 Check Point Software Blade on a Security Gateway that blocks botnet behavior and communication to Command and Control (C&C) centers. Acronyms: AB, ABOT. and Anti-Virus
Check Point Software Blade on a Security Gateway that blocks botnet behavior and communication to Command and Control (C&C) centers. Acronyms: AB, ABOT. and Anti-Virus Check Point Software Blade on a Security Gateway that uses real-time virus signatures and anomaly-based protections from ThreatCloud to detect and block malware at the Security Gateway before users are affected. Acronym: AV., and Zero-day Threat Emulation
Check Point Software Blade on a Security Gateway that uses real-time virus signatures and anomaly-based protections from ThreatCloud to detect and block malware at the Security Gateway before users are affected. Acronym: AV., and Zero-day Threat Emulation Check Point Software Blade on a Security Gateway that monitors the behavior of files in a sandbox to determine whether or not they are malicious. Acronym: TE. and Threat Extraction
Check Point Software Blade on a Security Gateway that monitors the behavior of files in a sandbox to determine whether or not they are malicious. Acronym: TE. and Threat Extraction Check Point Software Blade on a Security Gateway that removes malicious content from files. Acronym: TEX..
Check Point Software Blade on a Security Gateway that removes malicious content from files. Acronym: TEX.. -
IPsec VPN for VPC-to-VPC, and VPC-to-on-premises connections with optional Direct Connect support.
-
High Availability deployment.
-
Automated solution deployment with CloudFormation.
|
|
Note - For the list of supported versions, refer to the Support Life Cycle Policy. |
Costs and Licenses
You are responsible for the cost of the AWS services that you use, when you deploy the solution described in this guide.
The AWS CloudFormation template for the Security VPC includes parameters that you can configure. Some of these settings, such as instance type have an effect on the cost of deployment. For estimated costs, see the AWS pricing calculator.
This Transit VPC - Transit Gateway solution uses Amazon Machine Images (AMIs) from the AWS Marketplace. You must subscribe to Check Point CloudGuard in the AWS Marketplace before you start the deployment.
Check Point CloudGuard Security Gateways, Check Point CloudGuard Security Management Server![]() Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server., and AWS CloudFormation templates described in this guide must have a license. There are two licensing options:
Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server., and AWS CloudFormation templates described in this guide must have a license. There are two licensing options:
-
Pay As You Go (PAYG)
-
Bring Your Own License (BYOL)
To buy BYOL licenses, contact Check Point Sales.
Prerequisites
Before you use this solution, make sure you read the AWS terms and services:
-
Amazon EC2
-
Amazon VPC
-
AWS CloudFormation
-
AWS IAM
-
AWS Transit Gateway
If you are new to AWS, see Getting Started with AWS.
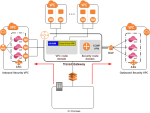
Architecture
The diagram shows Transit Gateway architecture for Check Point CloudGuard AWS.
an end-to-end solution, which includes:
-
AWS Transit Gateway (TGW) object.
-
Spoke (Consumer) VPCs attached to the AWS Transit Gateway.
-
Outbound Security VPC with the CloudGuard Transit Gateways Auto Scaling Group.
-
Automatic provisioning of VPN tunnels.
-
BGP routing configuration between the AWS Transit Gateway and the CloudGuard Network Security Gateways.
-
Inbound Security VPC with CloudGuard Security Gateways Auto Scaling Group attached to the AWS Transit Gateway.
-
Corporate VPN between on-premises perimeter and the AWS Transit Gateway.
Note - Red arrows show the provisioning flow from an on-premises Management Server![]() Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server..
Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server..
A Transit Gateway functions as a regional virtual router for traffic that flows between your Virtual Private Clouds (VPC) and VPN connections. A Transit Gateway scales elastically based on the volume of network traffic. Routing through a Transit Gateway operates at Layer 3, where the packets are sent to a specific next-hop attachment, based on their destination IP addresses.
Use Cases
| Architecture | Description |
|---|---|
|
Transparent proxy |
The transparent proxy provides secured proxy services to the spoke VPCs. It is transparent in that the security proxy services are seamless and do not need topological changes to the protected spoke VPCs. With this solution, it is not necessary to have a CloudGuard Gateway for AWS in each of the spoke VPCs. The solution relies on VPN connections to the central (hub) VPC for Internet-bound connections. DevOps and application owners can use the transparent proxy to deploy solutions in designated VPCs, rely on AWS native security controls only, and have advanced Threat Prevention, Next Generation Firewall, and compliance, seamlessly from the central VPC. |
|
Cloud perimeter |
The Transit VPC - Security VPC of the Transit Gateway solution, as a cloud perimeter, provides Threat Prevention and Access Control to the spoke VPCs. Each VPC can be deployed in multiple Availability Zones and provide security services to multiple spoke VPCs in the environment. Only the central VPC has access to the Internet, and the spokes are limited to private subnets. All traffic to and from the spoke VPCs is steered through the central VPC. The security controls are concentrated in a one central VPC. |
|
Hybrid cloud |
With a Hybrid cloud setup, you can connect your on-premises and cloud environments, and cloud assets can have secured access to on-premises assets. The connection is set up through a secured VPN connection between your Check Point Security Gateway You can also implement a secure connection with AWS Direct Connect tunnels. For example, a front-end server in the cloud can connect to an on-premises backend database to retrieve confidential data or business logic. For more information, see sk120534. |
|
Direct Connect |
Direct Connect makes it easy to establish a dedicated network connection from on-premises to AWS. When you use AWS Direct Connect, it is transparent to Check Point Security Gateways. For example, you can connect route and tunnels from Transit Gateways directly to Corporate Gateways. You must configure the Direct Connect manually, when you connect corporate gateways and Transit Gateways. Automation is not supported. For more information, see sk120534. |
VPN Community
A VPN Domain is a collection of internal networks that use VPN Security Gateways to send and receive their traffic. VPN Security Gateways are joined into a VPN Community. A VPN Community is a collection of VPN tunnels and their attributes. Networks from different VPN Domains can communicate safely with each other through VPN tunnels that end at the Security Gateways in the VPN communities.
VPN communities used for this Transit solution are based on a Star topology. In a Star VPN Community, each satellite gateway, an AWS VPN connection represented by an Interoperable Device object, has a VPN tunnel to the central CloudGuard Security Gateway, and through it to other satellite gateways in the Star VPN Community.
Transit solution uses Route Based VPN, where VPN traffic is routed based on the BGP routing settings of the CloudGuard Gateway. The CloudGuard Gateway uses a VPN Tunnel Interface (VTI) to send the VPN traffic, as if it were a physical interface.
Because of the Route Based VPN, it is not necessary to set a VPN Domain on the CloudGuard Security Gateway. The Transit service creates an empty Group object that is used when you configure the CloudGuard Gateway in SmartConsole![]() Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on.. This ensures that Domain Based VPN is not used.
Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on.. This ensures that Domain Based VPN is not used.
The config-community.sh script creates a Star VPN Community with these required settings for Transit:
-
Encryption: IKE Security Association Phase 2 enabled, set to Group 2 (1024 bit)
-
Tunnel management: One VPN tunnel for each gateway pair enabled
-
Shared Secret: Use only Shared Secret for all external members enabled
-
Advanced: IKE (Phase 1) set to 480
For information on this script, see Configuring the VPN Community with the 'config-community.sh' Script.
For more information about Check Point VPN solutions, see the Site to Site VPN Administration Guide for your specific version.
Security Policy
A Security Policy package is a collection of different types of policies that are enforced after you install the policy on the Security Gateways.
A policy package can have one or more of these policy types:
-
Access Control
-
Desktop Security
-
Threat Prevention
The Standard policy package is the default Security Policy defined in a newly deployed Security Management Server. Each policy package has a default cleanup rule![]() Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. that drops all traffic.
Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. that drops all traffic.
When you configure the Check Point Security Management Server with the autoprov_cfg utility, specify the name of the Security Policy package to be installed on the Transit Gateways with the "-po" parameter. For the default Security Policy, use the value "Standard" (a capital "S" is required), for this parameter.
If you want to configure more policy packages and install a different policy package on the Security Gateways deployed for the transit solution, then specify the name that you want to give that policy package when you run autoprov_cfg. Afterward, create and configure the policy by connecting to your Security Management Server with SmartConsole.
For more information, see Configuring the Security Management Server with the 'autoprov_cfg' Utility.