Installing Desktop Security Policy
To install the Desktop Security policy (for -managed VPN only):
-
Click Install Policy.
-
In the Install Policy window, select Desktop Security for the Endpoint Security VPN gateway.
If this column is not available, you did not configure the Policy Server. This is necessary. See Configuring a Policy Server.
-
Click OK.
When clients download the new policy from the gateway, configuration changes are applied.
The Desktop Firewall
Endpoint Security VPN enforces a Desktop Security Policy on remote clients. You configure the Desktop Security Policy in a Rule Base. Rules can be assigned to specific user groups, to customize a policy.
|
|
Important - Before you start to create a Desktop Security Policy, you must enable the Policy Server feature on the gateway. |
Endpoint Security VPN downloads the first policy from the gateway. It looks for and downloads new policies each time it connects or authenticates.
When Endpoint Security VPN makes a VPN connection, it connects to the gateway and downloads its policy. Endpoint Security VPN enforces the policy: accepts, encrypts, or drops connections, depending on their source, destination, and service.
|
# |
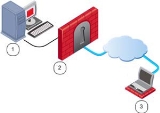
Endpoint Security VPN Desktop Policy Architecture |
|
|---|---|---|
|
1 |
Security Management Server |
Manages all policies |
|
2 |
Gateway |
LAN Firewall, holds Desktop Security Policy and TTM configuration |
|
3 |
Endpoint Security VPN client |
Gets Desktop Security Policy from the gateway and enforces policy on the client's computer. |
Rules
The Desktop Security Policy has Inbound and Outbound rules.
-
Inbound rules - enforced on connections going to the client's computer.
-
Outbound rules - enforced on connections originating from the client's computer.
Each rule calculates traffic by source, destination, and service. The rule specifies what action to take on matching traffic.
-
Source: The network object which initiates the communication.
-
Destination: The user group and location for Inbound communications, or the IP address of Outbound communications.
-
Service: The service or protocol of the communication.
-
Action: Accept, Encrypt, or Block.
Implied Rules
The Desktop Security Policy has implicit rules appended to the end of inbound and outbound policies.
-
The implicit outbound rule allows all connections originating from the client to go out, if they do not match earlier blocking rules:
Any Destination, Any Service = Accept -
The implicit inbound rule blocks all connections coming to the client that do not match earlier rules.
Any Source, Any Service = Block
User Granularity
You can configure different rules for remote users based on locations and user groups.
-
Locations - Set rules to be implemented by physical location. For example, a user with a laptop in the office building has a less restrictive policy than when the same user on the same laptop connects from a public wireless access point.
-
User Groups - Set rules to be implemented for some users and not others. For example, configure restrictive rules for most users, but give system administrators more access privileges.
Rules are applied to user groups, not individual users. Endpoint Security VPN does not inherently identify user groups, so it must get group definitions from the gateway. The gateway resolves the user groups of the authenticated user and sends this information to the Endpoint Security VPN client. Endpoint Security VPN enforces the rules applicable to the user based on groups.
In addition, rules can be applied to radius groups on the RADIUS server.
Default Policy
If an Endpoint Security VPN client is disconnected from the gateway, the client enforces a default policy. This policy is enforced until Endpoint Security VPN connects to the gateway and enforces an updated personalized policy.
The default policy is taken from the last Desktop Firewall policy that was downloaded from the gateway. It includes the rules that apply to the All Users group. Rules from the Desktop Firewall policy that apply to other groups or users are not part of the default policy.
Logs and Alerts
Desktop Security log messages are saved locally on the client's computer in the /Library/Application Support/Checkpoint/Endpoint Connect/trac_fwpktlog.log file.
Wireless Hotspot/Hotel Registration
A wireless hotspot is a wireless broadband Internet access service available at public locations such as airport lounges, coffee shops, and hotels.
The user launches a web browser and attempts to connect to the Internet. The browser is automatically redirected by the hotspot server to the Hotspot welcome page for registration. In the registration process, the user enters the required information. When registered, the user gains access to the Internet.
This feature supports users with restrictive outbound policies or with Hub Mode (everything goes through the Security Gateway), or both. Therefore, even if users connect to a gateway for all Internet communication, they can continue to access the hotspot to register.
A proxy may be required.
Planning Desktop Security Policy
Balance considerations of security and convenience. A policy must let desktop users to work as freely as possible, and to decrease the threat of attack from malicious third parties.
-
In the Inbound policy, allow only services that connect to a specific server running on the applicable port.
-
In the Outbound policy, use rules to block only specific problematic services (such as Netbus) and allow all others.
-
Remember: Implied rules may allow or block services not explicitly managed by earlier rules. For example, if the user runs an FTP server, the inbound rules must explicitly allow connections to the FTP server.
Operations on the Rule Base
Configure the Desktop Security Policy. Rules are managed in order, what is blocked by an earlier rule cannot be allowed afterwards. The right-click menu of the Rule Base is:
-
Add - Add a rule above or below the selected rule.
-
Disable - Rules that are currently not implemented, but may be in the future, can be disabled.
-
Delete - Delete rules which are no longer necessary.
-
Hide - Hide rules that are irrelevant to your current view, to enhance the readability of your Rule Base. Hidden rules are contiune to be applied.
-
Where Used - See where the selected network object is included in other rules.
-
Show - Show the selected object or rule in SmartMap.
Letting Users Disable the Firewall
You can configure if Endpoint Security VPN users can select to disable the firewall policy on their local computers.
If this option is enabled, when users right-click the Endpoint Security VPN icon, they can select Disable Security Policy.
To change the Allow disable firewall setting:
-
On the gateway, open the
$FWDIR/conf/trac_client_1.ttmfile with a text editor. -
Find the line
:allow_disable_firewalland set the value:-
true - Users can disable their firewall policy.
-
false - Users do not have the option to disable their firewall policy.
-
client_decide - Takes the value from a file on the client's computer.
-
-
Save the file and install the policy.