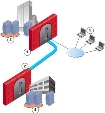
Encryption Domains
Example architecture setups of an encryption domain.
Scenario 1 Dedicated Encryption Domain
|
# |
Component |
Connects To |
|---|---|---|
|
1 |
Gateway of Site 1 |
|
|
2 |
Gateway of Site 2 |
Gateway of Site 1 in site-to-site VPN |
|
3 |
Servers in Remote Access Encryption Domain |
Servers in the Encryption Domain of Site 2 |
|
4 |
Servers in Remote Access Encryption Domain |
Servers in the Encryption Domain of Site 1 |
|
5 |
Endpoint Security VPN |
|
Scenario 2 Access to External Encryption Domain
|
# |
Component |
Connects To |
|---|---|---|
|
1 |
Gateway of Site 1 |
|
|
2 |
Gateway of Site 2 |
Gateway of Site 1 in site-to-site VPN |
|
3 |
Servers in Remote Access Encryption Domain |
Servers in the Encryption Domain of Site 2 |
|
4 |
Servers in Remote Access Encryption Domain |
Servers in the Encryption Domain of Site 1 |
|
5 |
Endpoint Security VPN |
|