Users that Received Malicious Emails (Attacks Allowed By Policy)
Description
In the main Cyber Attack View, in the Attacks Allowed By Policy section, double-click Users that Received Malicious Emails.
Note - Select the desired report period in the top left corner of this view. For example, Last 7 Days, This Month, and so on.
The email vector is the common vector used to deliver a malicious payload.
This drill-down view shows a summary of email attack attempts.
The IPS, Anti-Virus, Threat Emulation and Threat ExtractionSoftware Blades work in parallel to determine if an email is malicious and provide multi-layer protection.
Drill-Down View
This is an obfuscated example of the drill-down view:
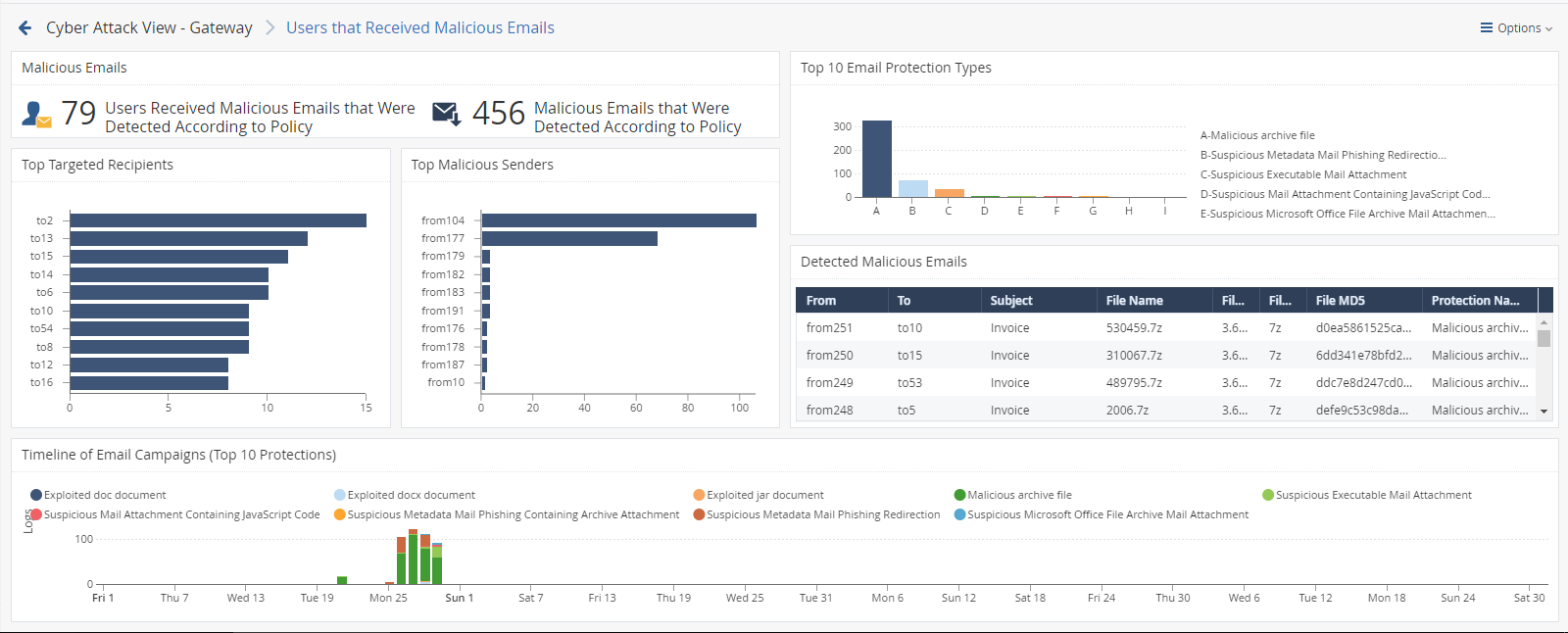
To see the applicable logs (the next drill-down level), double-click a value.
Available Widgets
Widgets available in the drill-down view:
|
Widget |
Type |
Description |
|---|---|---|
|
Malicious Emails |
Infographic |
Shows the total number of emails with content that the Security Gateway found as malicious. |
|
Top 10 Email Protection Types |
Chart |
Shows top Check Point protections that found malicious emails. Shows:
Different colors show different protection types. |
|
Top Targeted Recipients |
Chart |
Shows the recipients of malicious emails sorted by the number of emails they received. Shows:
Different colors show different recipients. |
|
Top Malicious Senders |
Chart |
Shows the senders of malicious emails sorted by the number of emails they sent. Shows:
Different colors show different senders. |
|
Detected Malicious Emails |
Table |
Shows malicious emails. Shows this information about the detected malicious emails:
|
|
Timeline of Email Campaigns (Top 10 Protections) |
Timeline |
Shows the number of detected malicious emails and their timeline. The timeline is divided into different protection types. Different colors show different campaigns. |
Widget Query
In addition to the Default Query, the widget runs this query:
|
|
|
|
Best Practices
Best practices against malicious emails:
-
Examine the Detected Malicious Emails to see the number of emails with malicious content that the current Security Policydetected, but did not prevent.
-
Examine the Top 10 Email Protection Types to see the top attack types.
Pay attention to protections configured to work in Detect mode instead of Prevent mode. Fine-tune your email policy accordingly.
-
In the Threat Prevention logs from the Security Gateway, examine the Description field (see Log Fields) to see if the Anti-Virus Software Blade work is in the Background or Hold mode.
To do so, in the Detected Malicious Emails, double-click on one of the counters > open the log > refer to the Description field.
In addition, read sk74120: Why Anti-Bot and Anti-Virus connections may be allowed even in Prevent mode.