MITRE ATT&CK
MITRE ATT&CK is a knowledge base used for the development of threat models and methodologies for the global cybersecurity community.
MITRE ATT&CK lets Check Point customers review the security incidents in their network in a way that exposes the top techniques and tactics used by attackers against their network.
For each malicious file that is found, Threat Emulation (SandBlast technology) adds the techniques and tactics that were used in the attack to the relevant log.

|
Note - The Threat Emulation blade must be enabled if you want to add MITRE ATT&CK information to the logs. |
Configuring Threat Emulation Logs with MITRE ATT&CK Data
-
Open SmartConsole.
-
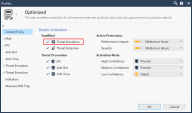
In the Gateways & Servers view, enable the Threat Emulation blade on the relevant Security Gateway.
-
Select the Gateway, click Actions > Open Shell.
-
Run:
tecli advanced version engineThe Threat Emulation engine version must be higher than
58.990001056 -
Open the Threat Prevention profile in use in the Threat Prevention policy, for example Optimized, and make sure the Threat Emulation blade is activated.
MITRE Logs
To view logs with the added MITRE data:
-
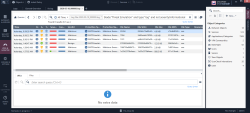
In the Logs & Monitor view, open the Logs tab.
-
In the search box, enter this query to find malicious files found by Threat Emulation:
Blade:”threat Emulation” AND type:”log” AND NOT severity: “informational” -
Open one of the logs.
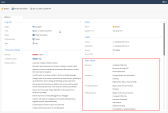
The log shows the MITRE ATT&CK Techniques and Tactics used in the specific attack. The log may show multiple actions such as execution and persistence. For more on each technique as well as mitigation advice, visit the MITRE ATT&CK web site.
MITRE ATT&CK Best Practices
Adding MITRE ATT&CK data to your logs lets you:
-
Understand your unique attack landscape
Focus on the top techniques used by your attackers. By gaining a high level view of your attackers intent, you can identity attack trends against your network.
Use MITRE ATT&CK to verify that your Threat Prevention policy is protecting your network against all types of tactics and techniques.
Review the Check Point Infinity Security Portfolio mapped to the MITRE ATT&CK Enterprise matrix.
-
Take action according to your attacker's intent
Review the mitigation options offered by MITRE. These mitigation options are related to the specific type of attack launched against your network.