Hosts that Downloaded Malicious Files (Prevented Attacks)
Description
In the main Cyber Attack View, in the Prevented Attacks section, double-click Hosts that Downloaded Malicious Files.
Note - Select the desired report period in the top left corner of this view. For example, Last 7 Days, This Month, and so on.
This drill-down view shows a summary of attacks that used malicious files.
This drill-down view shows all the malicious files caught by Check Point Threat Prevention's multi-layer protections.
Drill-Down View
This is an obfuscated example of the drill-down view:
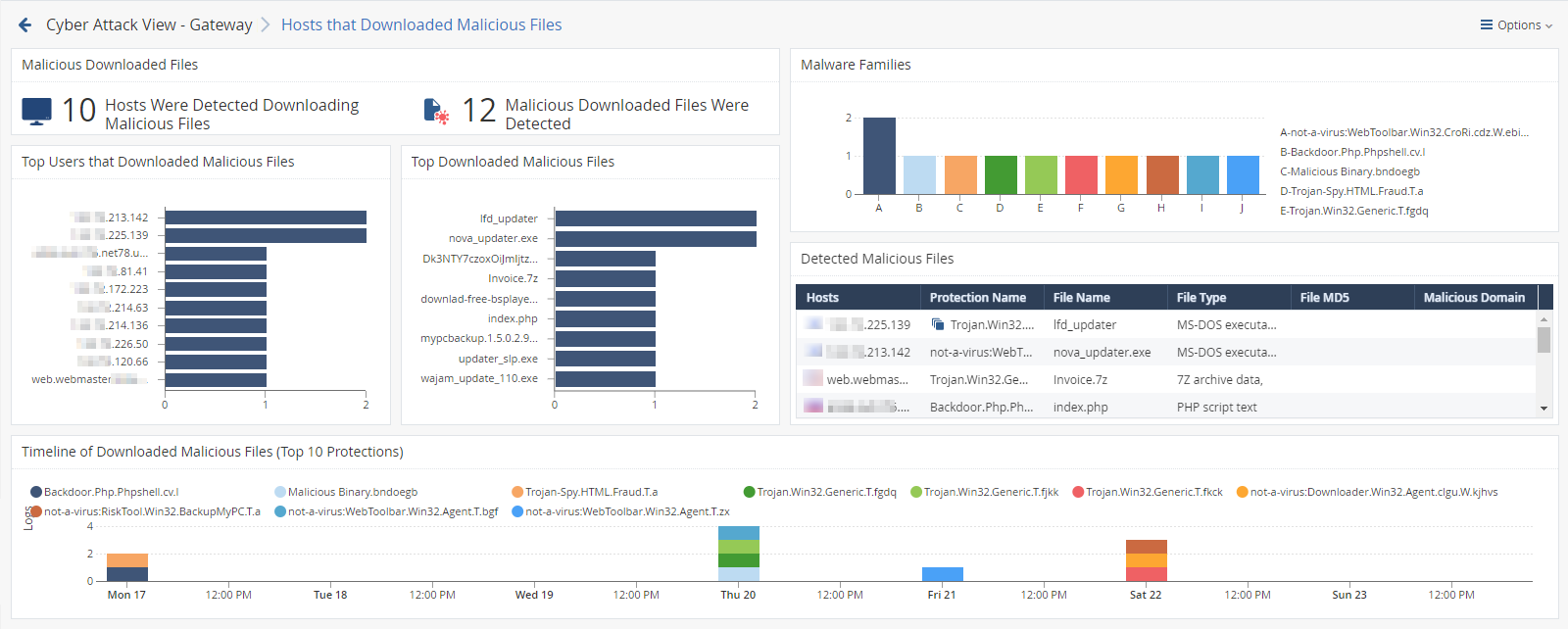
To see the applicable logs (the next drill-down level), double-click on a value.
Available Widgets
Widgets available in the drill-down view:
|
Widget |
Type |
Description |
|---|---|---|
|
Malicious Downloaded Files |
Infographic |
Shows:
|
|
Malware Families |
Chart |
Shows the top downloaded malware families (based on Check Point ThreatWiki and Check Point Research). Different colors show different families. |
|
Top Users that Downloaded Malicious Files |
Chart |
Shows hosts that downloaded the largest number of malicious files. The chart is sorted by the number of downloaded malicious files. |
|
Top Downloaded Malicious Files |
Chart |
Shows the number of downloads for the top malicious files. The chart is sorted by the number of appearances of downloaded malicious files. |
|
Detected Malicious Files |
Table |
Shows the downloaded malicious files. Shows:
|
|
Timeline of Downloaded Malicious Files (Top 10 Protections) |
Timeline |
Shows the number of logs for downloaded malicious files. Different colors show different files. |
Widget Query
In addition to the Default Query, the widget runs this query:
|
|
Best Practices
Best practices against malicious files:
-
Examine the Top Downloaded Malicious Files.
If you see a specific malicious file downloaded many times, treat it as attack campaign against your network.
-
Examine the Detected Malicious Files widget.
-
Look for the common malicious domains related to the malicious files. In case a domain appears many times:
-
If this is an unknown website, add this site to your black list (with the URL Filtering blade).
-
If this is a known website, contact the site owner to alert them about a possible attack on their website.
-
If this is your website, investigate the issue and contact Check Point Incident Response Team.
-