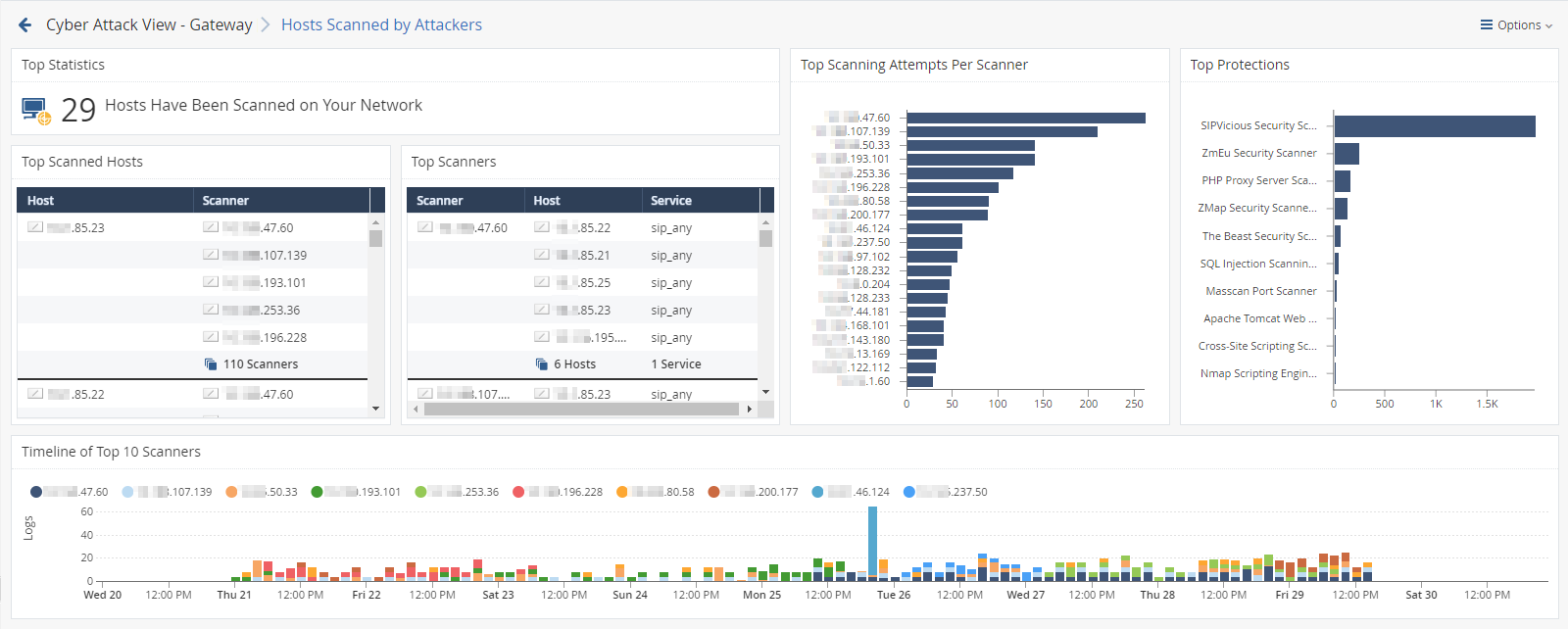
Host Scanned by Attackers (Prevented Attacks)
Description
In the main Cyber Attack View, in the Prevented Attacks section, click Host Scanned by Attackers.
This drill-down view shows the scanned hosts on your internal network.
Network scanners are common. Expect to see many events related to this stage of an attack.
To see the applicable logs (the next drill-down level), double-click on a value.
Available Widgets
Widgets available in the drill-down view:
|
Widget |
Type |
Description |
|---|---|---|
|
Top Statistics |
Infographic |
Shows the number of internal hosts scanned the most. |
|
Top Scanning Attempts Per Scanner |
Chart |
Shows the scanners and the number of their scan attempts. The chart is ordered by the by number of scan attempts. Shows:
|
|
Top Protections |
Chart |
Shows the top protections that reported the scan events. Shows:
|
|
Top Scanned Hosts |
Table |
Shows information about the most scanned internal hosts:
|
|
Top Scanners |
Table |
Shows information about the scanners:
|
|
Timeline of Top 10 Scanners |
Timeline |
Shows the number of scanned hosts for each detected scanner and their timeline. Different colors show different scanners. |
Widget Query
In addition to the Default Query, the widget runs this query:
|
|
Best Practices
Best practices against network reconnaissance attempts:
-
Find the hosts that are able to connect to external networks through the Security Gateway.
Configure the applicable Access Control rules for hosts that you do not want to connect to external networks.
-
If you use your own vulnerability scanner, you have two options:
-
Add an exception to your policy, so that the Security Gateway does not enforce protections against this scanner.
-
If you still want the Security Gateway to report events generated by your scanner, then run an explicit query that excludes your scanner and shows only the external scanners.
-
-
Use logs generated by scanning events to determine if new hosts on the network are connecting to the outside world.