Directly Targeted Hosts (Prevented Attacks)
Description
In the main Cyber Attack View, in the Prevented Attacks section, double-click Directly Targeted Hosts.
Note - Select the desired report period in the top left corner of this view. For example, Last 7 Days, This Month, and so on.
This drill-down view shows a summary of network and hosts exploit attempts.
Host exploit attempts generate the majority of Threat Prevention events.
Drill-Down View
This is an obfuscated example of the drill-down view:
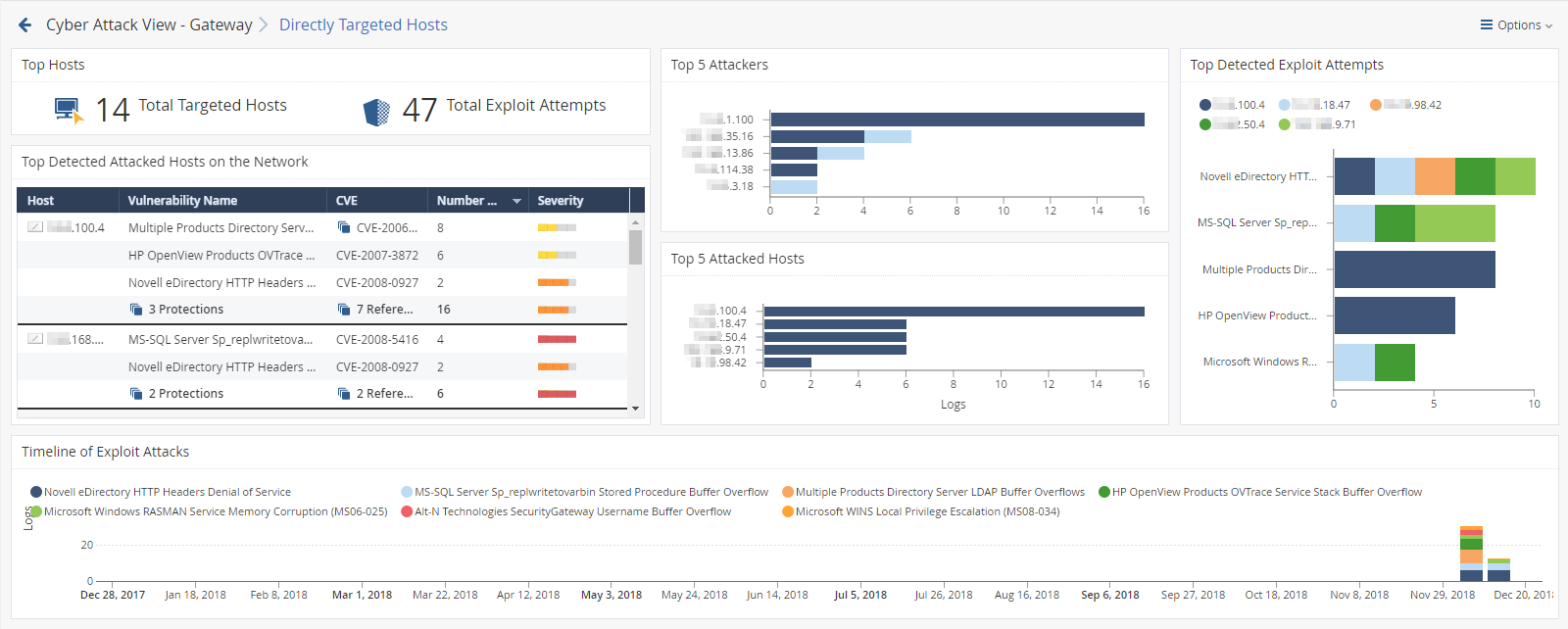
To see the applicable logs (the next drill-down level), double-click on the desired value.
Available Widgets
Widgets available in the drill-down view:
|
Widget |
Type |
Description |
|---|---|---|
|
Top Hosts |
Infographic |
Shows:
|
|
Top 5 Attackers |
Chart |
Shows the top attackers sorted by the number of their exploit attempts. Shows:
Different colors show different exploited vulnerabilities. For more information, see the Top Detected Exploits Attempts widget. |
|
Top 5 Attacked Hosts |
Chart |
Shows the top attacked hosts sorted by the number of attempted exploits. Shows:
|
|
Top Detected Exploit Attempts |
Chart |
Shows the top exploit attempts on internal hosts. Shows:
Different colors show different exploited vulnerabilities. |
|
Top Detected Attacked Hosts on the Network |
Table |
Shows the list of internal hosts and the exploit attempts they encountered. Shows:
|
|
Timeline of Exploit Attacks |
Timeline |
Shows the names of exploited vulnerabilities and their timeline. The timeline is divided into different exploit attempts. Different colors show different exploited vulnerabilities. |
Widget Query
In addition to the Default Query, the widget runs this query:
|
|
Best Practices
Best practices against network and host exploits:
|
Category |
Description |
|---|---|
|
General Best Practices |
|
|
Best Practices for events that the Security Gateway prevented |
|